without headaches
without headaches

the Debian beginner's handbook
– About this manual –
“The beginner’s handbook” is a simplified manual to install and take-over the Debian system.
You will find in the following pages the answers to your first questions concerning the Debian GNU/Linux system  , its history, how to obtain it, to install it, to take-over it, to configure and administrate it.
, its history, how to obtain it, to install it, to take-over it, to configure and administrate it.
You will be able to go further and obtain information concerning the privacy protection, the backing up of your data, and the various actors of the Free Software world.
Usually, the manuals begin by teaching you the theoretical basis and the usage of the terminal. This manual takes the very side of the “graphical environment”: it is designed to let you start quickly with Debian, screen powered on, fingers on the keyboard and the mouse nearby  .
.
– The mission of this manual is not to be comprehensive. –
A lot of external links are available in this manual. Don’t hesitate to click on them in order to read more detailed information.
For a more detailed documentation, please visit the official Debian Wiki: https://wiki.debian.org/FrontPage
If you need a complete Debian manual, please read the Debian Administrator Handbook from Raphaël Hertzog and Roland Mas https://debian-handbook.info/browse/stable/.
– How to use this manual?–
Iy depends on the version you are viewing :
The Debian beginner’s handbook: The Debian beginner's handbook

 Debian? What’s that?
Debian? What’s that? Distribution, free software, community, packages, source code … but what is Debian in fact?
Distribution, free software, community, packages, source code … but what is Debian in fact?
Debian is an operating system libre (as in free speech) and gratis (as in free beer). Debian allows your computer to function and offers you a a full set of Free Software for all the usual practices (surfing the Web, sending emails, playing multimedia files, doing office kind of tasks), and more …
This collection of Libre Software comes to a large extend from the GNU project, launched in 1983 by Richard M. Stallman. The Linux kernel developed by Linus Torvalds came to complete those software to make GNU/Linux.

The Debian GNU/Linux distribution was started by Ian Murdock (rip) in August 1993. Everything started with a little, but solid, group of free software hackers, which grew up to become a big and well organized community of developers and end users. Debian is now developed by a thousand of volunteers spread around the world.

So, Debian is a complete set of free software. A free software is defined by the 4 freedoms: it gives the end users the freedom in using, studying, sharing and modifying that software, without breaking the law. To achieve this, it is necessary for the developer to distribute the source code and authorize the end-user to exercise its rights granted by a free license.
One of the major interests of the free software is that it allows competent people to audit the program code, to insure notably that it does only what it is supposed to do. So it is additional barrier to protect your privacy  .
.
Debian implements this principle in its Social Contract, and particularly in the Free Software Guidelines according to Debian.
This contract states that the Debian project will contain only free Software. Thus, during the installation of a Debian distribution, neither non-free drivers will be install by default. However the contract recognizes that some users might need “non-free” components to run their systems, like some peripheral drivers, or some applications decoding some music or video files, for example. That’s why the distributed software is separated in 3 sections:

Debian id developed very thoroughly. Every new stable version is carefully tested by users before it is released. And this release happens when it is ready. Hence few maintenance work is required once the system is installed and facing problems is very rare.
Like numerous other free distributions, Debian is not very sensitive to malware (like viruses Trojan horses, spyware…) and for several reasons:
 The back-up of you data on a regular basis remains the best insurance to protect them against potential viruses or technical issues, but also against your own mistakes (chap.9).
The back-up of you data on a regular basis remains the best insurance to protect them against potential viruses or technical issues, but also against your own mistakes (chap.9).
Do you need help? The first reflex, if you can, is to consult the documentation. Next comes the various user’s forums, and then a GNU/Linux Group (LUG), if you are lucky enough to be located nearby. There are also several events dedicated to the free software in various associations: you will be able to define appointments not far from your home by consulting agendas of the Libre software https://en.wikipedia.org/wiki/List_of_free-software_events.
The self-help and support GNU/Linux community mainly consists of passionate volunteers who share their knowledge with big pleasure. They are also very technical and are friendly called the geeks (usually wearing a beard) with several years of computer practice behind them. This experience leads them to master the terminal, which is the most efficient tool to manage a GNU/Linux system: therefore, the very first answers found on the forums will naturally be given in the form of a set of command line operations. Don’t be scared: in most of the cases a graphical solution (using the mouse within a window) exists. Ask kindly and you will get an explanation.
To be able to ask a question on a self-help and support forum you should usually register first. You need a valid email address to register with, and receive a confirmation request message, as well as your answers notifications once registered.
Before you ask a question, please remember to look first into the Questions/Answers already solved: most of the forum include a search function by keyword, which will help you find out if your problem is already described in there and has a documented solution.
Don’t forget that a forum is usually maintained by volunteers, not to be confused with a post-sales customer service organization  .
.
 A simplified introduction to computer systems
A simplified introduction to computer systemsWe begin here a scary page…
Let’s start with a simple statement: Software developers and end-users do not speak the same language…

But then … how are we going to make it?
Easy: we read the beginner’s handbook!
Within a short period of time, computers became an essential tool of the modern life. One issue is that information and education don’t follow the technical progress at the same pace, nor the needs of the users.
Therefore, it is difficult for a “new user” to discover the full capabilities of its computer. Moreover we use generally only few applications.
We will try to simplify this universe as far as possible, in order for you to make the most of your computer and to enjoy the capabilities of Debian.
How does a computer work ?
One launches applications, clicks on icons, types text in… One needs a computer, a screen, a keyboard, a mouse.
In this handbook, we will explain to you the basic manipulations in order to use your mouse  and your keyboard
and your keyboard  .
.
What use for a computer?
It seems difficult to summarize in few sentences the whole scope of information technology. However its usage is somewhat clear :
And this is exactly the knowhow you are going to learn with the beginner’s handbook  .
.
Keep in mind that this manual is not cast in stone… Our advices are only suggestions regarding your computer knowledge …
Importantly, be as honest as possible: we are all beginners in one domain or another (personally, I am unable to change the injectors in the carburettor of my car) and it is not a fault. The issue is raising only because computers are taking a large space in our lives, and penalize the newbies. But we are here to change all that!
The goal of this manual is not to transform you in GNU/Linux sysadmin (short for system administrator), but simply give you the tools to utilize your computer as you want !
Outright beginner?
You never or rarely used a keyboard? You still wonder why you must “open a window” and what is this “drag and drop” concept? Please continue reading this manual and follow its guidance. You will learn how to:
Novice user?
You are a Windows® user and/or you have a little experience with GNU/Linux, but you never installed it: it is the right time to choose your Debian (chap.4) and discover the main interface of your future system.
Basic user?
You have already used a Debian derivative and/or another free distribution, and you know exactly what you need. Let’s jump directly to the serious stuff with the actual installation (chap.5).
The mouse is the physical interface which let you move the pointer on the screen: the mouse moves are synchronized with those of the of the little arrow (the pointer)  on your desktop.
on your desktop.
There are different types of mouse; We will take here the example of the classical mouse with two buttons and a scrolling wheel.
The left-click  (or simple-click) is the most common and is used to point to (or select) either a folder, or a file or an image, which can then be open with a double-click (done by quickly pressing twice the mouse left-button). This left-click is also used to send commands to the computer (validating a choice for example) when one presses on the “button” or something else sensitive to the click (like the cross closing a window, for example).
(or simple-click) is the most common and is used to point to (or select) either a folder, or a file or an image, which can then be open with a double-click (done by quickly pressing twice the mouse left-button). This left-click is also used to send commands to the computer (validating a choice for example) when one presses on the “button” or something else sensitive to the click (like the cross closing a window, for example).
The right-click  is used to open a contextual menu (a variable list of options, depending on the software used and the “object” pointed at by the mouse) in order to modify a file, a folder, a configuration …
is used to open a contextual menu (a variable list of options, depending on the software used and the “object” pointed at by the mouse) in order to modify a file, a folder, a configuration …
The middle-click or scrolling-wheel  is used for scrolling and quick copy. If your mouse has neither a middle button nor a scrolling wheel, the “middle-click” can be emulated by pressing on the two (left and right) buttons at the same time.
is used for scrolling and quick copy. If your mouse has neither a middle button nor a scrolling wheel, the “middle-click” can be emulated by pressing on the two (left and right) buttons at the same time.
The main action of the mouse is to point an item to open it (in the case of a document for example) or to launch it (in the case of a link to an application or a menu entry). For that, nothing very complicated, just place the pointer on the element and then double-click with the left button of your mouse.
One thing that you SHOULD NEVER DO is to click several times on a button if you think that nothing happens. It is very possible that an application won’t start “immediately”, it is very depending on your hardware and the application being launched. As an example, a web browser takes significantly more time to start up, than the file manager.
To graphically move or copy your data, it is enough to “drag” them across the screen and “drop” them where you want (this is the graphical equivalent of the mv command).
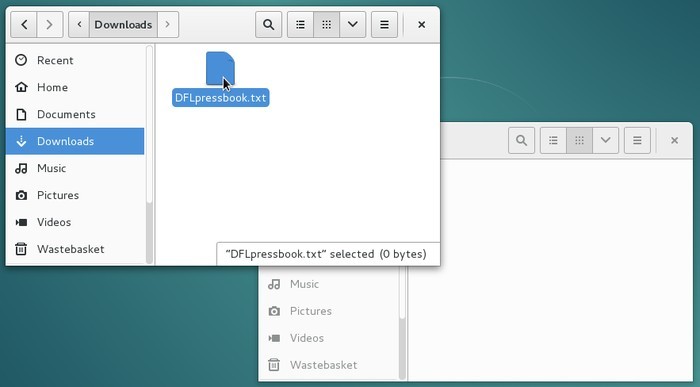
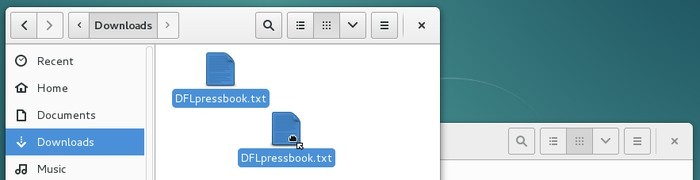
Example: to move a file you just downloaded into another folder, press the left-button the file in question, and while you hold the right-button, you move the mouse into the destination folder and then you release the mouse button:
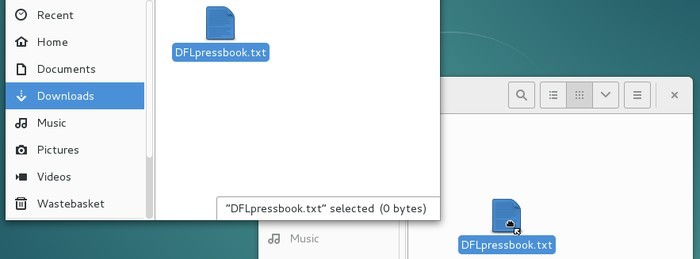
Put the cursor at the beginning or at the end of the text segment you want to select, then hold the left-button, and move the mouse over the text you want selected. Then release the mouse button.
You can also double-click (click twice quickly on the mouse left-button) on the first word you want to select and then move the cursor.
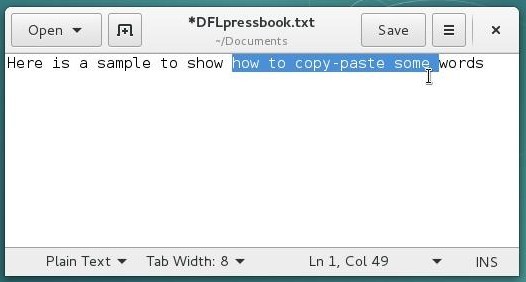
If you are fast enough, a triple-click will select the entire line or paragraph.
With the right-button: a right-click will display a contextual menu giving you the choice among several actions, one of them being the requested copy/paste. Put the cursor within the selected segment, right-click and choose the “copy” action. Then move the cursor where you want to paste the selected text, right-click again and choose “paste”.
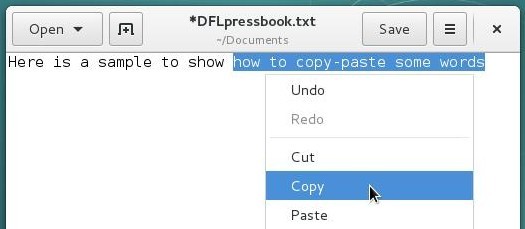
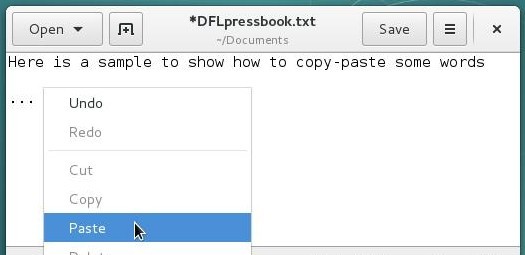
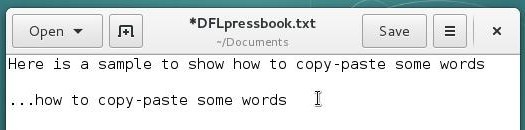
With the middle-button: this is the fastest method. Once the text segment is selected, you just need to move the pointer where you want to paste the selection and do a middle-click. The copy is immediate.
If you nedd to move, copy er delete several items, you can select them together.
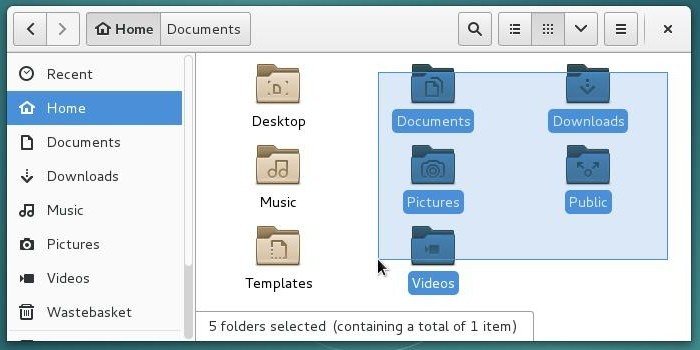
To select a group of contiguous items: press and hold the left-button, move the mouse to drag a frame around them and release the button when they are all selected. Then you can act on the selection like explain previously (copy/paste or contextual menu)
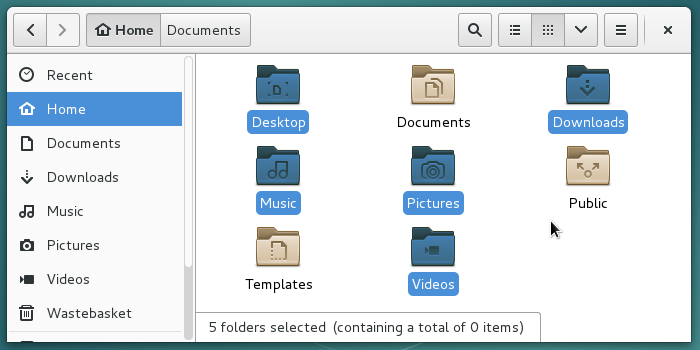
To select non contiguous items you can:
The keyboard is the main physical interface to enter data in your computer. But it is not the just the device which let you enter some words in the Internet search bar, or work with a word processor. It includes also some special keys, called modifier keys, which allow you to execute quick actions by modifying the behavior of the “normal” keys. The combinations of some “special” keys with other “normal” keys form the keyboard shortcuts.
Default QWERTY keyboard layout

The “non-alphanumeric” keys of the keyboard give you access to extended functionalities during action or edition phases. From the simple carriage return within a text editor with the [Enter] key, to the launch of a Help window with the [F1] key, find hereafter some descriptions of these special keys:
Why bother? Because it’s much faster! 
Note that the shortcuts are made by pressing down the keys together, at the same time: to copy a selection, press and hold the [Ctrl] key, then press the ‘c’ key. You can then release both keys, a clone of your selection is stored in the “clipboard” (a special buffer located in the memory of the operating system).
Hereafter a short summary of the most useful keyboard shortcuts:
| shortcut | action |
|---|---|
| [Shift] + arrows | make a selection |
| [Ctrl] + ‘c’ | Copy the current selection (in the “clipboard”) |
| [Ctrl] + ‘x’ | Cut the current selection (and save it in the “clipboard”) |
| [Ctrl] + ‘v’ | Paste the latest copy/cut selection |
| [Ctrl] + ‘f’ | Find a word or an expression |
| [Ctrl] + ‘+/-’ or Mouse-scrolling-wheel | Zoom in/out of the screen display |
| [Alt] + [F4] | Close the active window |
| [Alt] + Tab | Jump from open window to the next one |
| [F1] | Open the Help function of the active application |
| [F11] | Switch to full-screen mode |
![]()
Note that some functionalities are not only available on text segments (like copy/paste), but on files also: if you select several pictures in your ‘Pictures’ folder, make a [Ctrl]+‘c’ and then a [Ctrl]+‘v’ on your desktop, your selected pictures will be copied there. In the same way, [Ctrl]+mouse-scrolling-wheel will zoom in or out the content of your Internet navigator, as well as the content of a system file manager window.
Keyboards can’t contain as many keys as available characters. In order to write the particular characters in English, it is necessary to combine the keys like the shortcuts (simultaneous pressing of the keys)
First, a preview of the QWERTY’s hidden keys:

Each symbol is associated with a key combination. So to write “©”, you’ll have to simutaneous press [AltGr] + ‘c’.
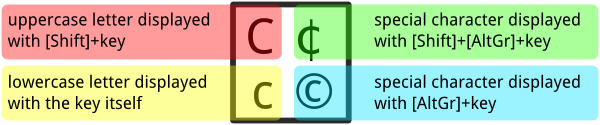
If you are not comfortable with simultaneous pressure exercises, you can always copy and paste special characters from a characters table.
mouse exercices:
keyboard exercices:
One of the great strengths of the GNU/Linux systems is their user management. The separation of rights and responsibilities provides a better security when executing system administration tasks or exchanging data on the net. Small explanation …
![]()
Generally YOU are the user, of course. Sometimes one talks about the Chair-To-Keyboard interface (abbreviated CTKI), since it’s very true that you are sitting between the chair and the keyboard, or the mouse. When you work on your computer, it does not see you. It feels only the actions made by a user with a login-name and sometimes a password.
Each user is allowed to perform a certain number of actions. Your user can, for example, use the keyboard and the mouse, read and write some documents (files), but not all of them. We call that rights: to execute administrative tasks, one must obtain the rights of the root administrator (chap.3.8.3).
![]()
Only one user has all the rights, it is the administrator. This special user is able to execute some tasks (in particular for the system administration) that other normal users cannot perform by themselves. But a single mistake in an operation made by this root user could potentially beak the whole system.
At home, on your desktop computer , you can use your computer both as a normal user and as an administrator. Some well defined actions have to be made in order to switch from one role to the other, like entering the root administrator password (chap.3.8.3).
![]()
This clean distinction, which, by the way, does not always exist under other operating systems, strengthen the stability and security of the Debian GNU/Linux system, as mentioned at the beginning of this manual. When working as simple/normal user you cannot make your computer unusable (brick it), and the potential viruses cannot infect the whole system.
More details on rights and permissions in the chapter 3.7.
 The graphical environment
The graphical environmentLet’s start by looking at the various elements displayed on the screen. On this simple image, you can already identify the first elements which are explained below in this handbook:
The “panel” or task bar (at the top of the screen, in this example, but can be moved wherever you wish)) which includes, from left to right:
a file manager window which displays the folders contained in your home directory.

You will discover other interfaces and layouts in the chapter dedicated to desktop environments (chap 4.2).
The “panel”, the task bar, the notification area… all these words to talk about the information and launcher interface of your system.
Usually, it is a banner located at the top or the bottom of your screen, displaying several types of information, launchers, menus to quickly access your data or your applications, but also to inform you (new email has arrived, what time it is, a USB disk was just plugged in …) via the notification area.
Here after a quick overview of the various “panels” on the Debian desktops: Gnome, Xfce, LXDE, MATE, Cinnamon and KDE:





Irrelevant of the type of desktop, the task bar displays, at least, the following elements:
Like almost all the elements of the GNU/Linux desktops, the task bar can be configured and embellished by plug-in (little specialized modules) or simply removed  !
!
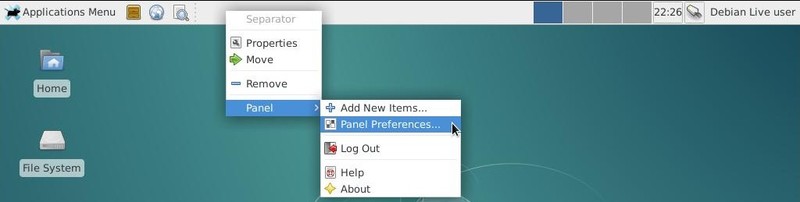
A right-click on the “panel” opens a drop down menu allowing you to change its configuration (except for the Gnome-3 desktop). Hereafter an example of configuration for the Xfce panel:
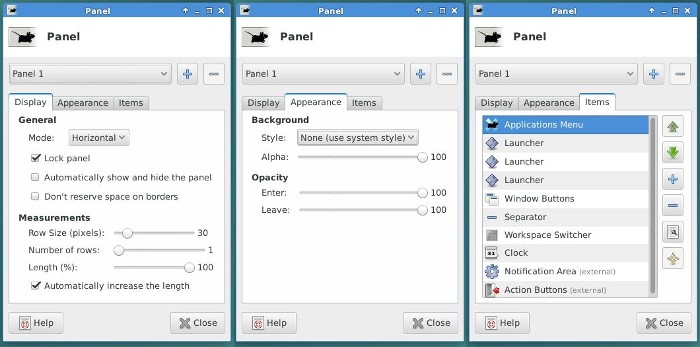
More details in the GNU/Linux desktop discovery section (chap.4.2).
The various applications installed in your system are available through several vectors: launchers on the desktop, or in the task bars, and more generally using the menus.
In the menus, your programs are listed and sorted by categories. A left-click on the menu icon displays the application and section entries. A left-click on a program icon launch the corresponding application. Each desktop has its own specific menu:
Cinnamon menu by category:
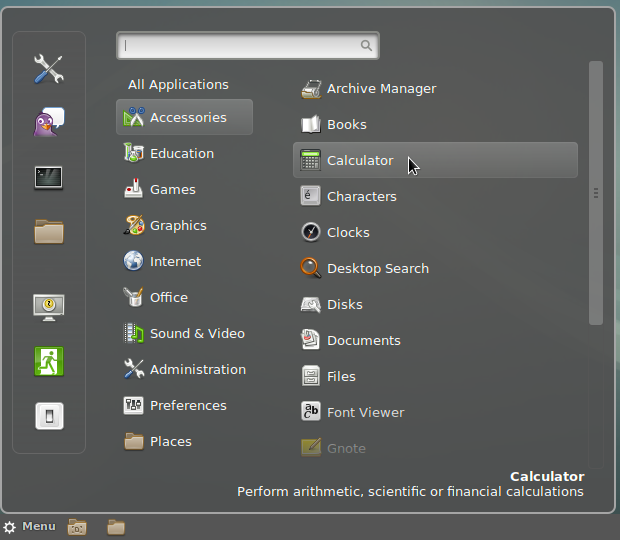
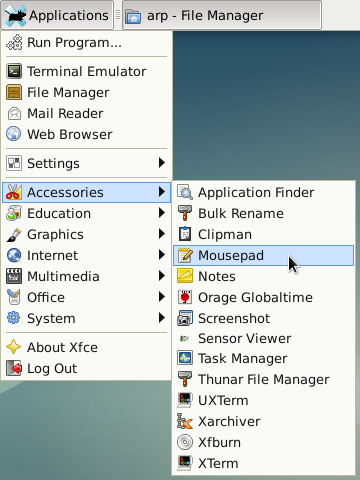
Classic drop down Xfce menu:
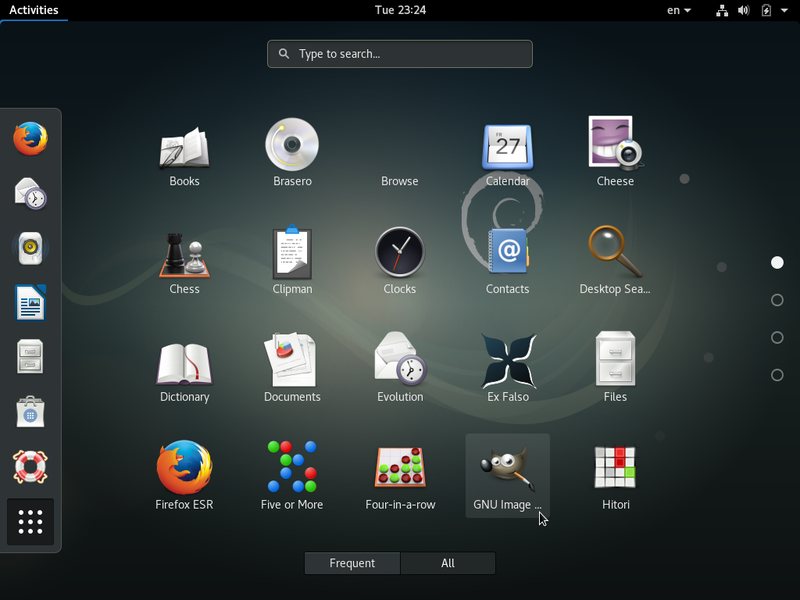
Gnome-Shell full screen menu:
Your applications, your data, your USB keys, are usually displayed within a decorated frame. Each desktop environment decorates windows its own way, but most of the times they implement the same functions:
Hereafter an example of windows on the Gnome desktop:
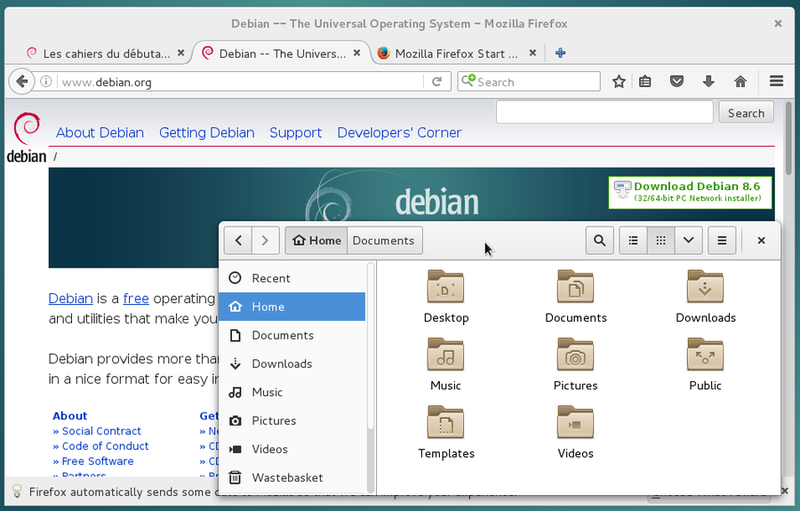
Actions on windows are generally executed with the mouse but are also possible with the keyboard: either directly with a function key, or by using a keyboard shortcut (chap 2.3.2).
To close a window, left-click on its “close” button, usually symbolized by a cross in the top right corner of the window.
To move a window on your screen simply move your pointer on the title bar (the top banner of the window) then press and hold the left-click. The pointer will then change its usual look:
from  to
to 
The window will then follow the mouse motion until you release the left button.
If you don’t have access to the title bar, you can use the special [Alt] key on your keyboard together with the mouse left-click to grab and move your window.
Windows are automatically open on the screen with a certain size. To close them, we have seen already that we need to click on the close button symbolized by a cross.
To resize a window, you need to move your cursor on the borders of the window or, even better, on one of the bottom corners.
The pointer will then change its usual look: from  to
to  or
or  depending on its left or right position. When the look of the pointer changes, press the left-button and move the mouse to resize the window like you want.
depending on its left or right position. When the look of the pointer changes, press the left-button and move the mouse to resize the window like you want.
An alternative solution consists in using use the special [Alt] key on your keyboard. Move the pointer inside the window, then press together the [Alt] key and the right-button of the mouse. Then you will be able to resize the window.
To maximize the window, double-click (click twice quickly with the mouse left-button) on the title-bar (when using the GNOME environment) or use the maximize button located next to the close button, if present (and it is the case on most of the desktops).
To avoid overloading your workspace, the Debian GNU/Linux environments support, since several years, the virtual desktop concept: the elements displayed on your screen lay upon a “desktop”. You can have several of them, which means that if you move to another “desktop”, it will be empty at first. If you return back to the previous desktop, you will find it in the same state as you left it (with your applications opened).
![]()
… “Several desktops” … What do you mean exactly ??
Well, it’s like having several screens for your computer, lined up behind each other, with the capability to change their order at will. You open the Internet navigator full screen on the first virtual desktop, then you feel like having a look at your latest family pictures. So you go to the next desktop which happens to be empty, and you can then display there your pictures also in full screen mode, and return back to the first desktop and enjoy the full real estate for the comfort of your navigation.
It is also a nice mean to get organized with your tasks: the first desktop is reserved for the Internet applications, the second for the multimedia, the third for the office work and so on, allowing you to leave open your work in progress, for future modifications, without impacting the other activities.
Each environment has its own way to represent the virtual desktops:
Gnome displays shrunk desktops on a side panel:
Xfce displays the virtual desktops in its top panel, within frame shapes representing the different workspaces.
All your data, your videos, your documents, your pictures, are regarded by Debian GNU/Linux as files, and these files are organized into folders.
Debian is an operating system (the big piece of software making your computer functional) which organizes the data according to their respective addresses, that is the path to follow, in order to access them, from the general starting point (the system root identified by the “/” symbol).
![]()
… the picture of grandma is a “file” having an “address” relative to a “root” ???
Imagine your computer is like your house. If your favorite book is located in a certain place, this “place” is like an address relative to the “house”. For example, if the book stands in the second drawer of your nightstand, one can define its address (the path to follow in order to reach it) like this: Home,bedroom,nightstand,2nd drawer,favorite book.
To separate the various “items” we use the “/” symbol, which gives the following address in computer language: /home/bedroom/nightstand/2nd drawer/favorite book.
The “root of the system is symbolized by a simple”/“. The main folder containing all the users data is symbolized by”/home/, and your personal folder is named “/home/Alice/”.
If we come back to the favorite book example, its address could be:
“/home/Alice/Documents/books/my_favorite_book.pdf”
Your personal data are stored within your personal folder, whose address is “/home/your_user_name”. They are organized within folders to to ease the finding and consulting of the files, by yourself or by some programs (it is very logical for a photo viewer to open first in the “Pictures” folder).
To help you better organize your data, Debian is distributed with few folders already defined in your personal folder: Desktop, Documents, Downloads, Models, Music, Pictures and Videos.
NOTE: Most of the objects you find in the computer file system are either files, or folders.
In the following sections of this manual we will use the word “Item” when the distinction between “File” and “Folder” is irrelevant.
Some items within your personal folder, relate to your interface configuration, the various fonts you are using, your passwords stored in Firefox, etc.
This type of data does not need to be always displayed on the screen when you consult your photos or documents: this is why these items are hidden.
They are identified by the form “/home/your_user_name/.hidden_file”. Please note the “.” (dot) symbol in front of the file name.
When you want to display them press together [Ctrl]+‘h’ (h obviously for “hidden”), or from the menu of your file manager window goto “View” > “Show Hidden Files”:
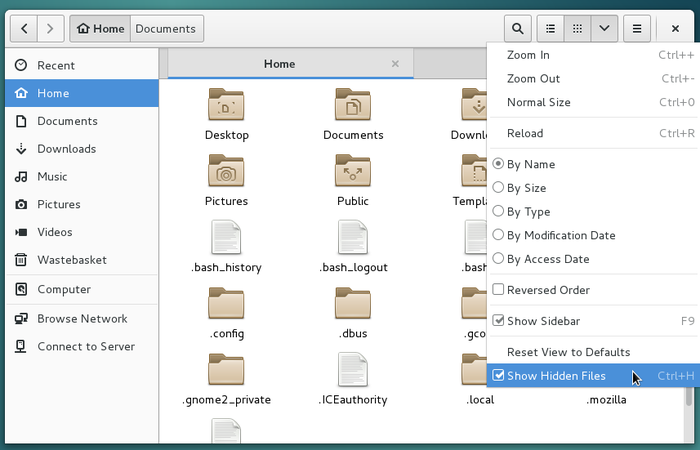
Debian GNU/Linux includes a collection of programs to navigate on the Internet, inside your personal folder, among all your photo albums, etc. These programs are stored inside “system folders”.
These folders are write-protected and some are also read-protected: this means that you can consult some of them, but you may not modify any of them, as being a simple user.
In order to modify these items, you need to use the system administrator account: “root” (chap.3.8.3).

Thunar is the file manager by default with the Xfce desktop. This program let you navigate through your various folders, “Pictures”, “Documents”, etc. by using the mouse (double-click on a folder to look into its content) or the keyboard (navigate among the folders with the arrows keys, and press [Enter] to open the selected one).The role of a file manager is to display on screen the content of these folders: your personal data. Thunar is accessible from the Xfce application menu in the task bar, under the name “file manager”.
Each GNU/Linux desktop environment has its dedicated file manager (otherwise it’s not funny) that has a slightly different interface than Thunar. However, you will find the same functions of consultation, search and modification of the data.
When Thunar displays your personal folder, a number of information and tools are already available to you:
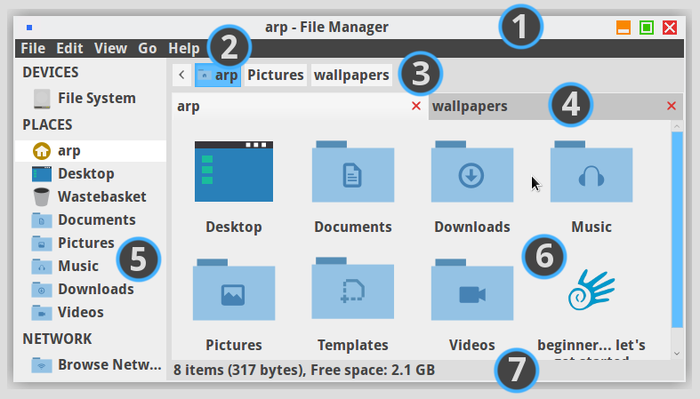
Thunar will let you consult your data, sort them, and modify them.
Note that other file managers have a different look and feel (GTK3), like placing the application menu directly in the title bar like Gnome for example (chap.4.2.1).
Consulting your data is very easy. Launch Thunar which opens by default on your personal folder. You can then decide to open another specific folder depending on the type of data you are looking for.
To open or explore a folder, put the mouse pointer over it: a double-click with the left button will open this folder in the same window. A middle-click will open the folder in a new window tab.
You can also click on the shortcuts located in the left side pane of the Thunar window.
To open a file, put the mouse pointer over it: a double-click with the left button will open this file with the application assigned to it by default. A right-click will display a contextual menu which, among other things, allows you to open the file with another application of your choice.
To select several items move the mouse cursor in an empty area of the window, left-click,hold and simply move over all the items that you want selected. Then release the button. After this, you can remove one or several items from the selection using the shortcut [Ctrl]+left-click on each of them.
More details in the simplified initiation (chap.2.2.4.4).
Once selected, you can apply the modifications to these items as detailed in the “Modifications” chapter below.
You are going to say:
I can do whatever I want with my own data
… and you are damn right  !
!
However some applications will access your data more easily if they are stored in their specific folders. Thus, the screen capture program will record its shots in the “Pictures” folder, the Internet navigator will record your downloaded files in the “Downloads” folder, the music player will look into the “Music” folder … And so on.
Thunar allows you to create shortcuts to ease the access, the classification and thus the retrieving of your data.
To create a shortcut, just “drag and drop” the wanted folder in the side pane. This folder will then be always accessible with a simple click.
A contextual menu shows up when right-clicking on an item (I.E. either a folder or a file), and then, let you make a number of actions/modifications on this selected item.
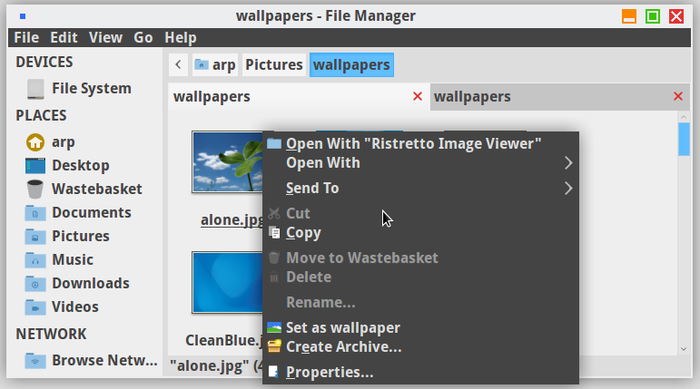
In our example the contextual menu proposes the following actions:
The famous “Trash bin” (or “Wastebasket”) is reachable directly from the side pane of the Thunar window. The “full bin” icon indicates that some items are currently in the wastebasket.
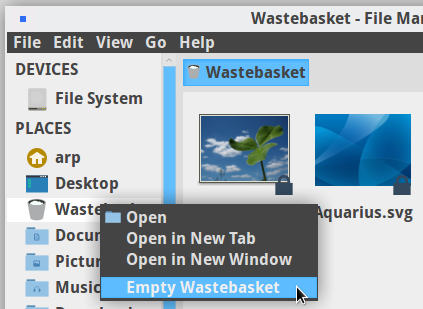
To empty the Wastebasket and remove definitively all the items in there, left-click on its proper icon and take the “Empty Wastebasket” action. You can also use the “File” menu and then click on “Empty Wastebasket”.
Sometimes the context menu has the “Delete” entry. Be careful because this menu entry will not move your files to the recycle bins: they will be deleted immediately and definitively.
Debian is a multi-user GNU/Linux system. It is therefore necessary to put in place a mechanism to protect the items belonging to each user, so that user Alice could not modify the “tax & due” list of user arp, for example.
To achieve this goal, each file and each folder belongs to one owner and to one users group.
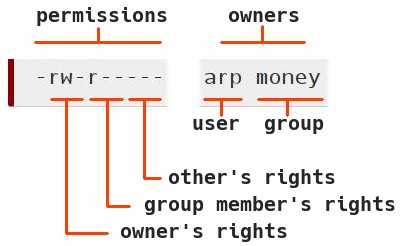
For each item, one can give Read, Write and eXecute rights distinctly to its owner, its group or all the others (I.E. persons which are neither the owner nor a member of the proprietary group).
To display these information, one can use the “ls” (list directory content) command, with the option “-l”, within a terminal window (that you will discover in the next chapter):
ls -l
-rw-r----- 1 arp money 1794 Nov 20 14:46 tax_and_due.txtHere, one can see that the user arp has the “read” and “write” rights, on the file ‘tax_and_due.txt’, while the members of the money group (which user Alice is part of) can only “read” this file, but not modify it, and the others cannot even open it (“-”, means no right).
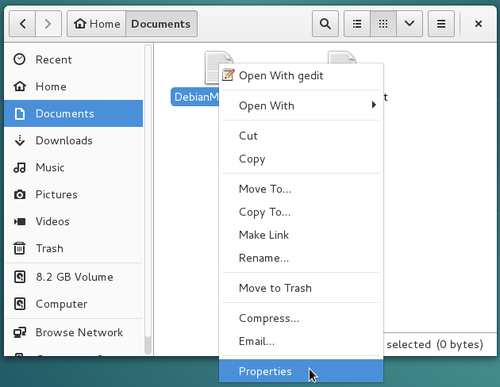
The file managers integrated in the various Debian desktops let you also display and/or modify the rights and permissions of your system folders and files “with the mouse only”. To do so, you need to open the contextual menu with a right-click on the file/folder you are interested in, and click on “Properties”:
In the new window which opens, click on the “Permissions” tab:
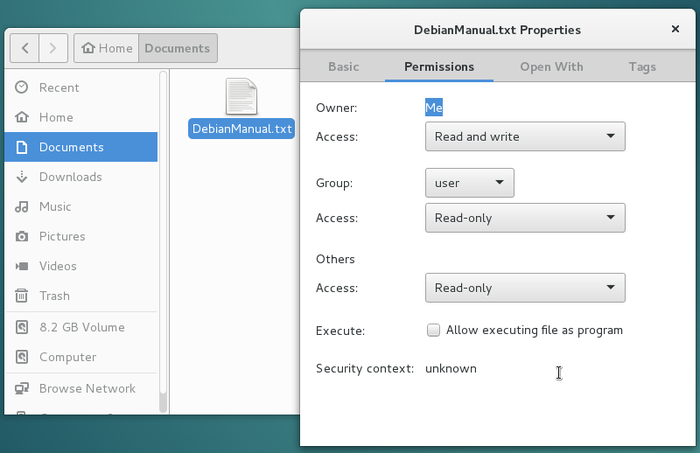
In this example, the file belongs to “Me” (arpinux), who has the Read and Write access, while the other users or groups have a Read only access right.

When you launch an application from the menu, or when you move a file from a folder to another by using your mouse, you send instructions to your computer in graphical mode.
These instructions can also be sent directly, without going trough a menu or launching an application, thanks to the Terminal which gives you access to the command line. This tool is more accurate than the graphical interface because it let you use all the options available in your application. It is also your last resort when the graphical session is gone.
The only concern is that this little black box, full of strange signs, is somewhat frightening … But we are going to demystify all this and show you that the terminal can become your new friend  .
.
In case of doubts, don’t hesitate to ask your questions on the support and help forums (chap.1.2).

Never run terminal tests in administrator mode!!: some very useful commands like “rm” (remove) allow you to bypass the “wastebasket” principle, but could be devastating on the entire system when you are running them in administrator mode.

Let’s simply start with what you see written in the terminal window:
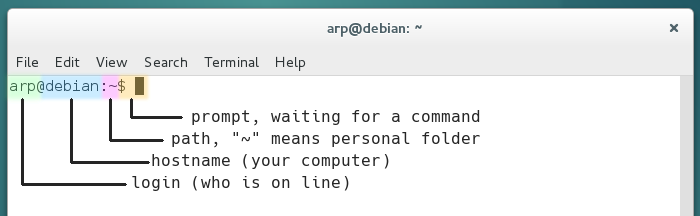
The configuration of the full prompt string resides in the ‘~/.bashrc’ (hidden file in your personal folder) “bash” interpreter configuration file. The bash program is handling the commands entered in the terminal (to make a long story short); it enables you to send commands, typed in the terminal, to the computer system in order to give it various instructions or obtain some information back.
Notez que vous pouvez aussi personnaliser graphiquement l’affichage depuis le menu “Édition > Préférences”.
To tame the beast, we are going to start with a simple “cd” (standing for “change directory”), which let you walk through the system file.
When you open a Terminal, you are by default in the personal folder of the user logged-in (here it is the /home/arp/ home folder). This folder includes the sub-folders Pictures, Downloads, etc.
To go down into the ‘Pictures’ sub-folder, I type in the words “cd Pictures” - without the quotes - (and the uppercase is of importance here, hence the necessity to clearly identify the item names one is looking at…) then I press [Enter] to send the command. To reach this ‘Pictures’ folder from anywhere in the file system, you need to provide its full path ‘/home/arp/Pictures’ (replace arp by your user name):
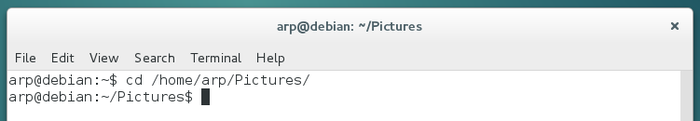
You can see here that, within the command prompt prefix, the path “~” has been changed to “~Pictures”, because you changed the folder you were in, and this is exactly like opening a folder with your graphical file manager.
However, when you open a folder with the file manager, you “see” all the items in there. Within a terminal you need to list the items with the “ls” command:
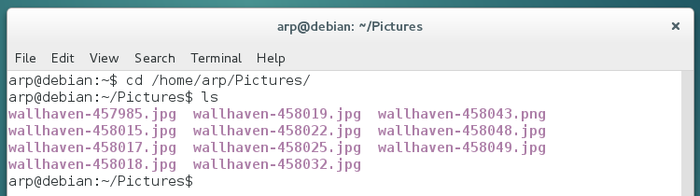
… easy, isn’t it ? See, you did not break anything Yes, but you are going to tell me that this stuff is rather useless…
OK, lets move on to cooler commands:

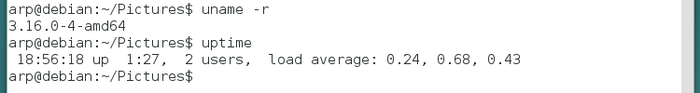
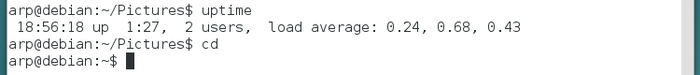
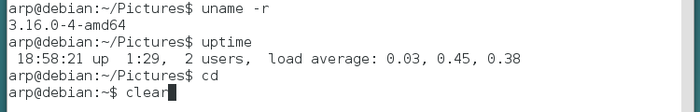
To run a command as administrator, Debian uses the command “su”. You will be asked to enter the administrator password, and nothing is displayed on screen when you type it in. This is done on purpose.
Debian can also use “sudo” (do as superuser). When using sudo, you will be asked, this time, to enter your own password.
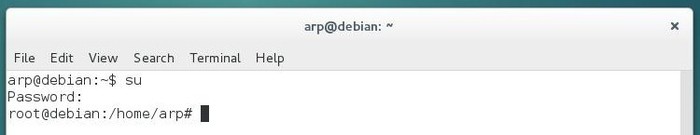
You note that the “$” sign (the command prompt delimiter), as been replaced by the “#” sign, indicating the “root” administrator account.
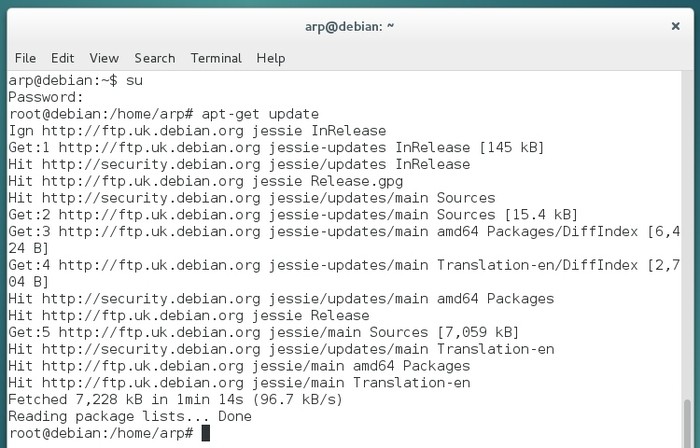
Once connected as “root” in the terminal session, you can launch system administration commands, for example here, a package repository update within a Gnome terminal, using the command “apt-get update”:
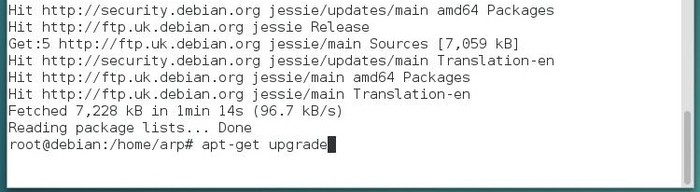
Look again at this package list update example, that is the retrieval of the latest information on packages and potential updates. After the completion of this package list update (verifying the repositories), we launch “apt-get upgrade” to execute the available updates for the software you have installed.
On Gnu/Linux, when a process must modify the system, it usually asks you a confirmation. Here the terminal informs you about the type of the expected changes and wait for your agreement, either by simply pressing [Enter] if you accept the default option (here “Yes”) or by typing “y” to accept or “n” to decline.
If you accept the changes, you will see the complete process of downloading, configuring and installing the concerned packages. Then the terminal will “give the control back to you” by displaying the command prompt:
That’s it, you just updated your system using the terminal!
The single commands tend to be boring after a while… But then it is a lot more fun if you associate several of them together in a “script” which enables the automation of series of processes.
For more information on scripts, and if you want to “learn the shell”, see the dedicated page on linuxcommand.org: http://linuxcommand.org/lc3_learning_the_shell.php.
A short summary of the GNU/Linux commands is proposed at the end of this manual (chap.11).
![]()
You must be extremely strict when you send commands in administrator mode. To avoid errors, use the auto-completion feature. This mechanism allows the computer to complete the commands you started typing (3 characters are enough), or their corresponding arguments. This is accomplished by pressing on the Tab key. If several choices are possible, they will be proposed to you as well.
Some applications in graphical mode require the administrator rights. You should not launch them with su or sudo, otherwise that might break the graphical session. You should use instead the command gksu (on gtk type desktops) or kdesu (for KDE) depending on your desktop environment.
Like you have seen in the previous section, one uses “su” (or “sudo”) in a terminal to enter a command in administrator mode. You can also launch directly your terminal in “administrator” mode using a menu entry or the application list:
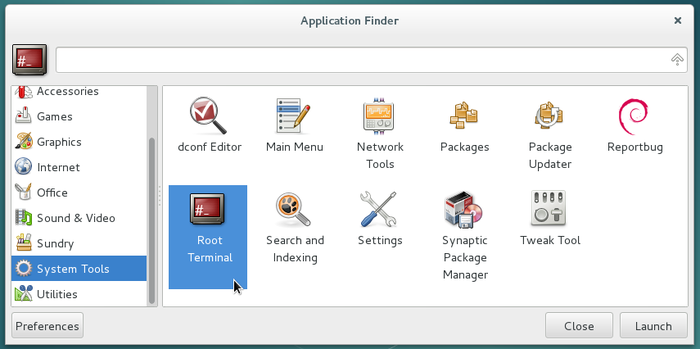
![]()
Be aware that within this kind of terminal, all the commands entered are executed with the “root” account, and in case of mistake or cockpit error, the system can become unstable. None of the commands used in this manual requires to be identified as “root”, except when clearly otherwise indicated.
 Pick your Debian
Pick your DebianDebian is an operating system offered in several versions, and you will need to make a choice depending on your tastes, your needs and your hardware.
There are a lot of Debian derivatives out there, more or less stable and/or supported. This manual and the indications in there can be used for all the Debian Stable “Stretch” derivatives.
![]()
The GNU/Linux distributions are not all supported by a community the way Debian is. Sometime, a single person handle the entire distribution. The different distributions do not provide the same level of documentation and support. They also do not offer the same durability. Choosing a “mother” distribution like Debian insures you to receive stable and regular updates.
If you want to test other distributions based on Debian, we suggest you consult the Debian derivatives official page (https://wiki.debian.org/Derivatives/CensusFull).
If you want to consult a more comprehensive list, visit Distrowatch.com which enumerates almost all the available active distributions.
Because no, there is not only “Debian” in life 
Other projects develop systems for beginners in the GNU/Linux world. If you want to try another system, let’s take a look at the GNU/Linux distributions dedicated chapter in the Software Directory (chap.12).
Let’s go ! The rest of this manual will help you to:

The processor, which is the compute and control unit of your computer, functions under a specific type of architecture, I.E. it handles data according to its own type (32 or 64 bits, PowerPC …).
We encourage you to use an ISO image of type “netinst” (chap.5.2.1.1), which gives you access to the most up-to-date software versions by downloading directly the applications during the installation process (you need an active and stable Internet connexion during the install). This version will let you install the desktop of your choice.
You can also use an ISO image already including a ready-to-use environment (Gnome, KDE, Xfce …).
But you must choose an ISO corresponding to your processor architecture. In other words, decide between a 32 bits or a 64 bits version, or again between an i386 or an amd64 version.
Note that the “32 bits” version will run on a “64 bits” computer, but not vice-versa.
Using a GNU/Linux distribution in an autonomous “live” session (chap.5.3.1), open a terminal, and in order to find out the 32 or 64 bits compatibility, type the following command:
lscpu | grep -i "mode(s)"which returns the explicit result, here an example when using an ‘amd64’ processor:
CPU op-mode(s): 32-bit, 64-bitUsing a Windows® system, your processor model is displayed in the “General” tab of the menu Start Button > Configuration Panel > System
Debian let you adopt one or several desktop environment directly from the installer interface: Gnome, KDE, Mate, Cinnamon, Xfce and LXDE. We propose you to discover also LXQt.
![]()
… But why several Gnu/Linux “desktop” ?
The computer is only a tool, and even if we ask you sometime to learn a couple of tricks to make an effective use of it, it is still your tool, and as such it must be highly adaptable to your taste, your working habit, and to your own way to have fun.
With this perspective, each desktop has its own organization, its setting method, its various functionalities. And it is not a superfluous diversity, designed by the brain mazes of some bearded geeks (although…), but rather a strength of the free software: knowing how to propose rather than impose! 
Hereafter the description of the main characteristics of this various environments, to help you decide which one to use. And then you will be able to add more of them, according to your needs and preferences.
The two main desktops are Gnome and KDE, but they are also the more “resource-hungry” solutions, so don’t hesitate to test other environments.
Integrated applications
Each desktop environment is designed to offer a minimal functionality for the personal usage of your computer.
So, within all the desktops presented here, you will find the Firefox Internet browser (chap.6.6), a system file manager, a text editor, the LibreOffice suite (chap.6.9), a multimedia player (except on MATE DE, but it’s easy to add one) and an access to a software library in order to maintain, update or make changes in your installation.

The Gnome-Shell interface is the default desktop for Debian and offers:
**The Activities Overview“**, which is a separate view designed to enable users to get an overview of their current activities and to enable effective focus switching. It can be accessed via the activities button at the left of the top bar or by pressing the ‘’⊞ Win’’ key of the keyboard. This view includes:

The Time manager, at the center of the top bar, has an on click calendar, linked to Evolution (the mail client), the personal information manager handling emails, calendar and contacts.
The System manager at the right of the top bar, including:
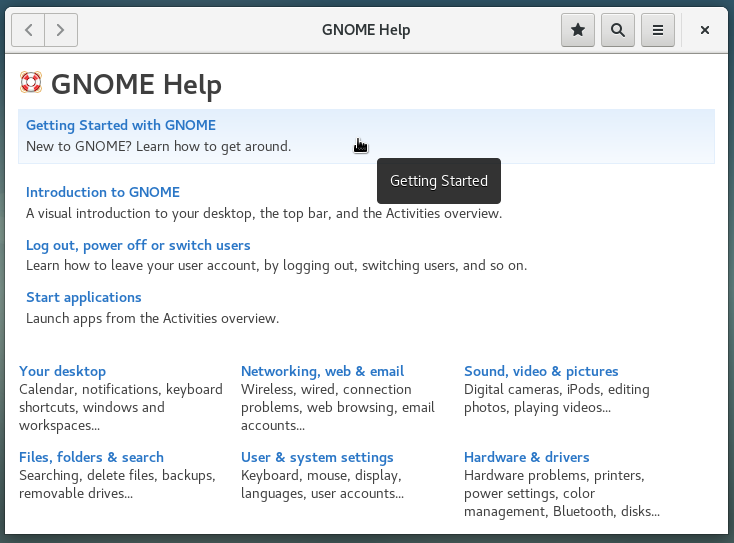
Integrated comprehensive help
Gnome includes a general detailed help mechanism, that you can access via the dock, by default, and this should reassure all the beginners, and make them a lot more comfortable:
Main applications:
Minimum RAM needed to start up: 450 Mo
Minimum RAM needed to surf the web: 530 Mo
Minimum user level: extreme beginner / beginner
Gnome project home page: https://www.gnome.org/
More details in the dedicated section of this manual (chap.7.1.1).

KDE is a project delivering a graphical environment (called “Plasma”) and a full set of applications. KDE is highly configurable, both in terms of desktop environment and supported applications. KDE has so many capabilities that some people even find difficult to deal with it.
Note that you can use KDE without any particular configuration tuning. It can be fully functional with its “out-of-the-box” settings.
The KDE environment is visually close to Windows®, and offers:
More than any other GNU/Linux desktop, you can transform KDE according to your needs and desires.
KDE is a very complete environment and has a configuration center as well as a built-in help center.
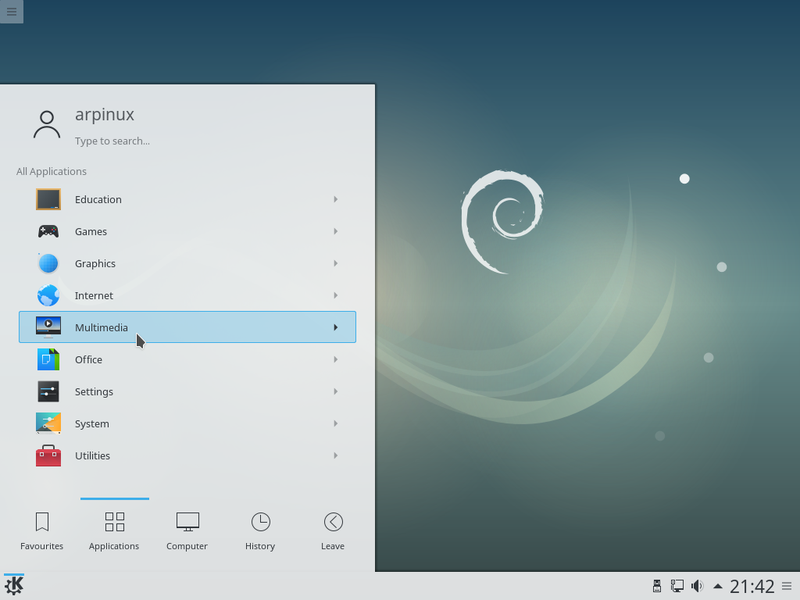
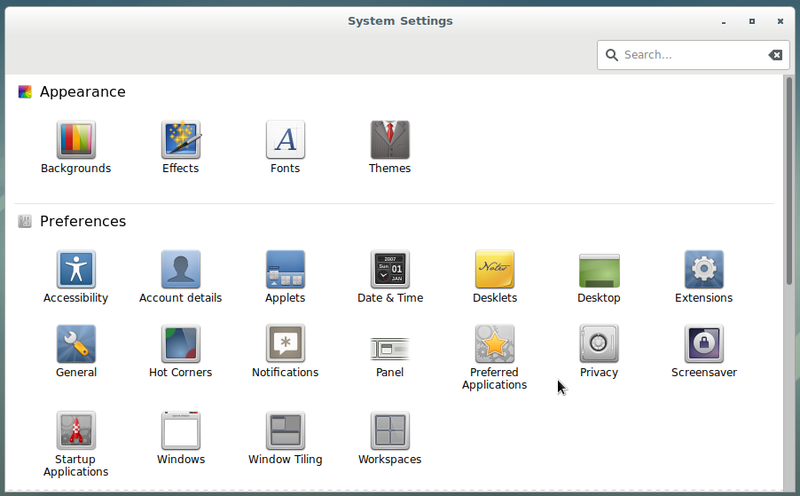
To launch the control center, navigate to the main menu > Applications > Configuration > System Settings.
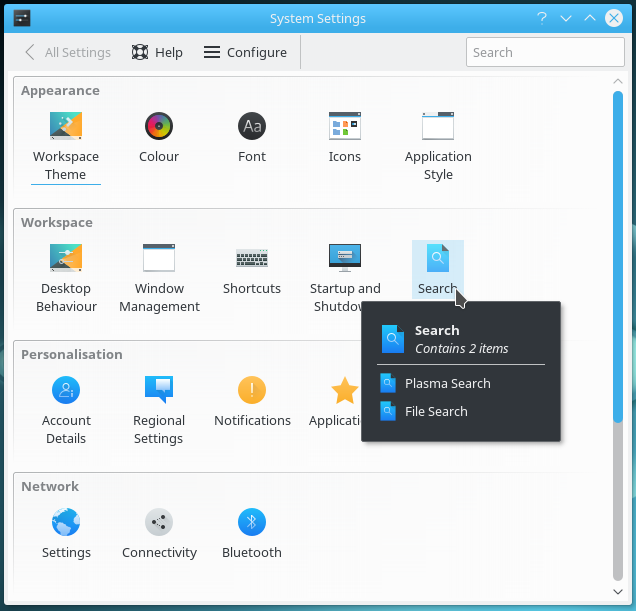
If you can not find an application, you can enter its name or function in the search box of the main menu (here with the help center).
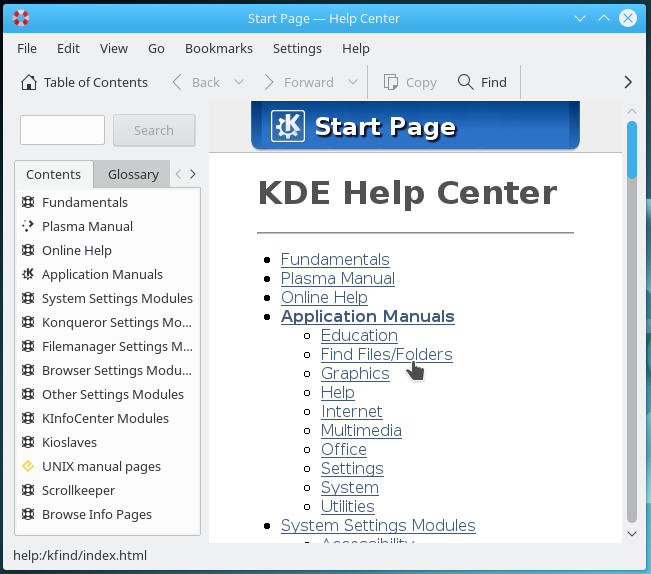
Main applications:
Minimum RAM needed to start up: 480 Mo
Minimum RAM needed to surf the web: 570 Mo
Minimum user level: beginner / experienced
KDE project home page: https://www.kde.org/
An introduction to KDE: https://userbase.kde.org/An_introduction_to_KDE
More detailed information in the dedicated section of this manual (chap.7.1.2).

MATE is a fork of GNOME 2. This means that this desktop environment was started from a copy of GNOME 2 and then modified independently.
This is the perfect environment for people who do not want to change all the work habits they acquired when using GNOME 2. This is also a good system for the computer aided music and the resource-intensive applications going with.
Mate aims to be lighter than GNOME 3, and as such, is more suitable for aging or resource limited computers. It’s clearly is a good compromise between GNOME 3 and Xfce 4.
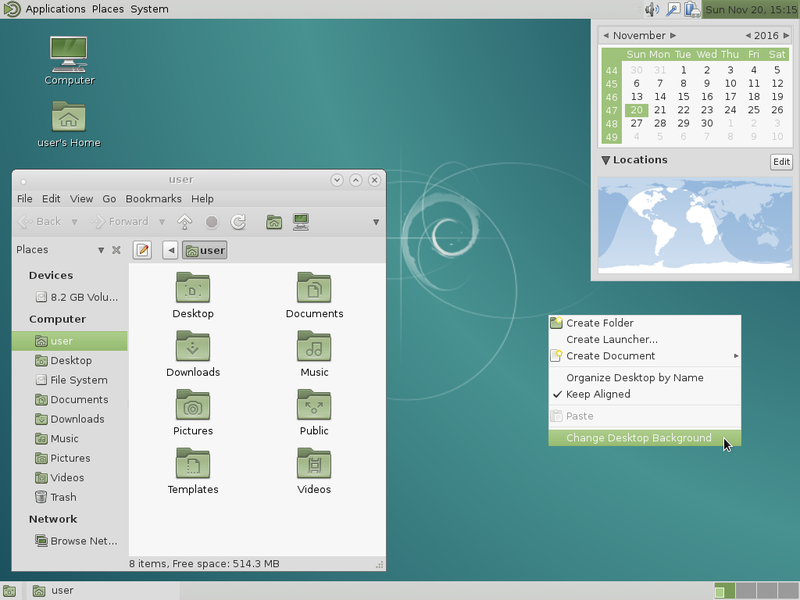
Mate offers a “traditional” interface with its two task bars:
To configure Mate you open the control center (“system” menu > Control Center) and you have access to the various components of this interface:
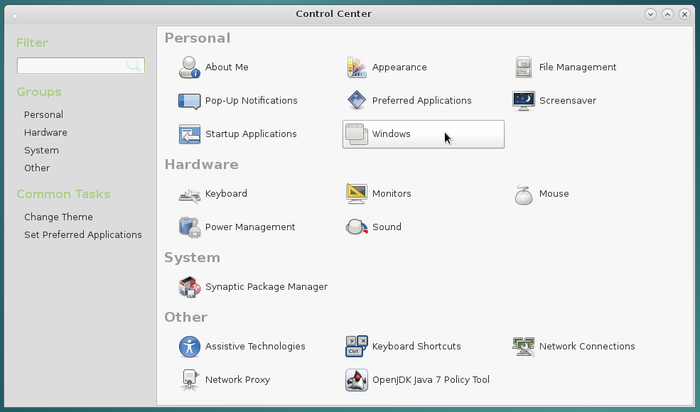
Mate project home page: http://mate-desktop.com
More details on the Mate Debian wiki: https://wiki.debian.org/Mate

Cinnamon is a desktop environment derived from the Gnome-Shell project. It moved away from this latter all-in-one interface, to adopt a more traditional interface (dash board along with a menu where Icons are sorted by categories).
Cinnamon is developed by the Linux Mint team (https://linuxmint.com/), and is one of the leading desktop environments of this specific GNU/Linux distribution.
Cinnamon uses the Nemo system file manager, a fork from Nautilus, which reinstates some functionalities removed by the latter: compact view, open in a terminal, open as root, capability to manually edit the absolute file path, etc.
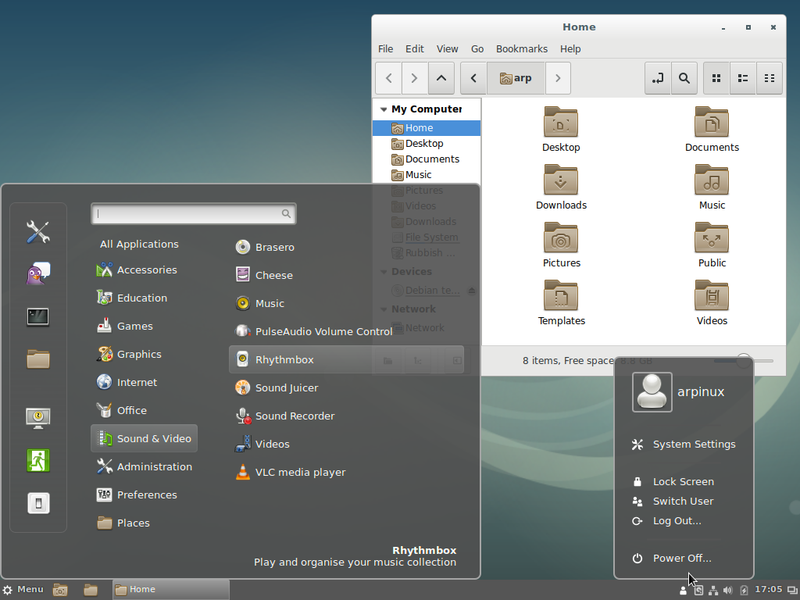
Cinnamon offers a complete desktop with all the helpful (or not) applications for your daily usage: in the screen capture above, you can see the graphical applications, and under the Internet category, for example, you will find the Firefox navigator (chap.6.6), the email client Thunderbird (chap.6.4.1), the multi-protocol chat client Pidgin, the Bittorent Transmission client and a remote desktop access software.
The Cinnamon configuration is delegated to the system settings pannel which centralized all the system and user settings:
Main applications:
Minimum RAM needed to start up: 480 Mo
Minimum RAM needed to surf the web: 560 Mo
Minimum user level: extreme beginner / beginner
Cinnamon project home page: https://github.com/linuxmint/Cinnamon
More detailed information on the CinnamonTeam: https://wiki.debian.org/CinnamonTeam
Xfce is a lightweight desktop environment for Unix type operating systems. Its goals are to be fast, little greedy in machine resources, but visually attractive and user friendly. It is expandable, thanks to numerous available plug-ins, and embeds a volume control application (xfce4-mixer), its own window manager supporting transparency, shades … (xfwm4), an integrated archive manager (thunar-archive-plugin), and disk, battery network, processor and memory monitorings, as well as various themes and miscellaneous pug-ins.
This interface is clear and traditional: you won’t be surprised during your first meeting with it.

Xfce has the significant advantage to be fully modular, because it is released with different independent plug-ins. Xfce also allows the integration of applications coming from other environments, and is able to launch, during the system start-up, the Gnome and/or KDE services by default.
It is a perfect environment for beginners, offering a great stability, a complete graphical handling (“with the mouse only”), and evolution capabilities with no real limit.
Like the other previously seen environments, Xfce centralizes its configuration settings to ease the customization. Note that each elements can also be configured from its specific interface (like a right-click on the panel to add a new launcher, for example).
Main applications:
Minimum RAM needed to start up: 250 Mo
Minimum RAM needed to surf the web: 330 Mo
Minimum user level: extreme beginner / beginner
Xfce project home page: http://www.xfce.org/
More detailed information on the Xfce Debian wiki: https://wiki.debian.org/Xfce.

LXDE is a free desktop environment for Unix like systems, and other systems which are compliant to the POSIX standard, like Linux or BSD (Berkeley Software Distribution). The LXDE name is the acronym for “Lightweight X11 Desktop Environment”.
And as its name implies, the goal of this project is to propose a fast and lightweight desktop environment.
As opposed to other desktop environments, the various components are not tightly linked together. Instead they are rather independents and each of them can be used without the others, with very few dependencies (packages used during the installation).
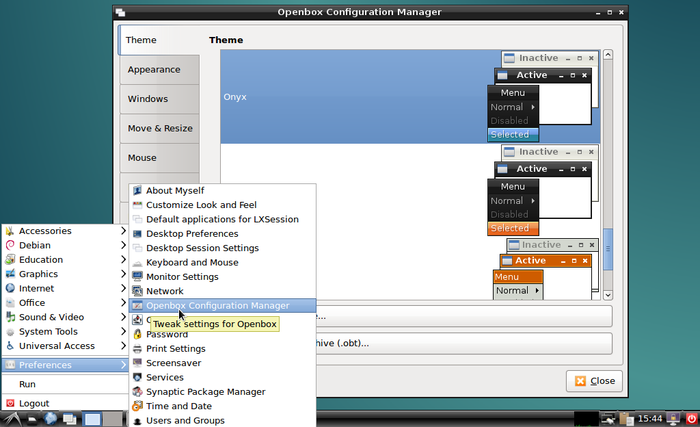
LXDE uses by default Openbox (https://wiki.debian.org/Openbox) as window manager:
The LXDE design model implies that the configuration of each element needs to go through an interface designed for this specific application. You will not find a “Control Center” akind to the Gnome one, but rather a suite of lightweight tools to customize your environment.
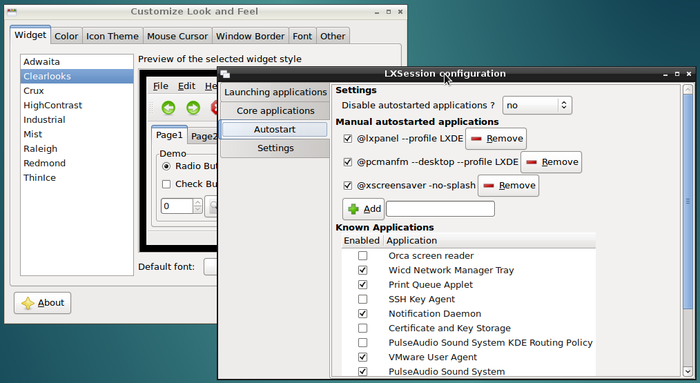
Note that the elements being configured, display their modifications on the fly which makes the customization very easy.
LXDE is notably light, making it an ideal solution for small hardware configurations and computers refurbishing, but it requires a little more time to learn and use its different elements.
Having said that, the LXDE/OpenBox couple will let you earn your first stripes on Debian as a “g33k”.
Main applications:
Minimum RAM needed to start up: 220 Mo
Minimum RAM needed to surf the web: 320 Mo
Minimum user level: beginner / experienced
LXDE project home page: http://lxde.org
More detailed information on the LXDE official wiki: https://wiki.lxde.org

LXQt is a light desktop environment. It offers a classical but a modern and lightweight interface that will let you work without thinking about it. It comes with a series of specific tools to take advantage of your favorite data and applications. It is an ideal environment for old machines and low performance.
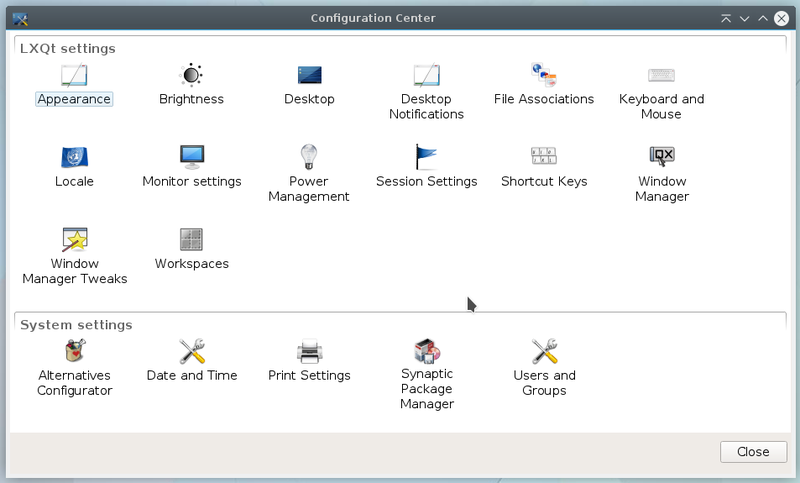
Its lightness does not dispense with a centralized configuration tool allowing you to access the settings of the main functions of your system.
Configuration goes through the control center: direction the main menu > Preferences > LXQt Settings> LXQt configuration center:
LXQt is not yet available from the standard Debian 9 installation interface, but you can easily install it from your software manager (chap.8.3)
Main applications:
Minimum RAM needed to start up: 220 Mo
Minimum RAM needed to surf the web: 310 Mo
Minimum user level: beginner / experienced
LXQt homepage: http://lxqt.org/
 Installing Debian
Installing DebianAbout time to take the plunge …
![]()
The following section describe the classical Single-boot installation: Debian will be the only distribution residing on your hard disk and the install process will be automatic (assisted partitioning, with the whole Debian system in a single partition).
![]()
This manual is intended for beginners, and does not cover all the install capabilities of the Debian system. If you are in a particular situation not covered here, look at the on-line Debian installation manual (https://www.debian.org/releases/stable/installmanual).
For installations in a different context (separated /home partition, DualBoot, Logical Volume Management, Encryption, Multi-boot, etc.) you will find the links to the specific documentations in chapter 5.5.
Most of the users never had to install a system previously (computers are usualy delivered with an operating system already installed). And that could be a little freaking … Take the time to be well prepared, take a breath of fresh air, and everything is going to be all right.
One of the first question when you wish to install Debian concerns the hardware compatibility: is Debian going to run smoothly on my computer??
A fast and simple way to check this out, is to type “Debian” followed by your machine type, within your favorite search engine: look for “Debian IBM T60”, for example. In case of doubts, don’t hesitate to ask on a support-and-help forum (chap.1.2).
In order to be really sure, you can use a distribution offering a test capability through a “live” session (chap.5.3.1).
If you anticipate to overwrite your hard disk with Debian, verify first that none of your personal data is in there: everything will be lost.
Remember to back-up your data before you start messing with the partitions (chap.9)
A Debian distribution occupies 4 GB in average, but you should still plan for a minimum of 6GB, to be able to download the updates. For greater safety and if you plan to add few applications, reserve 12 GB and you will be comfortable.
To install Debian from a “net-install” ISO requires some time because the software is downloaded from the Debian servers during the process: the time duration needed for the installation then depends on the speed and quality of your Internet connexion and may vary from 40 up to 90 minutes.
To install a derivative or from a Debian Live support, takes far less time (around 20 minutes, depending on your computer power), because the packages are already included within the downloaded ISO image. However, a system update will then be necessary after the installation, because the embedded packages are dating back to the time when the ISO image was burned.
If you anticipate to install Debian as the unique operating system on your machine, you don’t have to do anything special: the embedded installer includes the tools needed to prepare (I.E. to format) the disk(s).
If you anticipate to install Debian next to another operating system, take good care of preparing your hard disk (like defragmenting the Windows partition for example). More details in the section dedicated to specific installations (chap.5.5).
Debian ISO images are available for each desktop, in several architecture declinations, and supported by various media like netinst, CD, DVD, …
Here after the different ways to obtain a Debian ISO image. If you have other questions, read the Debian FAQ: https://www.debian.org/CD/faq/index.en.html.
If your Internet connection is stable, we encourage you to download an ISO image of type “netinst” multi-arch which includes everything you need to install Debian on any modern 32 or 64 bits (i386 or amd64) computer, with all the desired options: you will be able choose your main interface during the installation process.
This is the ISO image used in the installation section of this manual.
To get hold of the “Netinst” ISO image, you can visit this page: https://www.debian.org/CD/netinst/index.en.html. You will find there the torrent links (to share and relieve the main servers) and the direct “HTTP” to the ISO images depending on your architecture. Below the torrent link to a 64 bits ISO image:
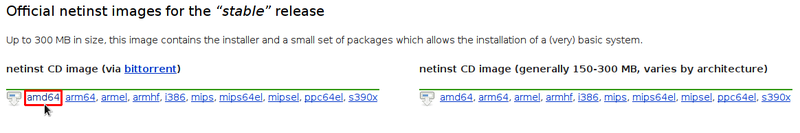
Note that if you absolutely need an ISO image already integrating non-free firmwares for your hardware (for a Wi-fi installation for example), Debian provides you with multi-arch ISOs (installable on 32 rr 64 bts architectures): http://cdimage.debian.org/cdimage/unofficial/non-free/cd-including-firmware/current/multi-arch/iso-cd/
To obtain a classic bootable ISO image, pre-configured with a specific desktop, you can look at this page: https://www.debian.org/CD/http-ftp/index.en.html.
This ISO file does not let you test your system, through a “live” session (chap. 5.3.1) to check the hardware compatibility with your PC. It only allows to install Debian on your computer, which is already cool, and let you install directly your preferred desktop, without a stable Internet connection at your disposal.
To relieve the main Debian servers and, at the same time, share your ISO image with other community members, you can use the BitTorent protocol.
To obtain the list of the available “torrents”, you can visit this page: https://www.debian.org/CD/torrent-cd/index.en.html.
Other images, called “autonomous”, are also available: they let you check your particular environment through a “live” session. They include also an installation launcher on the desktop, which, once your test is completed, let you install Debian directly from the session you are in. To get hold of a live image, you can visit this page: https://www.debian.org/CD/live/index.en.html.
More details on the dedicated “live” section (chap.5.3.1).
Note that if you absolutely need an ISO image already integrating the non-free firmwares for your hardware (for a test on Wi-fi for example), Debian puts at your disposal ISOs of type Live-non-free: http://cdimage.debian.org/cdimage/unofficial/non-free/cd-including-firmware/current-live/
In order to verify the integrity of the image, Debian computes the “md5sum” (short form of “md5 check sum”). This check can be used on all kind of data, but is particularly useful when downloading ISO image.
The md5 checking tool is integrated in almost all the GNU/Linux distributions. To verify the md5 checksum of a file, just type the following command in a terminal emulator, including the path of the file to be checked:
md5sum debian-xx-amd64-i386-netinst.isowhich will return a result of the type (to be checked against the md5sum given by the download site.):
6753c353cef5f5336079d94562ad15c3 debian-xx-amd64-i386-netinst.isoVerification in graphic mode (“with the mouse”).
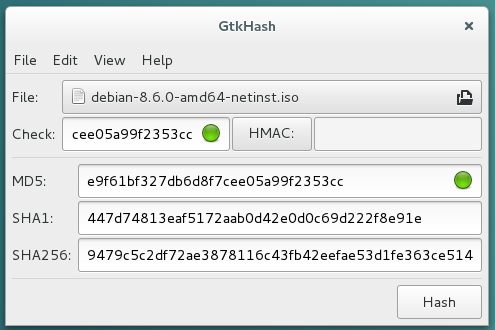
The Gtkhash program let you also check the md5 signature, but with a graphical interface.
To graphically verify the md5 checksum using a Windows® PC, you can use the WinMd5Sum software, to be downloaded here: http://www.nullriver.com/downloads/Install-winMd5Sum.exe
Once installed, launch it. A small graphical interface is open. In the “File Name” field paste or open the Debian image.iso downloaded file. In the “Compare” field, make a copy/paste of the md5 checksum retrieved from the site given by Debian (see above) and click on the “Compare” button.
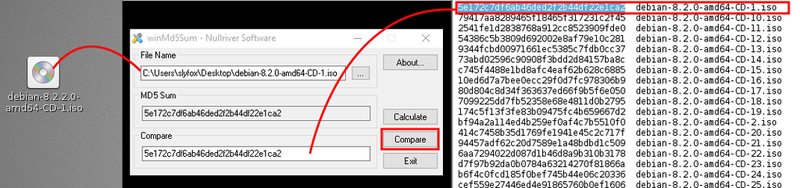
That’s all. The md5 checksum is computed within a minute or so (depending on the size of the file) and if found to be correct, you can proceed to the next step.

To burn your Debian ISO on a CD/DVD on a computer under GNU/Linux, simply open your favorite burning application, indicate the path of the ‘debian-xx-iso’ downloaded file, and start the media burning.
For the Microsoft® users, read this tutorial made for the Windows®7/8 systems: http://www.digitalcitizen.life/burning-iso-or-img-disk-images-windows-7

The USB key is the most convenient way to install GNU/Linux distributions, because you can change them as often as you want and even test several of them in parallel. The key also secures your tests because once the session is over, no trace is left on the key nor on the computer which booted from it.
The recommended method.
Plug your USB key in and launch a terminal in “root” administrator mode (chap.3.8.3). We are going to identify the USB key to be used, with the command:
blkidwhich returns information of this type:
/dev/sda1: LABEL="system" UUID="3d378712-1b6e-4f66-b9e8-2a6673c62199" TYPE="ext4"
/dev/sdb1: UUID="F9B8-E691" TYPE="vfat"Here, our key is identified as UUID=“F9B8-E691”, is formated in “vfat” and includes the sdb1 partition. Note carefully this sdb1 value, to avoid erasing by mistake a partition on your internal hard disk (here sda1 is another partiton on this disk).
The Debian ISO file should be located in the Downloads folder. Let’s move in there to act on this ISO file (the “$Home” variable replaces the address “/home/your_loginID”):
cd /$HOME/DownloadsNow, we are going to transfer the ISO content to the USB key, thanks to the “dd” command. Take good care of naming the USB key “sdb” and not “sdb1” (in our example), because it is the disk device name which is requested, not the partition, and don’t forget to change the xx in the ‘debian-xx.iso’ file by the corresponding version number.
Within a terminal in “root” administrator mode:
dd if=debian-xx.iso of=/dev/sdb bs=4M && syncThe transfer duration on the USB key is obviously depending on the size of the ISO and on the transfer rate of your USB port. This operation usually lasts from 10 to 15 minutes without any sign of activity within the terminal window. Once the transfer is completed, the control will be given back to you, that is a new command prompt line will be displayed in the terminal.
Win32DiskImager is a bootable media creation utility for Windows®: it will allow you to create a USB key on which you will boot your computer in order to install Debian.
To install it on your Windows® system, go to the main project page and download the latest version: https://sourceforge.net/projects/win32diskimager/
Win32DiskImager installs like other Windows®-compatible software. Once in place, first plug in your USB stick and note the ID of the disc displayed (disk “F:” for example). Then run Win32DiskImager.
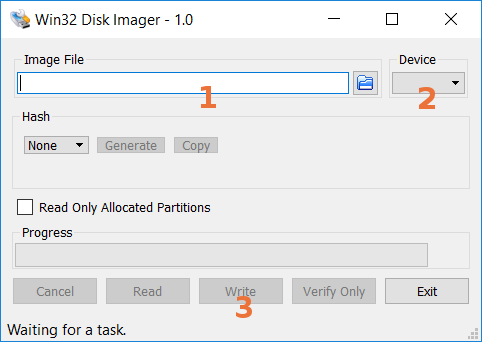
Wait a moment and you will be in possession of a bootable Debian USB key!
You still have to restart your computer on this bootable key and start the Debian installation.
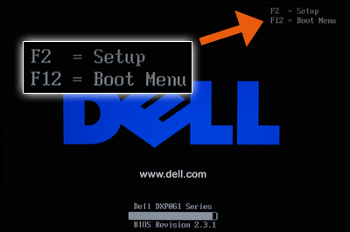
To proceed now with the Debian installation, using your CD/DVD or USB medium, you need to ask the computer to boot from this device. If your computer does not boot automatically from the desired installation medium, you need to access the “Boot menu” or modify the “Boot order” in the BIOS.
Some computers have a function key that let you boot directly from a peripheral device, without having to modify the BIOS parameters. Usually, but not always, pressing the F12 key at start-up gives you access directly to the boot options. On the other end, to access the BIOS configuration you need to tap one key like DEL, ESC or F2 during the start-up phase.
More information at: http://www.boot-disk.com/boot_priority.htm
As mentioned above, the key to access the Boot Menu at start-up may vary from one computer to another. This specific key as well as the key to access the BIOS configuration is usually indicated during the boot sequence for one or two second:
The boot menu let you select the boot peripheral without going into the BIOS configuration
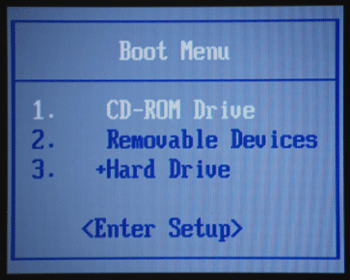
Use the keyboard direction arrows to select the right peripheral (in this example the USB key is the “Removable Devices”).
If the Boot-order menu is not available, you must modify the Boot priority inside the BIOS.
Once entered in the BIOS settings, the operations to execute are very simple, but you should be extremely careful to not modify other parameters. Hopefully, in case of mistake, the program let you quit without recording the changes, by pressing the ESC (or Escape) key. Other keys like F9 or F10 will let you reload the default parameters, or to record the changes before quitting:
The navigation is done by using the directional arrows on the keyboard. One validate or enter inside an option using the ENTER key. In most of the BIOS models, you move until the Boot menu is highlighted, then find the peripheral selection for the boot (boot device, boor sequence, boot priority) and finally put the various devices in the first, second, third etc … positions, reflecting the boot order you wish.
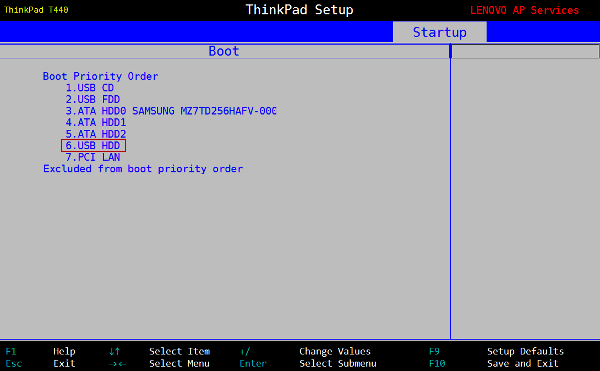
Hereafter some peripheral names, like they might appear in your BIOS settings:
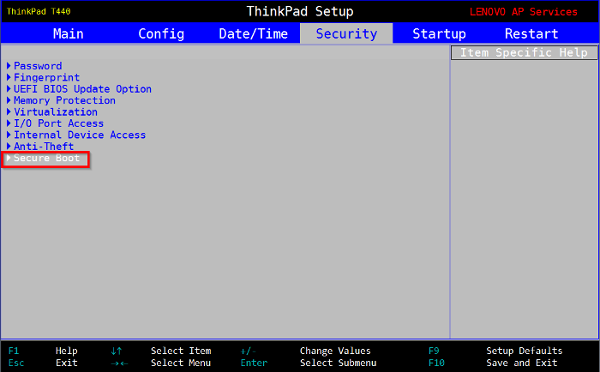
If your machine uses a BIOS/UEFI equipped with the wonderful “Secure Boot”, the handling is slightly different.
Each manufacturer has its own UEFI, and the following images and explanations might be different at your place.
Disable the secure boot
Using the mouse or the navigation arrow keys, select the “Security” or “Authentification” tab. Verify that the “Secure Boot” is “Disabled”.
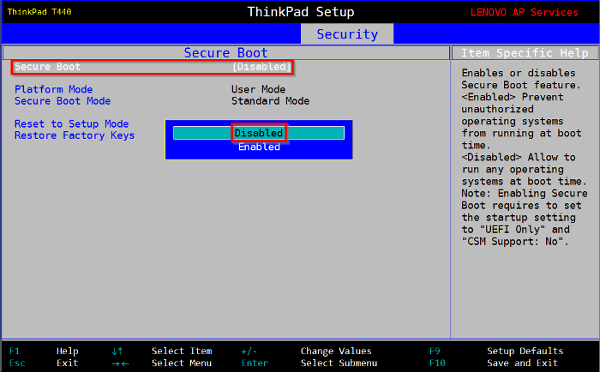
Change the boot order
Now we must change the boot order so that the computer starts first from the USB (or the DVD). Click on the “Boot” tab and modify the order, if necessary, so that your medium becomes the first of the list as explained on the previous chapter (BIOS).
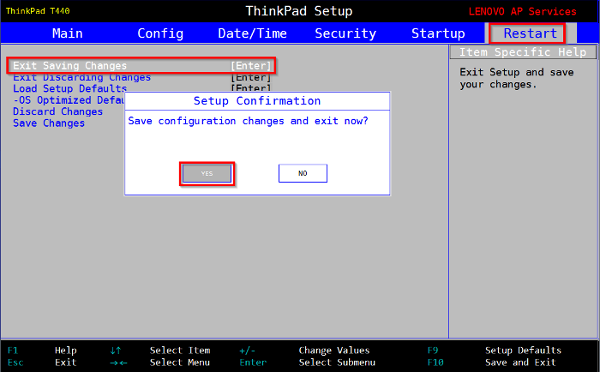
Now, you save your changes and you start the Debian installation.
The best way to make your choice: try the system directly on your computer!
There are two possibilities: you can test a GNU/Linux distribution from a stand-alone “Live” session or directly from your windows® system thanks to virtualization software: VirtualBox.
Debian provides standalone “live” images for safe testing of an environment. Their peculiarity is to change nothing on the computer, everything happens in RAM and is forgotten once the computer is turned off. These images sometimes have a setup launcher on the desktop that allows you, once tested, to install Debian directly from your session.
To get a live image, visit this page : https://www.debian.org/CD/live/index.html.
![]()
The principle of the Live CD is the capability to use/test a distribution on a computer without any risks for your personal data. The Live also let you check the distribution compatibility with your hardware.
The Debian software is “compressed” within a special file (the ‘squashfs.filesystem’ file) and embedded in the downloaded ISO image. This same special file is “uncompressed” during the Live utilization, and will later be copied on your hard disk during the installation process.
At launch, the menu is different from the classic Debian ISOs since the “Live” entry awaits you:
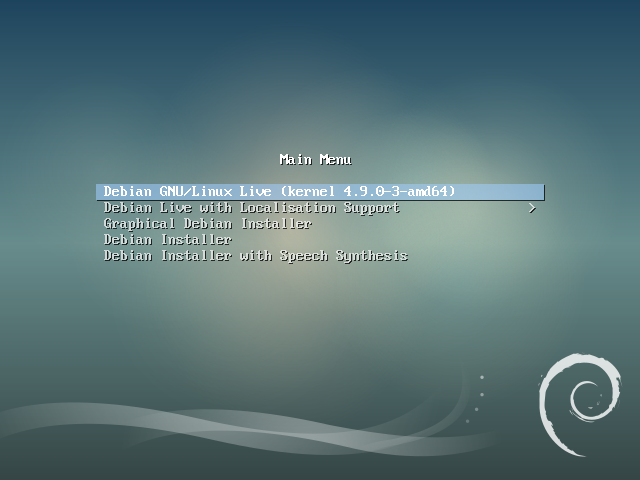
Whatever version you choose (Gnome, KDE, Xfce …), you will find on the desktop and / or in the “System” menu an entry to install directly Debian. Thus, after having tested the compatibility of your machine, you can directly install the chosen environment from the “live” session.

Virtualbox (http://www.virtualbox.org/) is a virtualization software available for major operating systems. This software will allow you to test your Debian or any other GNU/Linux OS directly on your Windows® desktop. Virtualbox is not the only virtualization software: more information about virtualization on Wikipédia (https://en.wikipedia.org/wiki/Virtualization#Nested_virtualization).
Internet is full of tutorials about installing VirtualBox. I leave you to consult these few links which will allow you to take charge quickly this software:
![]()
… We enter the virtual world here??
Kind’of’. The virtualization software makes it possible to test or install a system in a system, and to ensure the independence of the two installations. VirtualBox will “make believe” the system you want to test (referred to as “guest system”) that it is all alone on its computer, while ensuring exchanges (shared folder, network connection sharing, etc.) With the host system.
Your guest system will be installed on a “virtual disk”, which will simply be like a big archive in a folder of your documents.
Note that this test method does not verify hardware compatibility and is only for you to discover a distribution before installing it on your hard drive.
Here comes the long-awaited moment, the actual installation of the Debian GNU/Linux system on your machine … Are you ready to begin the exciting journey?
Hereafter a visual step by step explanation on how to easily install Debian, using the graphical installer. This method erases the whole disk and installs Debian as the unique operating system on your machine. The ISO image is of the type “netinst”.
The Debian installer displays an explanation at every step of the process: with GNU/Linux  , there is no advertising, so please take few seconds of your time to read the little messages which talk about your future system
, there is no advertising, so please take few seconds of your time to read the little messages which talk about your future system
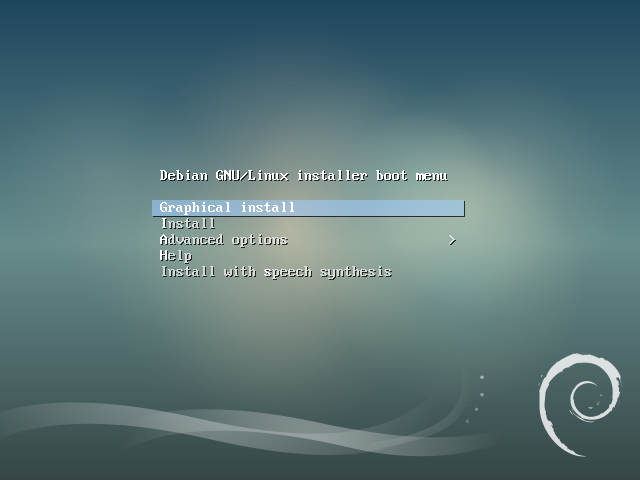
When the installer begins, we select the installation mode:
If your motherboard boots under UEFI, the display might be slightly different:
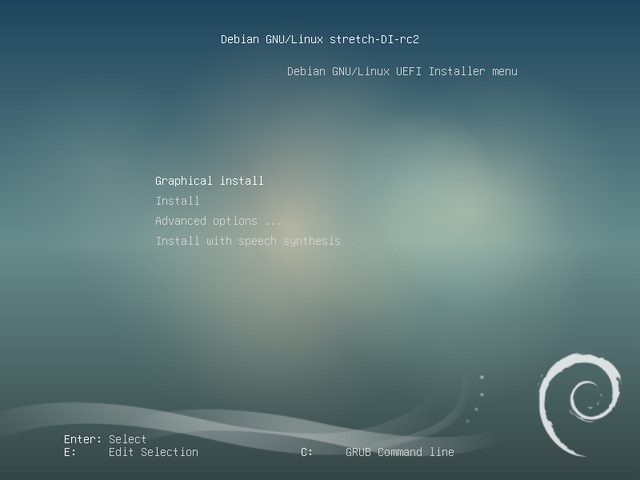
More information on UEFI in the Debian wiki (https://wiki.debian.org/UEFI).
During the start-up, the installer proposes a choice of several installation modes:
Each installer pane displays a clear explanation message. When you don’t know the answer, take the default setting. However, pay great attention during the partitioning phase, since this operation could erase the existing data on your hard disk(s).
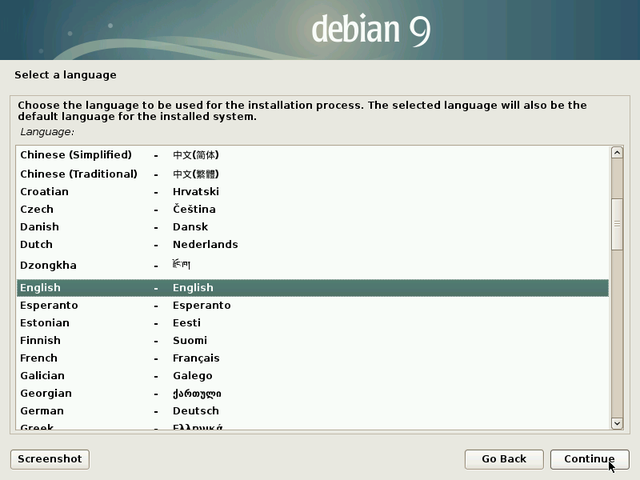
Selection of the system language by default: this choice will also modify the installer language itself, which then will display its own messages in English (if you chose “English”).
This information allows the system to automatically set the date and time of your system, using a remote time server.
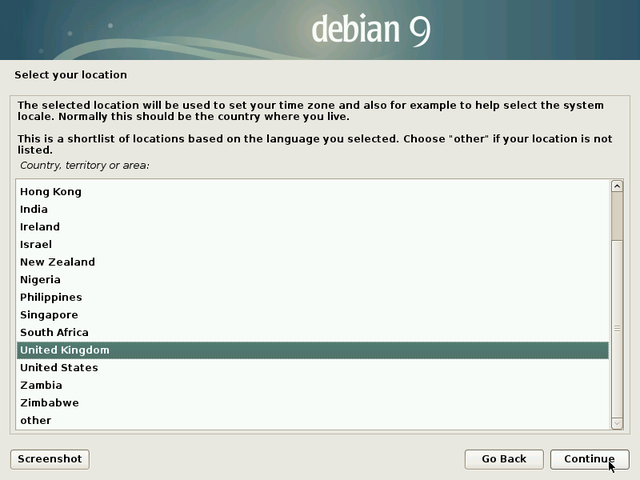
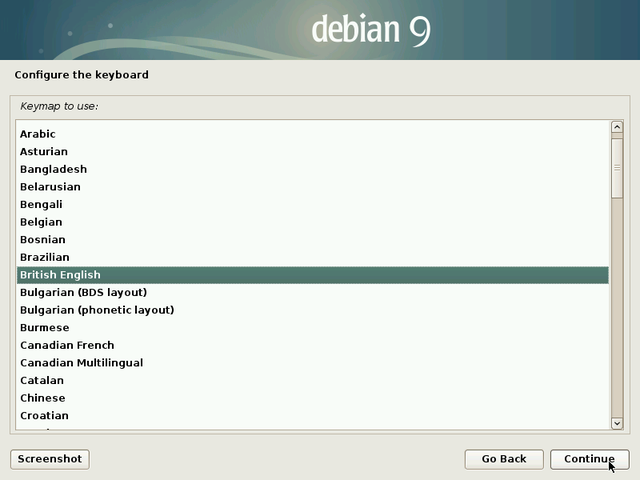
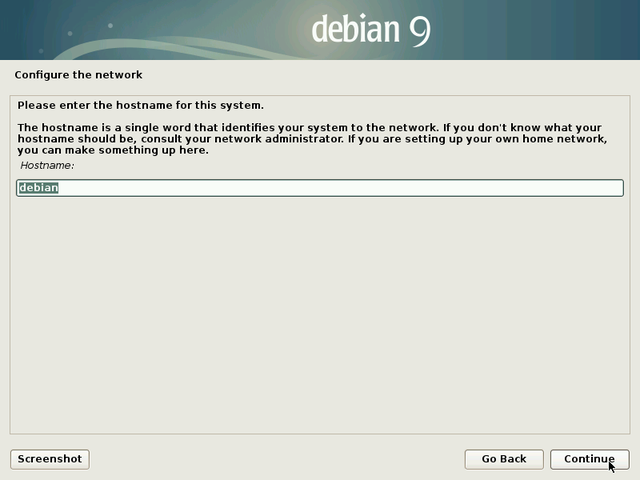
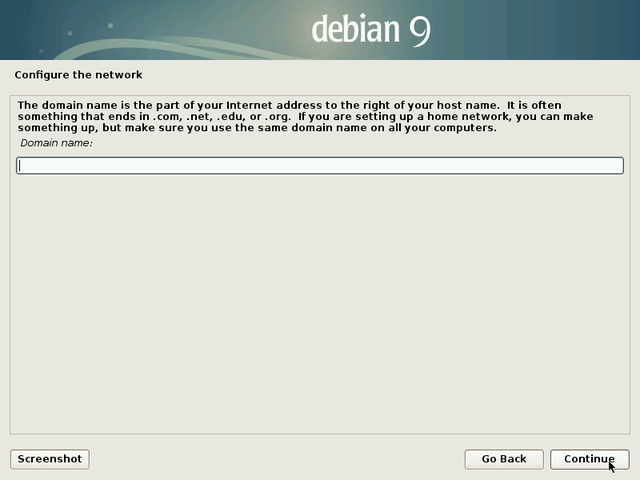
Leave this field empty if you don’t know the answer.
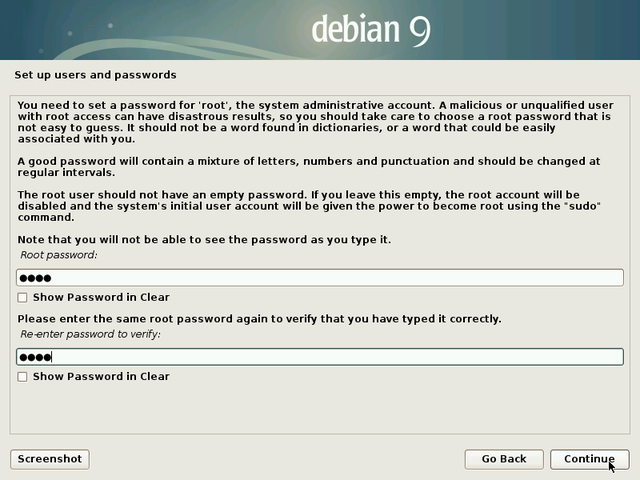
Enter the administrator password (twice to confirm). Like indicated in the information message, creating a “root” administrator account is not mandatory. If you leave the fields empty, the first user will receive all the rights to perform administrative tasks with the “sudo” command and your password.
More information about passwords on dedicated section (chap.10.1.3).
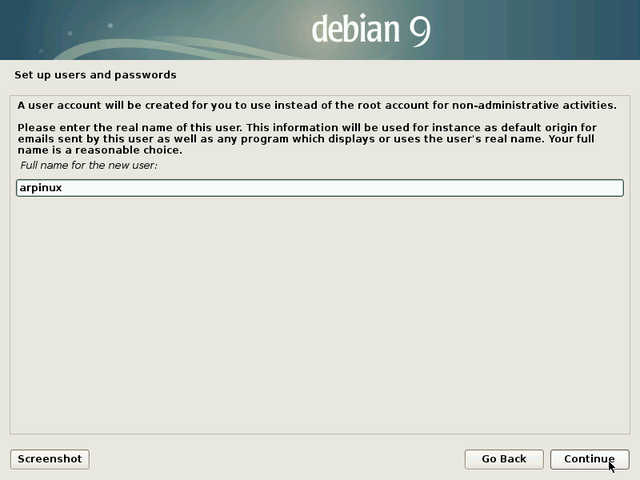
Start by entering the full name of the main user:
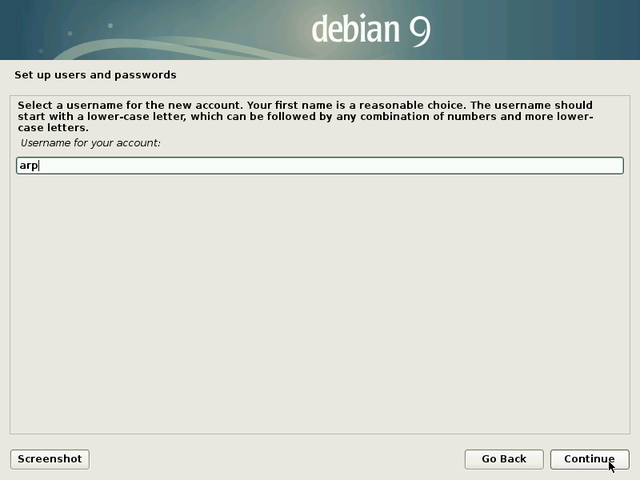
Then enter its identifier, that is the pseudo which will be used during the connection (login) to a session:
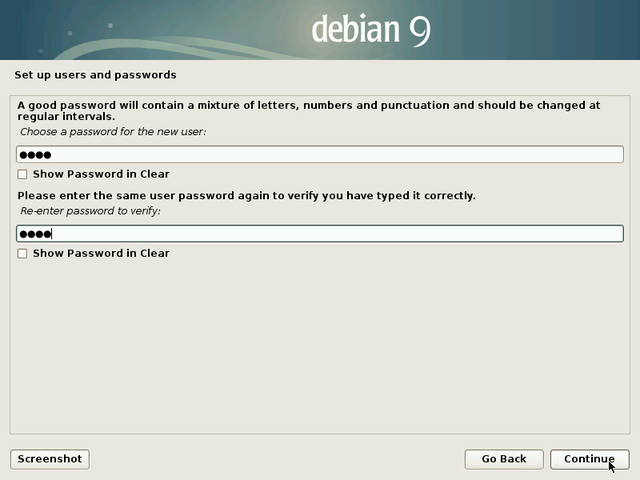
Like for the administrator account, you need to enter the password twice for confirmation.
![]()
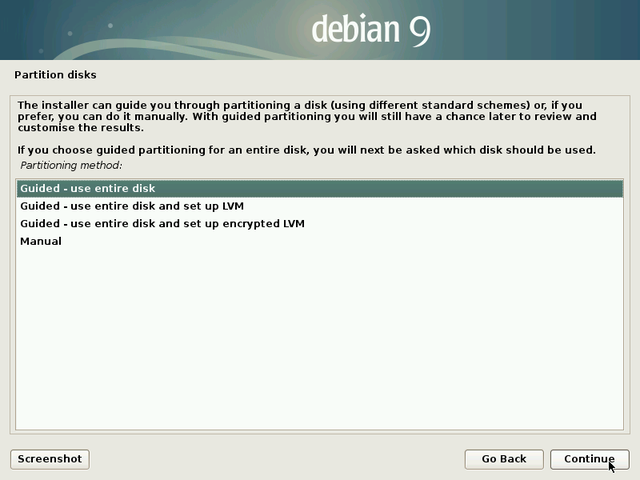
… “Partitioning” … What’s that?
The partitioning process consists in organizing different partitions on your system. Partitions are non-overlapping area defined on your hard disk(s), each one of them having its specific properties (file system type, unique identifier, size, etc.). In order to function correctly, Debian GNU/Linux needs at least one partition to install the operating system. An additional exchange partition (called SWAP) is highly recommended, to deal not only with insufficient memory space, but also with the suspend or hibernation functionality.
The guided partitioning scheme proposes 2 partitions (system + swap), but you can opt for a scheme proposing a separated “/home” partition, and use another hard disk to store your personal data (as an example).
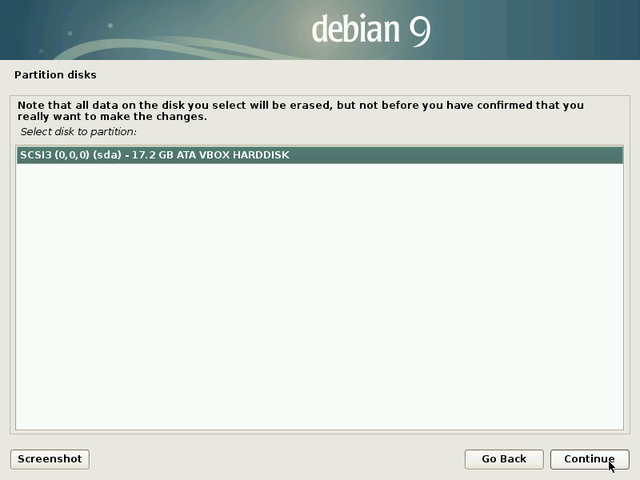
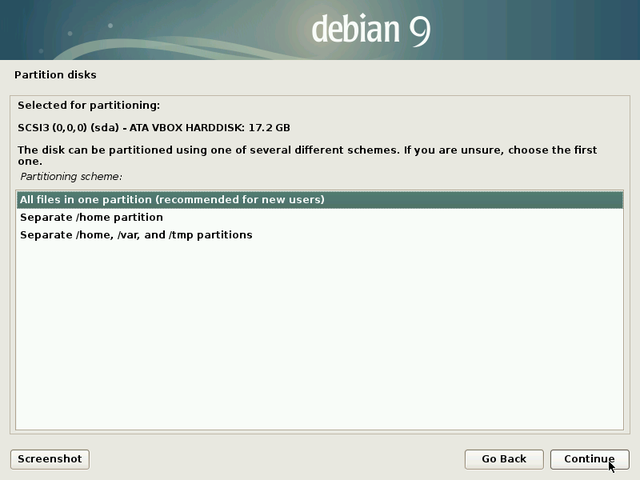
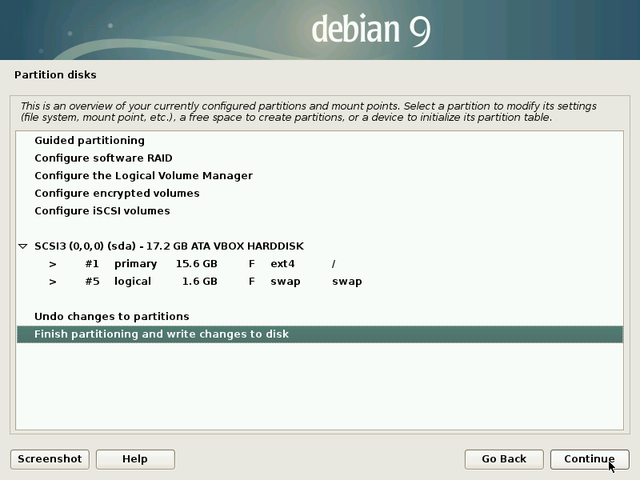

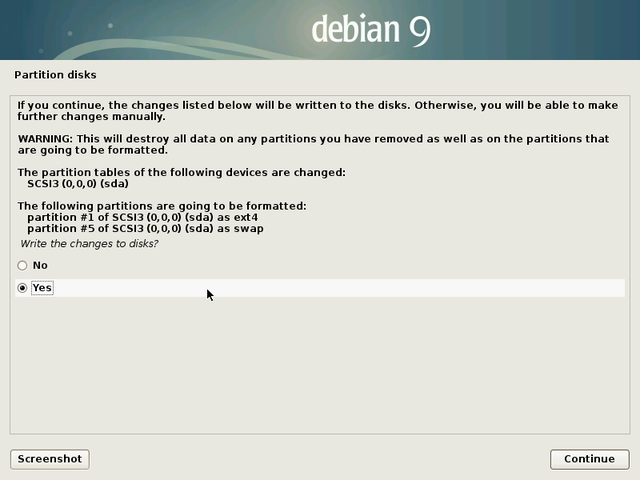
Warning: this is the step during which the installer will format the partitions.
The data on the selected disk will be erased!
The base system is installed. You will choose your main interface later.
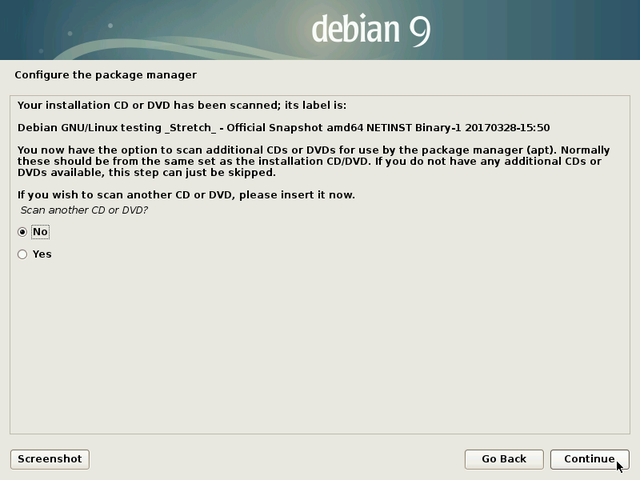
Optional: Had you opted for a Debian CD set including all the packages needed for the installation, you would now insert the second CD (and tick the “Yes” option).
![]()
… where should I put this mirror?
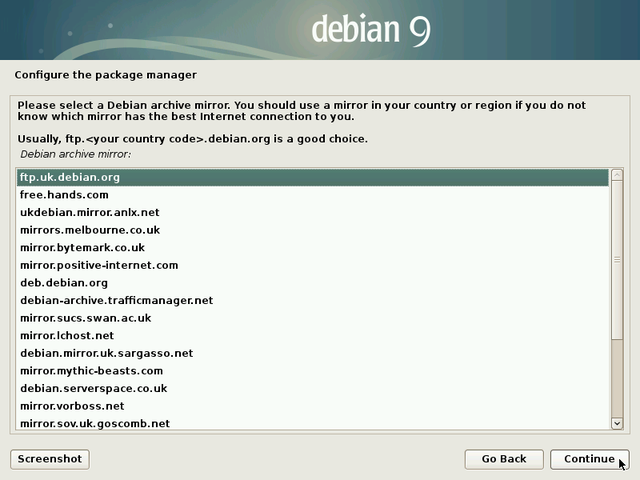
“A repository mirror” is a computer server, available on-line, hosting the full set of the Debian packages. If you don’t have all the CDs on hand, Debian will grab the software or the packages you need on the network mirror servers.
There are repository servers all around the world, each one being the exact copy (mirror) of the others. In this example we select “Yes” and in the following section we will pick an Internet mirror located in the United Kingdom.
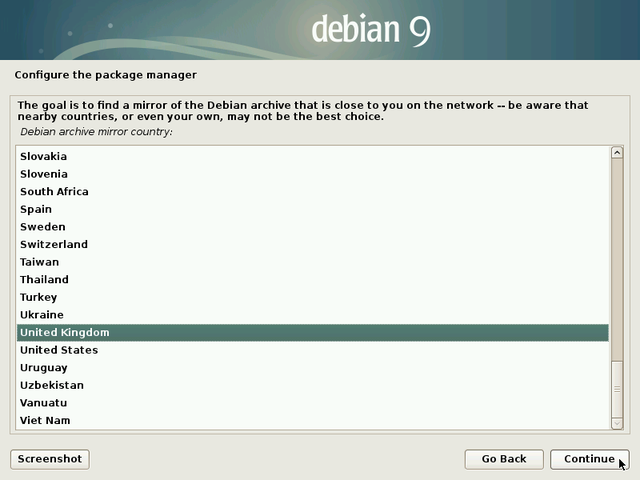
The server proposed by default is usually a good choice.
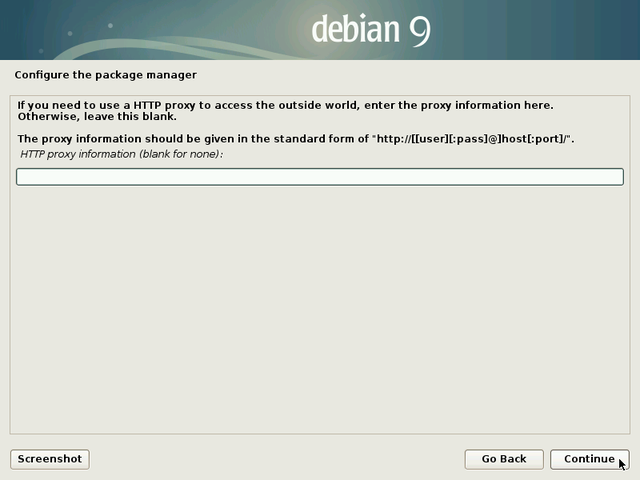
Leave this field empty, if you don’t know.
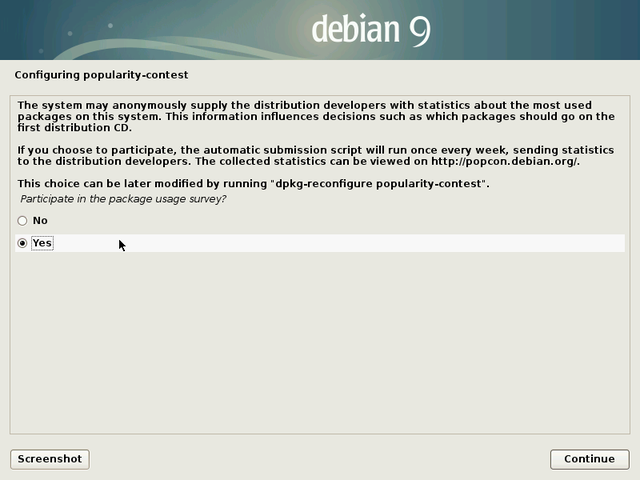
This can be useful to the community, but it is not mandatory.
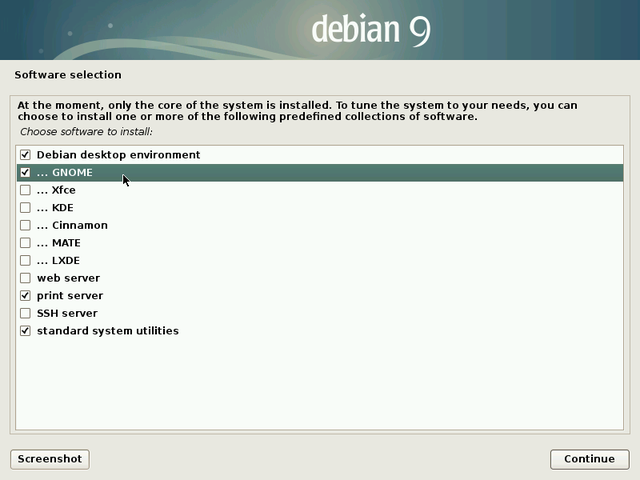
Now, it is time to select your main desktop interface, as well as the main services to be installed by default. Note that you can select several desktops in view of directly installing several environments. Hereafter a summary description of the proposed choices:
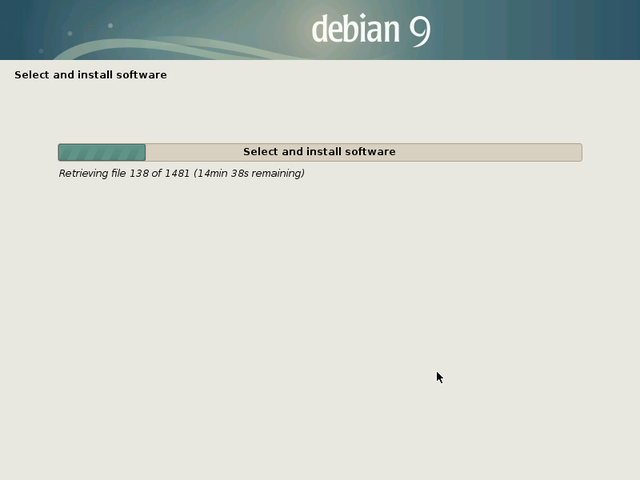
Time to take a little pause. Downloading and installing the packages may take quite some time, depending on the power of your computer and the Internet connection bandwidth.
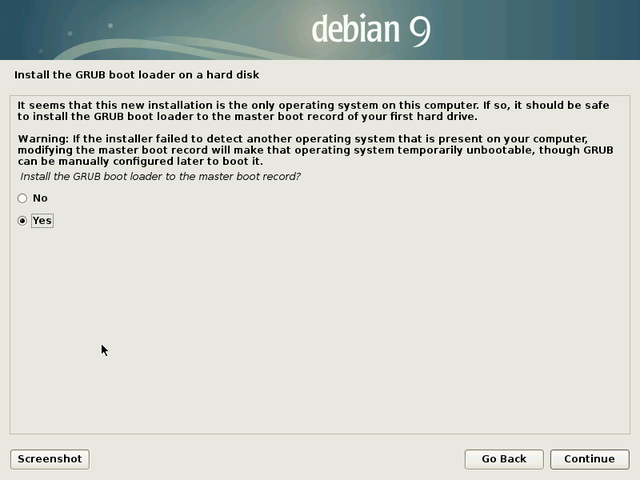
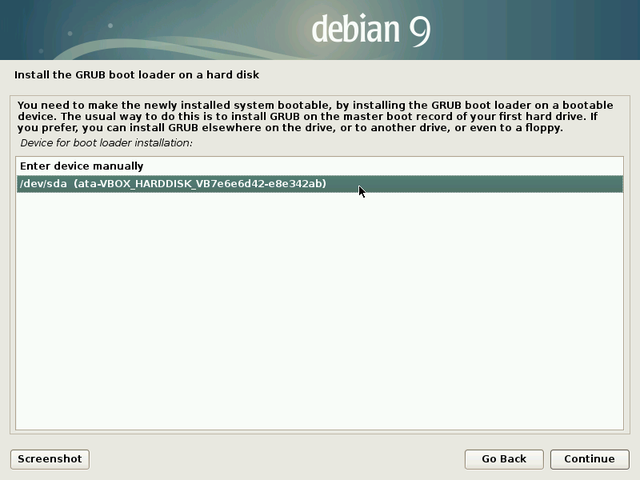
When the system installation is of type “simplified single-boot”, you should install Grub on your machine main disk, usually identified under the nice “/dev/sda” name.
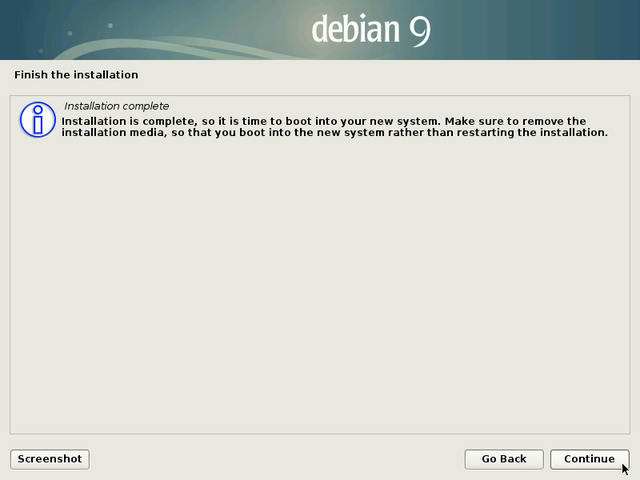
Don’t forget to remove the CD or USB key to avoid re-launching the installer during the next boot.
Then complete the installation process by pressing the Continue button.
Grub boot loader selection menu:
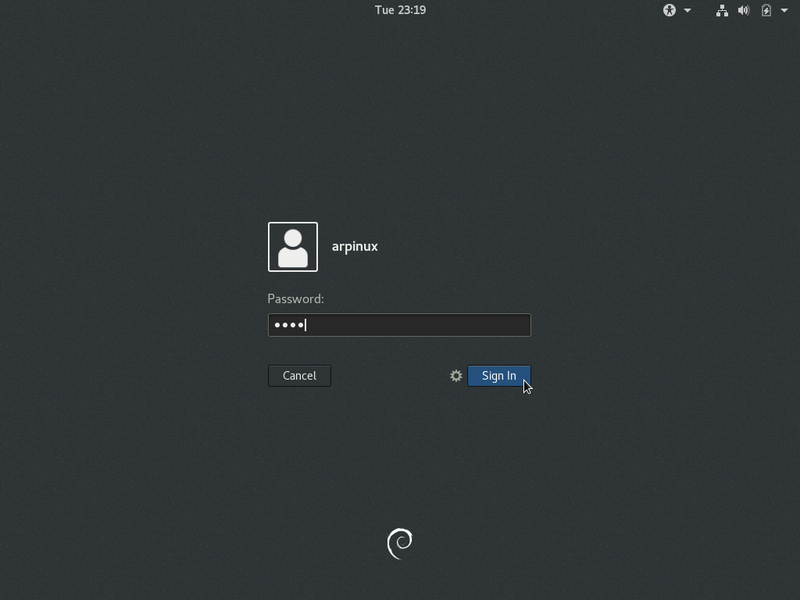
Gnome login in:
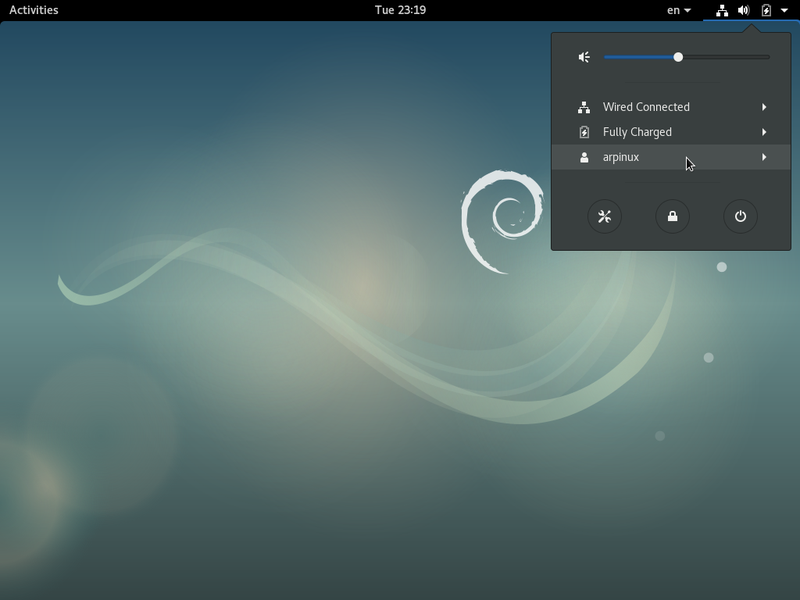
Interface by default on the Debian Gnome-Shell desktop:
Debian offers more possibilities than just the two methods explained in the previous chapters.
But this manual being intended for the beginners, the more complex installation modes are detailed in the official Debian documentation: https://www.debian.org/releases/stable/installmanual
Just to give you a flavor of the other installation modes:
The Dual-boot mechanism let you install side-by-side two independent operating systems, and doing so, allows you to select, at boot time, which one you want to launch.

This is not the recommended method: there are inherent risks for your data during the partition resizing. If you choose this solution to get started on Debian, please remember that you can very well test it first by using a Live session (chap.5.3.1) with no risks for your data.
More information of the Debian Dual-Boot Wiki: https://wiki.debian.org/DualBoot
LVM is an acronym for Logical Volume Manager.
Is usage consists in:
So, the “Logical Volumes” utilization, replaces straight out the usual disk “partitioning”, and provide a more flexible way to manage disk space by allowing modifications on them at any point of time.
It is possible, as well, to keep one part of the LVM partition without installed “Logical Volume” pending further decisions.
More details on the dedicated Debian LVM Wiki: https://wiki.debian.org/LVM
The confidentiality of personal data is is a pretty hot topic these days. In order to better protect your data, you can opt for an encrypted installation; With this kind of installation, even in the case of theft of your computer, or the removal of its hard disk, no data access is possible with the password !
The Debain Administrator’s Handbook provide us with more details (https://debian-handbook.info/browse/en-US/stable/sect.installation-steps.html#sect.install-partman):
This feature can be added underneath any filesystem, since, as for LVM, Linux (and more particularly the “dm-crypt” driver) uses the Device Mapper to create a virtual partition (whose content is protected) based on an underlying partition that will store the data in an encrypted form (thanks to LUKS, Linux Unified Key Setup, a standard format that enables the storage of encrypted data as well as meta-information that indicates the encryption algorithms used).
To put it simply, LUKS creates a container to host an encrypted volume protected by a password.
For more information and a complete guide, visit the digital self-defense guide: https://ssd.eff.org/en
Wikipédia is my friend …
RAID is the acronym of redundant array of independent disks.
RAID is a data storage virtualization technology that combines multiple physical disk drive components into a single logical unit for the purposes of data redundancy, performance improvement, or both.
Please note that the Debian installation in RAID mode, uses the RAID software (thanks to the mdadm tool) and not the RAID hardware (handled by a physical RAID controller).
For more details and installation tutorial see the official Debian wiki https://wiki.debian.org/SoftwareRAID or the dedicated section of the Debian Administrator’s HandBook https://debian-handbook.info/browse/stable/advanced-administration.html#sect.raid-soft
 Fast boot after installation
Fast boot after installationFirst things to do after installation: Wi-fi network connection, screen resolution, printer configuration … everything you’ll need to make your workstation operational.

Using either an Ethernet wired connection or a Wi-fi wireless connection, your Debian system is expected to access the network. The Ethernet connection is recognized natively. As far as the Wi-fi is concerned, it is sometimes necessary to use a non-free driver.
This is the network manager delivered with Gnome, Mate, Cinnamon, and Xfce. It is accessible from its icon within the notification area (here on Gnome and LXDE):
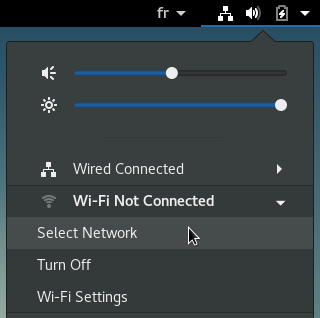
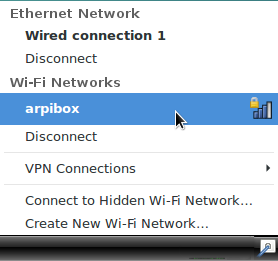
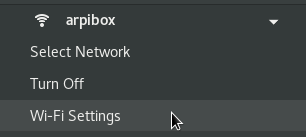
All the active or inactive connections are listed here, and the Wi-fi networks are detected as well. Left-click on the network you want to connect to, and a dialog box will pop up. Select your network then “Connect”. A password is then required (the one given by your Internet Service Provider). Here on the Gnome desktop:
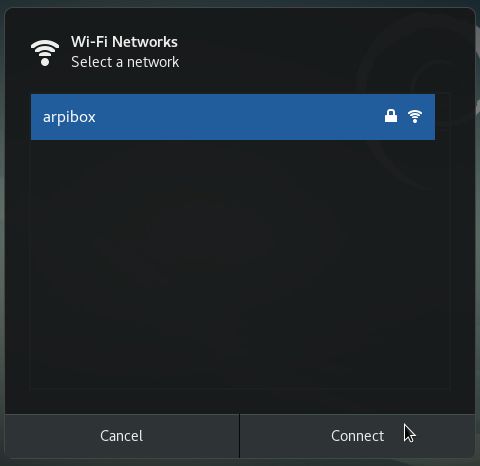
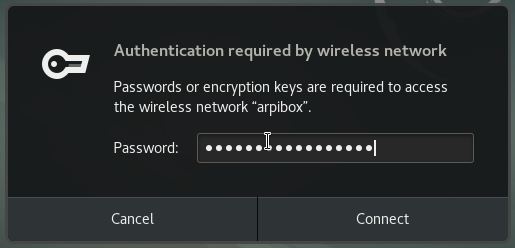
Then enjoy your Wi-fi connection:
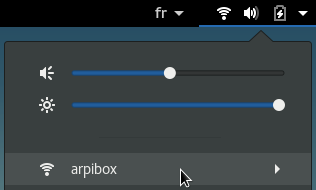
To tweak the Wi-fi settings, select the dedicated entry in the main menu:
You will be able to modify the connection settings, and even “Forget” it:
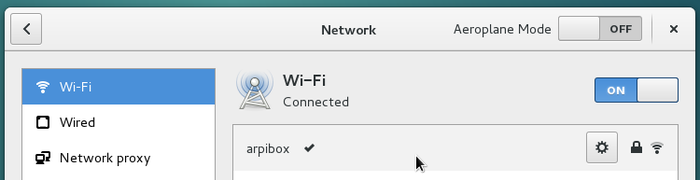
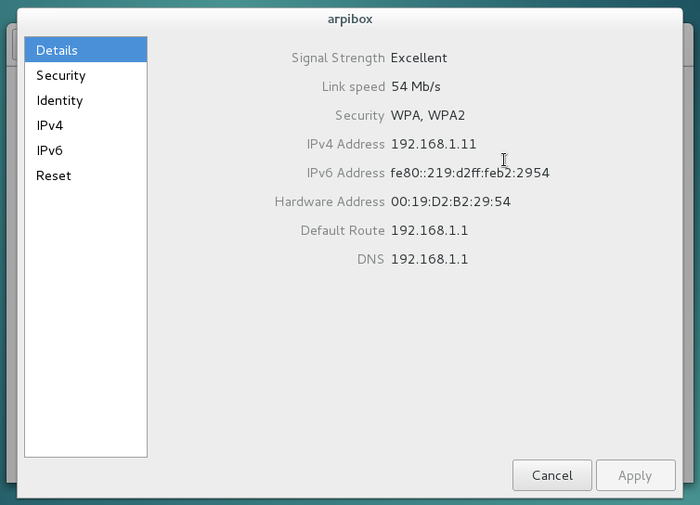
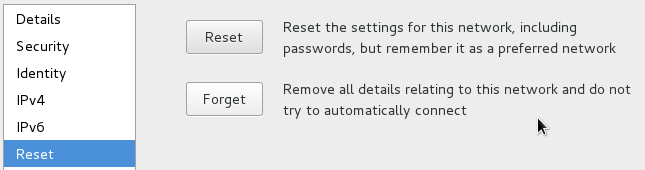
Wicd (https://wiki.debian.org/WiFi/HowToUse#Wicd) (Wireless Interface Connection Daemon) is an independent network manager delivered with LXDE. However, it can be used on any other desktop.
Its interface is slightly different compared to the one of the Gnome manager, but the functionality is the same.
Wicd is available from its icon in the task bar (usually at the bottom right, in the notification area); A left-click opens the main interface which let you select your network access:
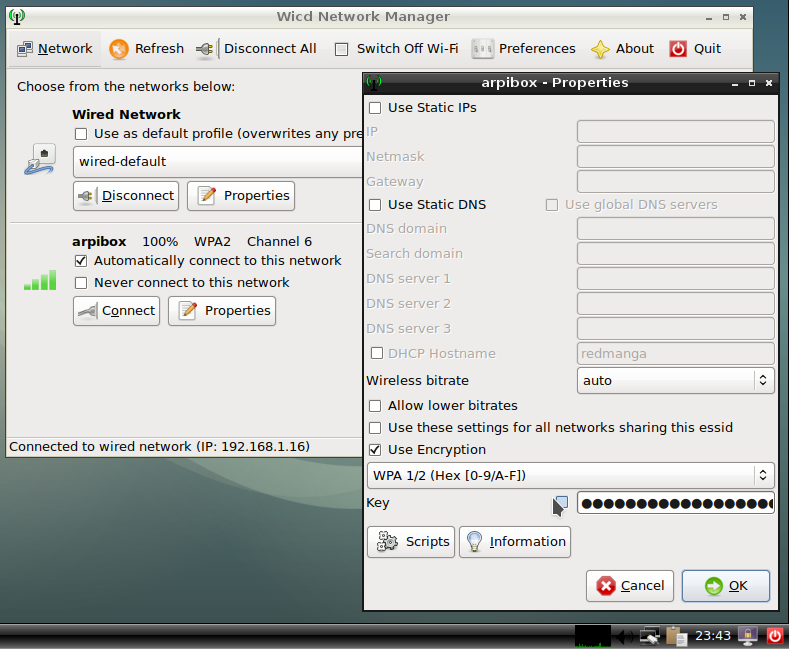
If the network does not show up, verify first that in the Wicd “Preferences”, the right interface (the very one found in the previous chapter: “wlp2s0” for example) is selected for the Wi-fi network.
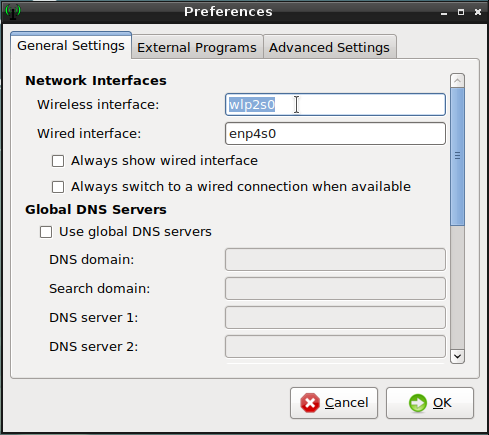
On KDE, the network connections are managed like on the other desktops: through a graphical interface. A left-click on the network icon in the notification area and you access to the list of available networks. A click on “Connect” and KDE ask you to enter the network Wi-fi key:
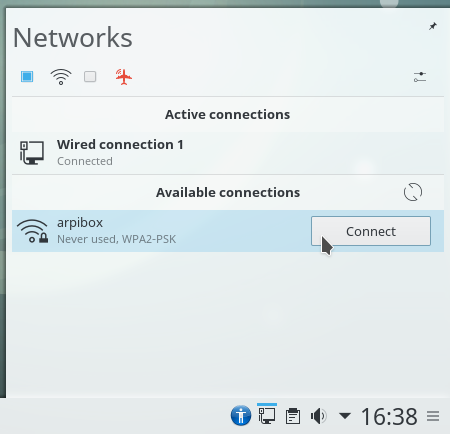
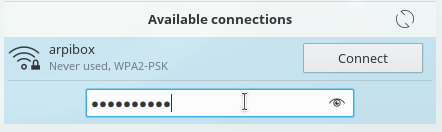
When this is done, you can connect your computer using this Wi-fi network and/or modify its settings.
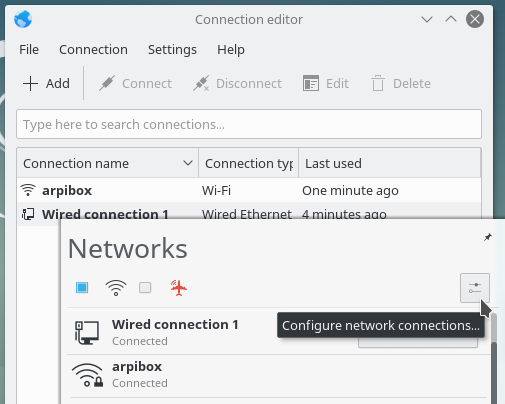
Driver or Firmwares are microprograms often provided by the manufacturer. The kernel must load this driver into the Wi-Fi card itself.
In order to check if the driver is present, we are using the command:
/sbin/ifconfigwhich should return a result like:
enp4s0 Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:xx
BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 lg file transmission:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lo Link encap:Boucle locale
inet adr:127.0.0.1 Masque:255.0.0.0
adr inet6: ::1/128 Scope:Hôte
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:552 errors:0 dropped:0 overruns:0 frame:0
TX packets:552 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 lg file transmission:0
RX bytes:37827 (36.9 KiB) TX bytes:37827 (36.9 KiB)
wlp2s0 Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:xx
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:638993 errors:0 dropped:0 overruns:0 frame:0
TX packets:412031 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 lg file transmission:1000
RX bytes:617235341 (588.6 MiB) TX bytes:42145548 (40.1 MiB)If the interface named something like “wpl2s0” or “wpl2s1” does not appear in the list, this means that the Wi-fi driver is missing.
If your network connection is not functioning, it is usually a driver issue. In order to select the right one, we need to identify first the network device.
Within a terminal, in user mode, launch the command:
lspci | grep -i "net" | cut -d: -f3which will return a result like:
Intel Corporation 82567LM Gigabit Network Connection (rev 03)
Broadcom Corporation BCM4322 802.11a/b/g/n Wireless LAN Controller ...Here, the detected Wi-fi device is the Broadcom BCM4322
If I run a simple Internet search, like “Debian Broadcom BCM4322”, I found quickly the right page (https://wiki.debian.org/bcm43xx) which tells me to install the firmware-b43-installer.
The Wi-fi connection setting is a very touchy subject for the GNU/Linux distributions, due to the non-free nature of the drivers to be installed.
More information on the Debian Wi-fi Wiki: https://wiki.debian.org/éWiFi.

C.U.P.S (https://wikipedia.org/wiki/Common_Unix_Printing_System), is an acronym for Common Unix Printing System, and as its name suggests it, a printer management system created by Apple Inc. for OSX and other Unix-like systems. It is used by default on Debian to manage printers. To achieve this, CUPS uses the Internet Printing Protocol (ipp) to drive both the local and the network printers.
What is enough to remember is that CUPS is the tool managing the printers.
If you chose an exotic installation, you might need to install yourself some Debian packages. Within a terminal in administrator mode (thanks to “su” (chap.3.8.3) :
apt update && apt install --install-recommends task-print-serverCompatibility
Likewise Wi-fi devices, printers need external drivers. However their detection by default is much better, which enables Debian to embed a simplified printer setting interface (detailed in the first section of this chapter). Methods may vary from one manufacturer to another.
To check your printer compatibility, you can visit the dedicated page of the openprinting.org site: https://www.openprinting.org/printers.
![]()
Regardless of the chosen method, don’t forget to plug the power cord at both ends, to verify that the paper tray is not empty, to connect the printer either directly to your computer, or to the local network, and turn its power on.
The Debian GNU/Linux desktops include the system-config-printer tool, a simplified graphical manager to add and configure your printer.
If you followed the Debian classic installation procedure, this tool is already present on your system and can be found usually at “Sysem > Print Settings”, or in the Control Centers for Gnome or KDE. If you don’t find it, simply open a terminal and launch:
system-config-printerIn the first window which opens you can press the “Add” button to add a printer.
Then you access the “New Printer” window which presents the local or network “Detected Devices” list. Select your printer and click the “Forward” button:
If your printer was correctly detected, its driver has been selected for you. You can describe your printer in the next window. Once you are done with the modifications click on the “Apply” button:
The installer then ask you if you want to test the printer:
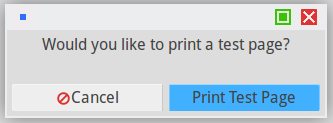
The printer is now correctly added to your machine. It is available for the printing tasks executed by any of the installed applications on your system (LibreOffice, Evince (for pdf files), etc.).
To change your printer settings, double-click on its icon:
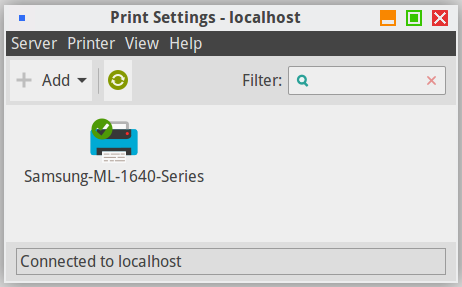
Small hint: to change the printer behavior in case of error, go to your printer settings, click on the “Policies” category, and select the “Abort job” option (instead of “Stop printer”) in the “Error policy” field.
The simplified interface is handy, but the classic CUPS interface is no longer as austere as it used to be. You can access it from your Internet navigator since CUPS is a print server offering a web interface.
So let’s meet on the page http://localhost:631/printers/ which displays all the detected printers (don’t forget to connect your printer either directly to your computer, or to the local network, and to turn its power on).
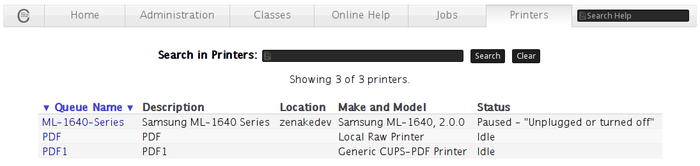
A left-click on your printer opens the dedicated page:
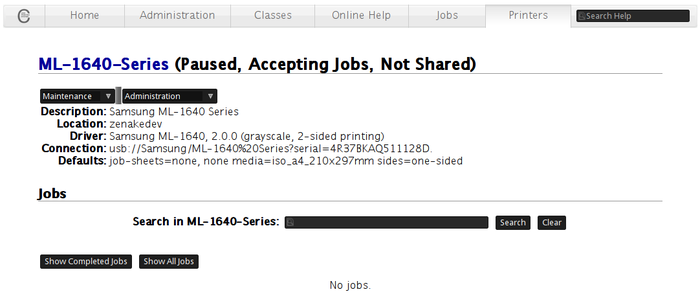
which includes the “Maintenance” and “Administration” menus. Depending on the selected operations, the administrator password will be requested. (chap.3.8.3).
More information of the Debian SystemPrinting Wiki: https://wiki.debian.org/SystemPrinting.

Debian updates have nothing to do with Windows’ updates…
The GNU/Linux system updates are the direct evidence of one of the free software strengths: the public sources.
As opposed to the proprietary systems, hiding their software flaws (since they sell it) as long as possible, the free distributions publish their software flaws as soon as they are discovered and fix them immediately.
So, when a small window suddenly pops up and invite you to update your system, say yes, of course, and your computer will thank you a all lot.
The terminal, this little box which frightens you so much, whereas it is actually your friend … yes yes … your friend.
You want a proof ? Easy: we are going to update the entire system using just one line.
We start by opening a terminal and log in as administrator. That is (depending on your environment) from the Applications menu > System > “Administrator Terminal”, or in the more classic way, open a terminal and type the command:
suIn both cases, the administrator password is requested. Once connected as “root” in the terminal, cut and paste this line:
apt update && apt dist-upgrade![]()
… wait a minute, what does that mean exactly?
The GNU/Linux desktops use Software or the Synaptic package manager on the Gnome, Xfce and LXDE interfaces, or Discover on the KDE interface, and both tools include a notification function.
Thus, your system checks the repositories on a regular basis (when the network is available, of course), without even bothering you and displays a notification at the beginning of a new session when some updates are available. It is enough to accept the updates, or to click on the notification bubble opening up, to display the update manager tool integrated in your system.
If you want to manually check for available updates, you can use the procedure listed at the beginning of this chapter.

If you have an online messaging service like gmail.com or free.fr, you can access it from your Firefox web browser (launches from the application menus in the “Internet” section). Enter the address of your online account provider (openmailbox.org, yahoo.fr, orange.fr, google.com …) in the address bar and launch by pressing [Enter].
If you do not have an e-mail account, or you want to create a new e-mail account, we recommend that you use the services that respect your privacy. For example:
If you are using a local e-mail client, a dedicated software, Debian offers severals tools but all working on the same model: Gnome uses “Evolution”, KDE includes “KMail” and Xfce integrates Thunderbird.

Thunderbird (https://www.mozilla.org/fr/thunderbird/) is primarily an emailer, but it is also a communication hub that allows you to read and write within newsgroups, chat with others (discussion group), and read RSS feeds provided by some websites.
If you have two or more email accounts, it might not be very practical to access each of them using the browser! Thunderbird is an application that brings together all the mail boxes of all your email accounts, in one single convenient interface.
To open Thunderbird, from an application list or a menu, select the “Mail client” from the “Internet” category.
At first startup, Thunderbird provides temporary configuration interface and a foreground window that allows you to create an account with two suppliers and partners.
If you want to take advantage of this option, fill in the fields and let you guide, the configuration will be automatic.
If you are not interested you can click on “Skip this step and use my existing address”.
Another window opens. Then provide the requested information about your account. You can choose whether Thunderbird must remember the password. If you uncheck this option, you must enter your password each time you connect.
Click on “continue”. Thunderbird then searches in its database then specific parameters for your eamil account. When finished click on “done”.
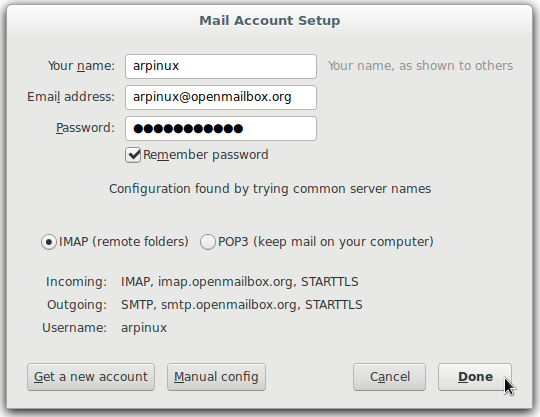
Thunderbird now displays your account details in the right column, starts downloading all your emails and, depending on your provider, all your contacts (this may take sometime). Now click on your account in left pane to unfold it, then on “Inbox”. The interface takes its normal appearance:
The Thunderbird interface is relatively intuitive. In the top tool bar you can check your mail, compose a new message, open a chat session, access your address book, put a label on a message, or filter your messages.
At the right of the menu bar you can find the Thunderbird menu, represented three small horizontal bars, from which you set your preferences, and launch various actions.
For example if you click on the Message menu (or right-click on given message), a list of actions is proposed like Reply, Forward, Archive, Mark as Junk, etc.
The right panel is reserved for the “Lightning” calendar, very intuitive: a click on a date will open the assistant to make appointments.
If you are looking for a specific message you have several options:
If you have more email accounts you want to access via Thunderbird, click on the main menu (the three small horizontal bars at the right of the tool bar) and select “New Message” > “Existing Mail Account …” and continue the Mail Account Setup procedure like explained above.
In the modern presentation of Thunderbird (as well as other communication tools like Firefox and Chromium, for example) the application menu is define by the three small horizontal bars at the top right of the window. From this menu you have access to the parameters of the application.
If you prefer the classic presentation, with the menu bar at the top of the window, click on this Thunderbird menu and then “Preferences” and tick “Menu Bar” on.
It is advisable to visit the Preferences setting window, where you can define the handling of junk mails, define a master password for all your account, customize your tag list, among all the settings available in there.
![]()
… Encrypt your e-mails … what does that mean?
Let us take the example of the regular mail, sent via post-mail. You send a postcard to your mother-in-law for example, you know that what is written on it can be read by the postman or anyone else. Well, with your e-mails, it’s exactly like the postcard,if you do not encrypt them.
“Does not matter” you say, “I don’t care if someone knows that I wrote to my mother-in-law that the weather is fine during our vacations”. Perhaps. But you can write more than just mundane wordings in your messages, and you never know what can happen to them. You are not convinced? I ask you to reconsider if you really have nothing to hide by visiting this page on the FSF website: https://emailselfdefense.fsf.org.

To effectively protect your electronic exchanges, use EnigMail!: https://emailselfdefense.fsf.org.
GNU/Linux systems follow the principle of rights and permissions by default. When you install Debian, a password is requested for the primary user. This password is requested at the beginning of the session.
If you are using Debian in single-user mode, you can disable this password request in order to begin your working session directly when the computer is started.
Debian uses three different default connection managers: GDM (on Gnome & Cinnamon), LightDM (on MATE, LXDE & Xfce) and SDDM (on KDE).
GDM3 (https://wiki.debian.org/GDM) is the default Gnome Display Manager for the default desktop environment on Debian 9 “Stretch”. To enable automatic login:
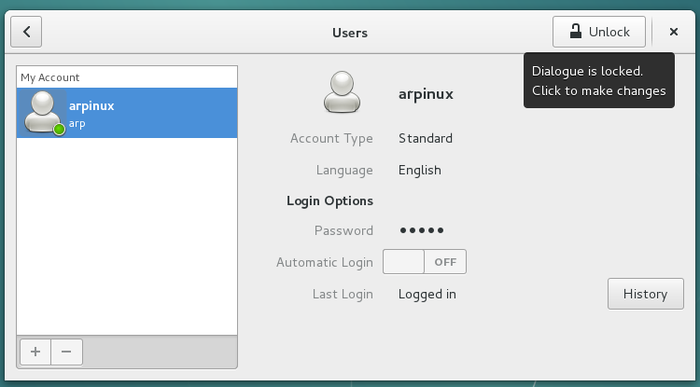
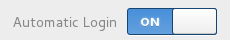
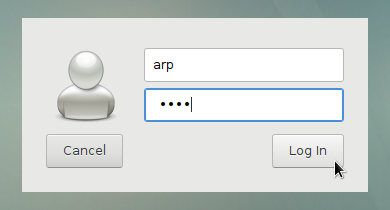
You can setup LightDM (https://wiki.debian.org/LightDM) by editing its main configuration file. To enable autologin, you’ll have to edit it with a root terminal (chap.3.8.3).
Open a terminal and become root with the “su” command. The administrator password will be asked. Once connected in root terminal, copy (to backup) and edit the dedicated file with in 2 commands:
cp /etc/lightdm/lightdm.conf /etc/lightdm/lightdm.conf.bak
nano /etc/lightdm/lightdm.confThe second command opens the configuration file in the CLI Nano editor. Use arrows to scroll and locate those lines:
#autologin-user=
#autologin-user-timeout=0Remove the “#” (uncomment) in front of each line then add your login like that:
autologin-user=my_login
autologin-user-timeout=0With “my_login” remplaced by your login.
Save the file with the [Ctrl]+x shortcut, then answer “Y” for “yes”:
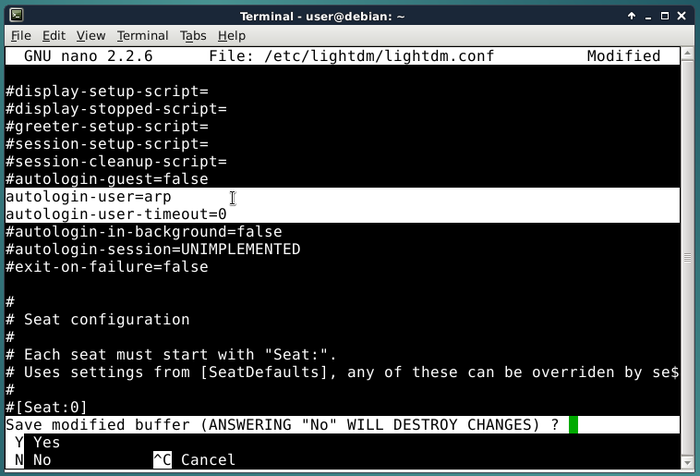
You can close your terminal: your password won’t be asked anymore at login time.
In case of troubles, just enter this command in administrator mode to restore your previous LightDM configuration:
mv -f /etc/lightdm/lightdm.conf.bak /etc/lightdm/lightdm.conf
KDE is a truly complete environment and SDDM (Simple Desktop Display Manager) provides you with a graphical interface to configure your login screen. The configuration tool will allow you to manage the wallpaper, the language used, some options and of course, the automatic login.
To access SDDM configuration, direction the main menu > Applications > Settings > System Settings > Startup and Shutdown:
Enable automatic login from the “Advanced” tab of the SDDM configuration interface:
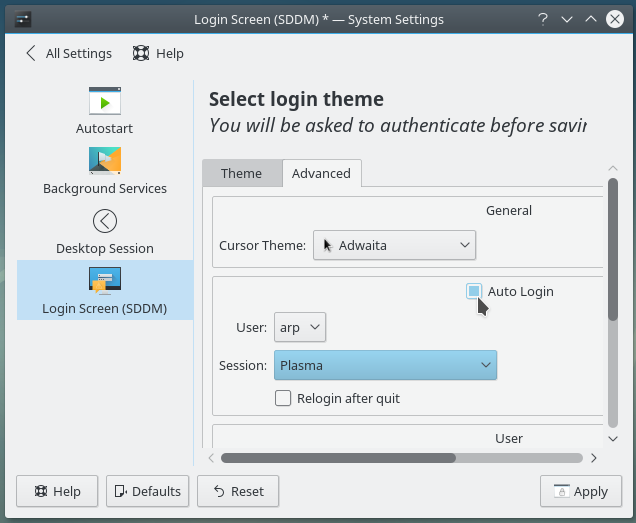
Select the “Automatic login” checkbox and select the user from the “User” drop-down menu. As this action changes the system settings, you will be prompted for the administrator password. On next login, your password won’t be asked.

The primary function of a web browser is to let you consult information available on the Web (World Wide Web).
The user gives the browser the web address of the resource to consult. There are three ways to give a web address:
The browser connects to the web server hosting the target resource. The communication protocol commonly used is HTTP or HTTPS (secure version).

Firefox (https://www.mozilla.org/en-US/firefox/desktop/) is an open and free web browser, developed and distributed by the Mozilla Foundation (https://www.mozilla.org) with the help of thousands of volunteers using the free software/open source development methodology (dixit wikipédia).
Debian integrates Firefox-ESR, the “Extended Support Release” version, aimed at large organizations (and small ones) for mass deployments. This version is maintained for 10 months from its release date and only benefits from security updates, ensuring a stable and secure browser.

The main window consists of the following elements (from top to bottom):
Customize and configure Firefox through its main menu that appears when clicking on the 3 bar menu icon (at the right end of the tool bar):
To add features to your Firefox browser, navigate to Preferences > Add-ons. In the tab that opens, select “Get Add-ons” and choose from the available modules (https://addons.mozilla.org/fr/firefox/extensions/).

Debian GNU/Linux comes with a video player on each Desktop Environment (DE like Gnome or Xfce). Debian natively recognizes most common video formats (ogv, mkv, mp4, avi, webm, etc).
Once your system is installed (or in Live session), a double-click on a video file will open it with the default player of your DE.
For Gnome or Cinnamon, it’s the “Videos” player (Totem) that is automatically launched when double-clicking on a video:
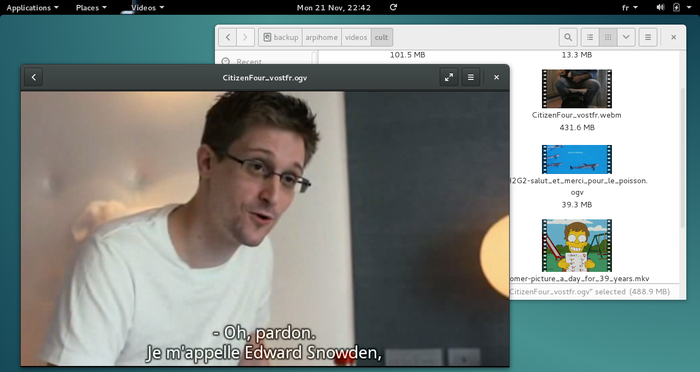
Its use is very simple and intuitive. At the slightest movement of the pointer, the playback menu is displayed and allows you to browse the video file, set loop playback (the vertical bar formed by 3 points) or adjust the volume. The main menu gives you access to other functions:
Each DE integrates its own player, all featuring the same basic functions, largely enough for a first use of a Debian system.
As usual on Debian, you can add the multimedia software of your choice. I’ll let you visit the list of applications available on the Debian wiki (https://wiki.debian.org/Multimedia).
The Xfce desktop comes with a multi-platform media player widely used by Windows®: VLC (https://www.videolan.org/vlc/), a way to get started on Debian without changing your habits.
VLC is a free media player and a system capable of playing most multimedia files as well as DVDs, Audio CDs, VCDs, and various broadcasted protocols.
VLC can also play network streams (podcasts), listen to an online radio, capture the screen, as well as encode a stream to save it.

Debian GNU/Linux comes with a media player for each DE. Some allow the management of a large music library, including sort management, play lists, cover artwork, etc (such as Amarok or Rhythmbox described in the following section), others are simple, lightweight and easy to master (Such as Audacious http://audacious-media-player.org/ or XMMS https://xmms2.org/wiki/Main_Page).
Wikipédia is my friend …
An audio file format is a file format for storing digital audio data on a computer system. The bit layout of the audio data (excluding metadata) is called the audio coding format and can be uncompressed, or compressed to reduce the file size, often using lossy compression. The industry has produced many formats for either production or distribution
The program element which transforms the signal into a file and the file back into a signal is called a codec (https://wikipedia.org/wiki/Codec), an abbreviation for coder-decoder.
Debian recognizes (among other things) the 4 main default formats (mp3, ogg, flac, wav). If you need to install codecs or non-free audio software, you will need to modify your repositories (chap.8.1.3) to add the “contrib” and “non-free” sections.
Rhythmbox (https://wiki.gnome.org/Apps/Rhythmbox) is the default music player in the Gnome environment, which allows you to play and organize your music collection.
Here are its main features:
At first launch, Rhythmbox scans your “Music” folder, but you can add more folders to your music library.
Rhythmbox integrates a plugin system that adds functionality to the player.
Default audio player of the Gnome desktop, it benefits from a complete integrated help:
The main desktops also have their dedicated player, which works on the same principle: a music library scanned by the application which offers you simple reading or by “playlists”, options, preferences and plugins.
Let your mouse wander, you do not risk anything: a confirmation will be asked for each action involving the modification or the deletion of your musical files.

Debian integrates by default the full office suite LibreOffice which allows you to work on documents of any type format coming from different office suites.
If you don’t need such a comprehensive tool suite, you can use the Abiword (https://packages.debian.org/stretch/abiword) or Gnumeric (https://packages.debian.org/stretch/gnumeric) tools, lighter while maintaining a high level of compatibility.
LibreOffice (http://libreoffice.org/) is a free (as in freedom) office suite that offers tools for word processing (Writer), spreadsheet (Calc), presentation (Impress), drawing (Draw), database (Base) and editing mathematical formulas (Math).
LibreOffice is the default office suite for Debian 9 and will be integrated with the main desktops.
There are many possibilities for LibreOffice. The official wiki of the community is very well done and will provide you with an efficient and complete help (no need to reinvent the wheel …): https://wiki.documentfoundation.org/FAQ
Good reading.
Debian includes the graphic manipulation software the Gimp.

GIMP, standing for GNU Image Manipulation Program, is an image processing software. Often considered as a competitor of Adobe™ photoshop™, it is, at any rate, a safe alternative with all the same functionalities, and, on top of it, it is free!
Available for a whole range of OS, it runs naturally on Linux, MacOsX, BSD and Windows®.
There are already very good documentation concerning The GIMP, and this page is only to gather, in few lines, the most basic hints, without having to browse through dozens of sites hoping to find its happiness.
At first launch, Gimp displays 3 windows with several elements:
1 The tools box - 2 The tools options - 3 The Gimp menu bar - 4 The active picture - 5 & 6 The tabs displaying the values of tools and layers.
By default, the first tab displays the active layers in the image.
![]()
… What does those “layers” exactly means??
Gimp uses the principle of layers, ie the superimposition of images for a final rendering. It is the same principle as recording a piece of music: the instruments are all recorded on separate “audio tracks”, the voices also, then “mixed” all together to obtain the final piece of music.
For the layers of Gimp, it is the same: you separate the different elements on layers and the final image will be exported in the format of your choice (JPEG, PNG …).
The default format of Gimp is “xcf”, a format that allows to preserve the independence of the layers and thus, to be able to modify an element without touching the other layers.
Prepare a folder with a copy of the images to modify:
It is often said, the backup is your friend and it is also true for image editing. Before working on your project, create a folder where you will place a copy of your original image as well as all the elements you want to add (other images to process, modify, your graphics resources in short).
Record your work regularly in “.xcf” format:
Gimp uses the default “xcf” format to save your project. This format allows to save the layers and therefore, permits a fine modification of your work. To save in xcf format, direction the menu “File”> “Save”. Once your project is finalized, you can export your project in a compressed format (jpeg, png, gif) from the menu bar: “File” > “Export as”.
Switch to single-window mode:
If the default interface with its 3 windows disturbs you, Gimp has provided a “single-window” mode available from the menu “Windows” > “Single window mode”.
Have Fun!
One way to discover the Gimp is to test, try, have fun editing your family photos for fun… Create a folder to play with Gimp and place your favorite photos or images and start to gimp-it
Tutorials
The Gimp website provides a large choice of tutorials where you could start to play: https://www.gimp.org/tutorials/
Print an image
If Gimp prints only white pages, and the preview is desperately showing a blank page too, you can fix this problem by installing the gimp-gutenprint package in administrator mode (chap.3.8.3) :
apt install gimp-gutenprintThen, to print a image, all you have to do is: “File > Print with Gutenprint”. A page is open where you can set up your printer and print layout.
 Tweaking of your environment
Tweaking of your environmentDo you feel you took control of your system ? Now we are going to tweak the configuration of your workstation.
Basically, you can modify everything you want on the Debian GNU/Linux desktops and tailor your environment to make it fit your personal needs and tastes.
To achieve this, the right-click is the quasi-ultimate weapon !

The GNU/Linux environments are known for their great flexibility in terms of configuration. However, some desktop are more flexible than others, because of their main interface.
Grossly speaking, they all work the same way: a “Control Center” to handle them all in the same place, and the right-click for the settings of individual elements.
Most of the functionalities have been addressed during the presentation of the desktops (chap.4.2). But let’s return to the two Debian main desktops: Gnome and KDE.
Gnome is the default desktop for the Debian installations. This desktop features an “all-in-one” interface which makes it a fluid and intuitive environment.
Gnome-Shell (https://wiki.debian.org/GnomeShell) provides a “uniform” interface: this is what brings this great fluidity. This means also that you will not be able to modify everything you want, like on the other desktops built with a modular design. But instead of talking about the few things you cannot make, let’s talk about all the settings available to you.
Let’s take the direction Gnome Activity menu > “Tweak Tool”.
The opening window includes all the elements of your Gnome-Shell desktop. The changes are applied and visible immediately.
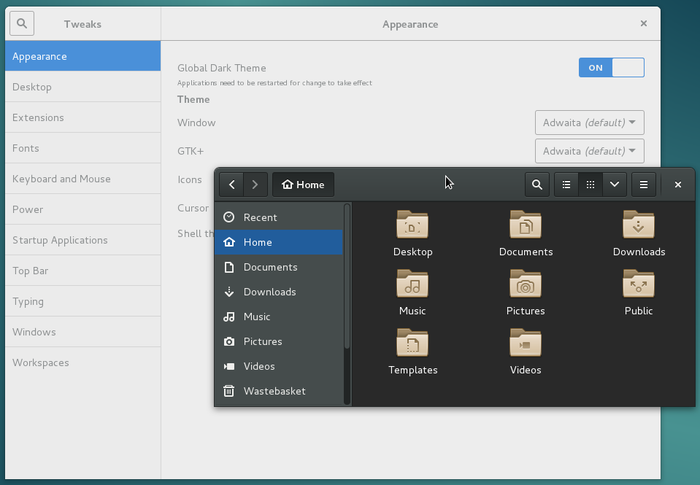
After few “clicks” on the various categories, you will easily understand how to install, in the top bar, the Application menu, the Places menu or the weather forecast.
Gnome-Shell is enhanced with various extensions available in Debian repositories. To install them, run the software manager, category “Add-ons”… simple isn’t it?
You still have to make your choice in the list: a left click on an extensions and “Software” offers installation. You will be asked for confirmation.
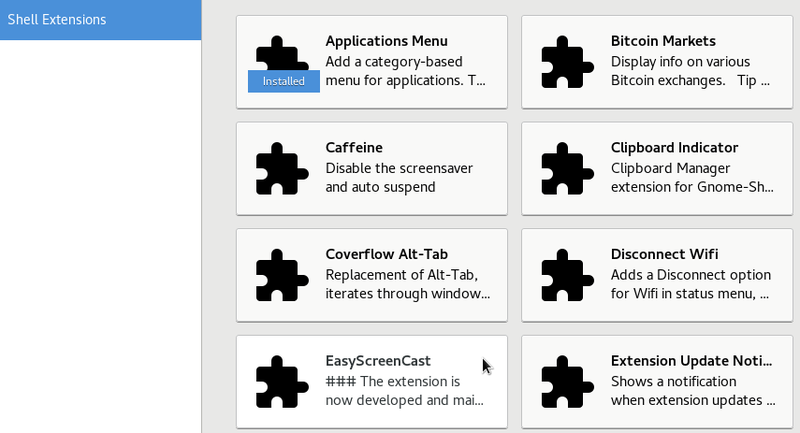
Your extension is immediately accessible, here with the extension “Screencast” which allows to record a video of your working session:
In order to be more efficient, and even if Debian is “mouse-click-oriented”, we suggest you use the keyboard shortcuts: pressing the “Windows” key, for example, switch between the Activities overview and desktop. The overview displays the open activities, the dock and the virtual workspaces.
| Shortcuts | Actions |
|---|---|
| Alt + F1 ou Win | Switch between the Activities overview and desktop |
| Ctrl + Alt + Tab | Give keyboard focus to the top bar |
| Alt + F2 | Pop up command window |
| Alt + Tab | Quickly switch between windows |
| Alt + Maj + Tab | Idem, but in reverse order |
| Alt + ² | Switch between windows from the same group |
| Ctrl + Alt + ↑/↓ | Switch between workspaces |
| Ctrl + Alt + Maj + ↑/↓ | Move the current window to a different workspace |
“Gnome Settings” is available from the Parameter launcher and gives you access to all the settings of your environment.
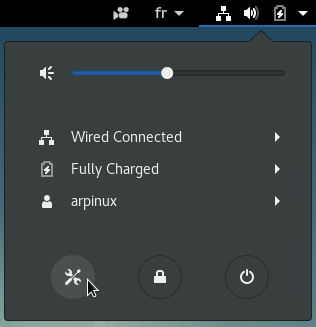
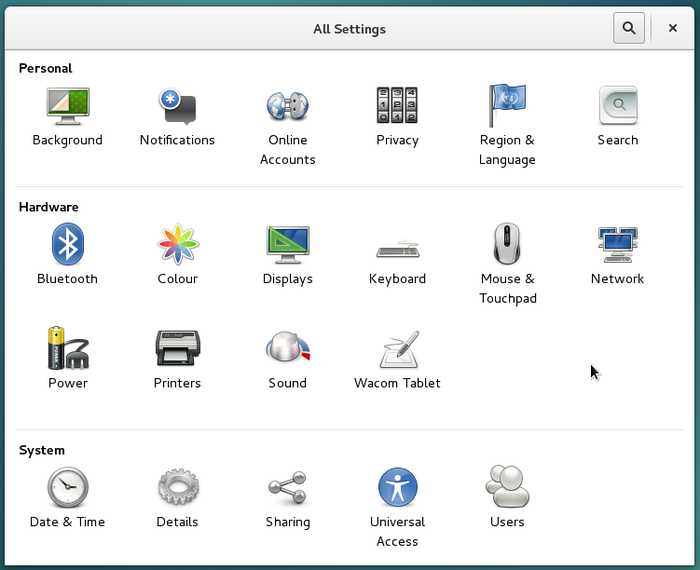
If you want to use a more “classical” interface, you can take this option during your session sign in: click on the little gearwheel to select the “Gnome Classic” option before pressing the “Sign In” button:
Your session then opens with a more conventional version of Gnome, but you keep your main settings and your tools.
The “Classical” interface is lighter, but offers less visual effects (usefull or useless, depending on the view point)
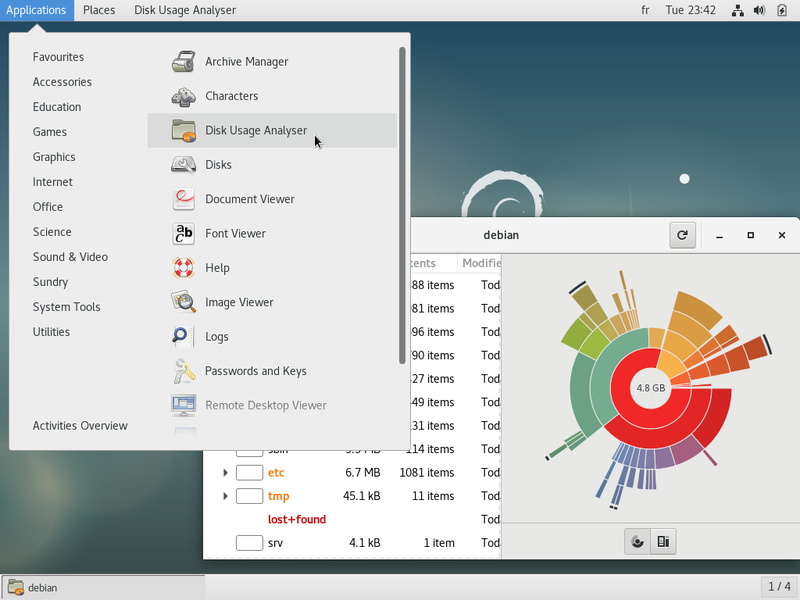
In order to come back to the default Gnome-Shell interface, select the “Gnome” option of the gearwheel menu, next time you Sign In.
KDE is one historical desktop for the GNU/Linux environments, and did always put the emphasis on its extreme customization. The transition to the Plasma (https://www.kde.org/plasma-desktop) rendering engine did not change a bit on that point: everything on KDE is modular, movable, configurable, and accessible from a very detailed System Setting Center.
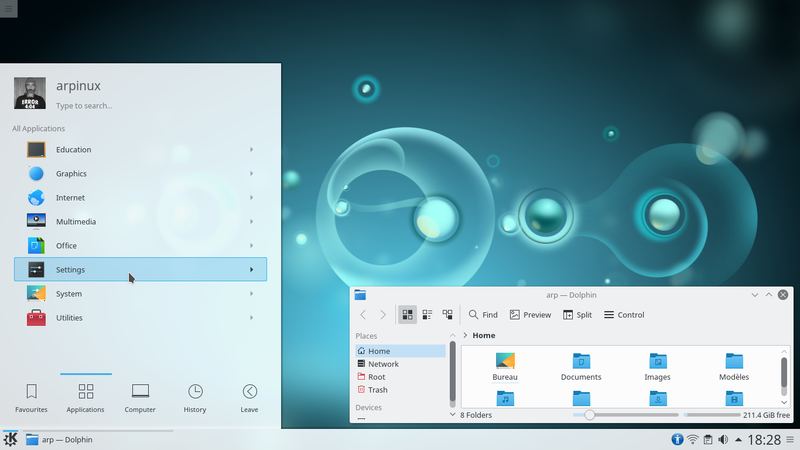
This is where you are going to tweak all your computer and Debian system settings.
Network, audio, video, window appearances, default language, and also the way you sign in, and a lot more … Virtually everything is configurable from this panel. Even some desktop special effects integrated in KDE, in Compiz style, can be managed from here.

Each entry is detailed and you will discover as the configuration possibilities of the KDE-Plasma environment.
If you wish a more “out-of-the-box” like environment, and if your computer configuration allows it, you should prefer Gnome or Cinnamon which offer less detailed (and less complex) interfaces.
Plasma allows you to add graphic components to your desktop, sort of small ‘widgets’ that display virtually anything on your desktop. From the launcher at the top left corner or right-click on the desktop, select “Add Widgets” and then drag and drop the desired components to your desktop.
To configure the widgets, left-click on the relevant component to bring up the configuration menu. You can then adjust the component, move it or resize it to your liking.
The Activity manager let you organize your tasks and keep an eye on them. To access it, left-click on the top-left corner menu or right-click on the desktop:
The activity banner will then appear at the left of the screen and display the current and pending activities. Each activity can be configured to separate your tasks and associate certain settings (for example, deleting the browsing history).
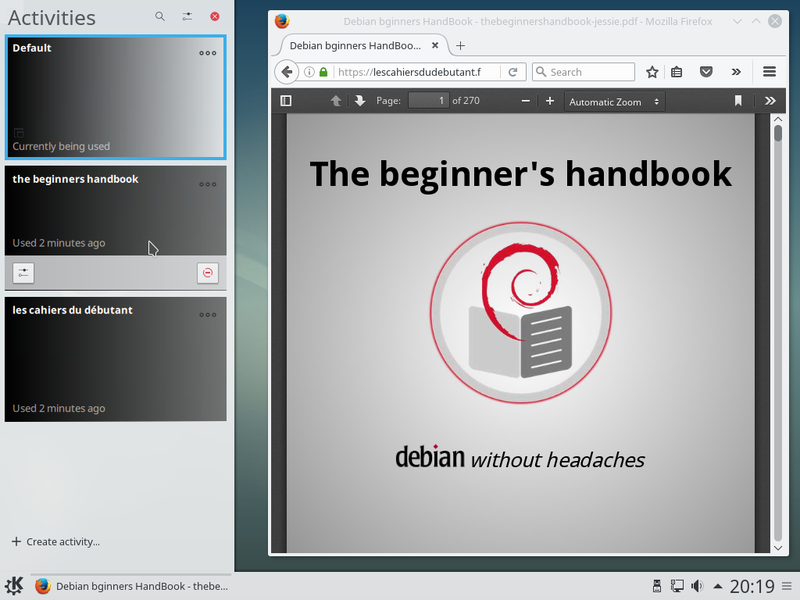

The configuration of your system directly impact you user experience. Instead of writing a complete chapter about the different ethical and technical concepts which led to the Debian software organization, we are going to examine their consequences on your daily usage.
In the rest of this chapter, you might be asked to activate the “contrib” and/or “non-free” sections of the Debian repositories, in order to access some “less-free” software. In that case, follow the method documented in the chapter 8.1.3.
During the installation, Debian ask you to enter the password for the “root” administrator account. This account is common to all the GNU/Linux systems and allows to execute administrative tasks on the system.
However, this account is not mandatory. During the installation process, you can pass over the the “root” account configuration (leave empty the root password fields), and doing so, avoid its creation.
In this case, this is the first user registered during the installation who will assume the “root” role.
OK… and then?
Then, this changes the way you launch commands to administrate the system: in this manual, every time we ask you to execute a command in “root” mode, we use the “su” command. But if the “root” account was not created, you must use instead the “sudo” command, which switch you and “root”, and give your own password.
In a nutshell to launch an administrative command:
If the “root” account was created, use “su” + administrator password + command launch:
su
> asking administrative password
apt update && apt upgrade
> command executionIf the “root” account was NOT created, use “sudo + command” + your user password:
sudo apt update && sudo apt upgrade
> asking first user password
> command executionThe DVDs sold commercially are “copy protected” and usually are not readable by default on free systems.
The Entertaining Companies consider that we do not have the right, on a free system, to make a private copy of the DVDs we bought … no comment.
To remedy that, if you really need this functionality, you must install the libdvdcss2 package. This package is not present by default in the Debian repositories, but you can find it in the repositories of Videolan (the site of VLC, the well known multimedia player).
The principle consists in adding the Videolan repositories to your system, adding the signature keys to secure the communication with these repositories and finally installing libdvdcss2.
In practice: 3 commands and that’s it!
1 Open a terminal in administrator mode (chap.3.8.3) with su, then launch this command to add the Videolan repositories in a separate file:
echo "deb http://download.videolan.org/pub/debian/stable/ /" > /etc/apt/sources.list.d/videolan.list2 Add the repositories signature key:
wget -O - http://download.videolan.org/pub/debian/videolan-apt.asc | apt-key add -3 Reload the repositories and install libdvdcss2:
apt update && apt install libdvdcss2You can realize these modifications in graphical mode only, by using the Synaptic package manager, but it takes a lot of time to click with the mouse all over the places …
Your Debian GNU/Linux system is now able to read the “protected” commercial DVDs, and to make private copies of them.
Adobe Flash Player is a non-free platform used to add animation, video, and interactivity to Web pages. Flash is frequently used for advertisements and games.
A free reader exist: Gnash (https://packages.debian.org/stretch/gnash). It is an alternative to the Adobe reader but does not allow to have access to all the Flash functionalities.
Be aware that the current trend for site developers is to move away from flash in favor of HTML5 (https://fr.wikipedia.org/wiki/HTML5), thus it is more and more easy to survive on the Internet without the proprietary flash player.
This manual being intended for beginners, we are not going to ask you to remove all the bookmarks pointing to sites still using the flash reader (although that could help making a faster transition), so we will detail below how to install the flash player from Adobe website
To update your flash player, retrieve the latest version in the same way, and overwrite the old file with the new one, simply.
The Debian GNU/Linux system includes free drivers and some firmware in order to operate the integrated graphical functions (chipsets) of the motherboard or the external graphical card.
![]()
… I need a driver to manage the card of my mother ??
Your computer is designed around its “motherboard”, a plastic board on which the various elements of the processor (the central compute unit) are fixed, as well as the chipsets, the graphical component being part of them (the graphical display computer, to make a long story short).
In order to send the right instructions to these elements the GNU/Linux kernel (the program managing the interactions of the hardware with the system) uses pieces of code, called drivers (and sometimes “firmware” to be loaded on smart devices during the initialization phase). The Linux kernel includes by default a set of free drivers. These drivers are usually sufficient to manage the screen display. But it may happen that proprietary drivers are needed to optimize the screen resolution.
You can try to install these proprietary drivers if, during a live session or once your system is installed, you find out that:
Please note that installing proprietary drivers is a non-free alternative, and as such, not followed by the Debian developers. If your computer is very recent, don’t hesitate to ask the support of the community before tinkering with your system (chap.1.2).
The first thing to do is to identify your graphic device (or graphic card). Open a terminal as simple user, and enter the following command:
lspci | egrep "3D|Display|VGA"which will display this kind of result for a nVidia controller:
01:00.0 VGA compatible controller: NVIDIA Corporation G96GLM [Quadro FX 770M] (rev a1)or this kind of result for an ATI controller:
01:00.0 VGA compatible controller [0300]: Advanced Micro Devices, Inc. [AMD/ATI] Barts PRO [Radeon HD 6850] [1002:6739]but what doest that mean?
lspcilists the devices connected to the PCI bus and
egrep "3D|Display|VGA"selects only the information we are interested in, rather than displaying everything. Here we are looking only at graphical components.
As you can see the identification is rather easy … we got the manufacturer and the model on the same line. Should you have the slightest doubt concerning the installation of additional drivers, don’t hesitate to ask the Free Community for help (chap.1.2).
In all cases, and before the installation of any proprietary driver, you should add the non-free firmware delivered by Debian. To add the Debian non-free firmware to your system, start with modifying your repositories (chap.8.1.3) by adding the contrib and non-free sections to your sources.
Open a terminal in administrative mode (voir chap.3.8.3) with the “su” command (the administrator password is requested), then launch the command:
apt edit-sourcesModify the sources.list file by adding the contrib and non-free section, like this:
###### Debian Main Repos
deb http://deb.debian.org/debian/ stretch main contrib non-free
###### Debian Update Repos
deb http://security.debian.org/ stretch/updates main contrib non-free
deb http://deb.debian.org/debian/ stretch-updates main contrib non-freeSave your modifications with [Ctrl]+x in the Nano text editor, then “Y” for “Yes”.
Reload the repository informatin, and install the non-free firmware:
apt update && apt install firmware-linux firmware-linux-nonfreeRestart your machine to test again your screen display before installing the proprietary drivers.
If no real improvement is noticed, continue with the following sections … The sources.list file is already set for the next steps.
ATI driver
This is the “generic” driver to install if your card is not listed in the specific sections (Radeon, Catalyst).
To install it from an administrator terminal (chap.3.8.3):
apt install libgl1-mesa-dri xserver-xorg-video-atiRestart your computer to load the microcode (firmware) of the graphic peripheral.
Radeon driver
the Radeon driver of Debian 9 “Stretch”, supports the graphic processors from R100 to Hawaii (Radeon 7000 - Radeon R9 290). See the Radeon package page https://packages.debian.org/stretch/xserver-xorg-video-radeon to verify your card.
To install it from an administrator terminal (chap.3.8.3):
apt install libgl1-mesa-dri xserver-xorg-video-radeonRestart your computer to load the microcode (firmware) of the graphic peripheral.
For non-supported cards here and for more information, visit the official Debian documentation: https://wiki.debian.org/ATIProprietary.
Debian uses a software tool to detect and indicate the driver to be installed: nvidia-detect.
To install and use it, open a terminal in administrator mode (chap.3.8.3), then launch:
apt update && apt install nvidia-detectTo launch the detection, simply launch the command:
nvidia-detectwhich will return this kind of result:
Detected NVIDIA GPUs:
01:00.0 VGA compatible controller [0300]: NVIDIA Corporation G96GLM [Quadro FX 770M] [10de:065c] (rev a1)
Your card is supported by the default drivers and legacy driver series 304.
It is recommended to install the
nvidia-driver
package.In this example, the card is natively supported by the default driver and by the “legacy series 304” driver; Depending on your machine, you can install two types of drivers: the 340.xx series (for the GeForce 8x and more) and the 304.xx series (for the GeForce 6x and 7x). Older models are supported natively by the free driver.
For a complete list of the supported cards, visit the dedicated documentation: 340.xx series page (http://us.download.nvidia.com/XFree86/Linux-x86_64/340.65/README/supportedchips.html) - 304.xx series page (http://us.download.nvidia.com/XFree86/Linux-x86/304.125/README/supportedchips.html)
For details on the installation procedure and supported cards, refer to the official Debian documentation page: https://wiki.debian.org/NvidiaGraphicsDrivers
If, following a driver installation, you are facing a black screen, you need to return to the previous configuration.
Boot in “recovery mode”: from the Grub loader menu, select the “Advanced options” entry and then the “recovery mode” entry.
The system launches a console and invite you to continue the startup sequence (by using the [Ctrl]+d short-cut to quit the console) or enter the administrator password, and this is what you do:
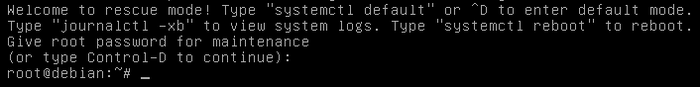
Removal of the xorg.conf configuration file: during the installation of the proprietary driver, you created a X configuration file located in /etc/X11/xorg.conf and/or /etc/X11/xorg.conf.d/xxx.conf. It must be removed. Always from the console and depending on the file created, remove it with the command: “rm”:
rm /etc/X11/xorg.conf.d/20-nvidia.confHere this is the file corresponding to nVidia which was removed, !! to be adapted to your situation !!.
Uninstallation of the proprietary drivers: The same way you were able to install a driver, you can uninstall it, here an example with the nVidia driver, !! to be adapted to your situation !!:
apt remove nvidia-kernel-dkms nvidia-driverRestart your computer with a simple
systemctl reboot
If you are not the only user of your computer, you can create new user accounts in order to preserve your data and preferences. By adding a new user, a new folder will be created in the system. This folder, named by the pseudo of the new user, will receive the default parameters delivered during the system installation.
It will be readable (you can consult the data of the other user) but not writable (you cannot create or modify its data).
Debian includes a simple graphical tool to execute this task, but you can also use the terminal and the “adduser” command (described in the next section).
From a menu or the application list, “System” category, select “Users and Groups”:

The window which opens, displays the detailed information of your user account. You can then modify the parameters of your account, or create a new account. But you need first to “unlock” the application by clicking on the lock button at the top, and enter the administrator password.
To add a new account, click on “Add” (or the “+” button) at the bottom of the left panel:
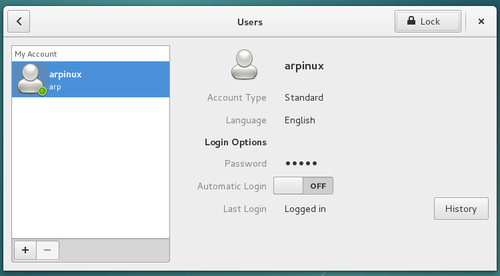
You must enter the full name of this new user, as well as its username (the pseudo or login name used when connecting to a new session). On the Gnome system, you can let the user to define its password during the first connection, or enter it immediately:
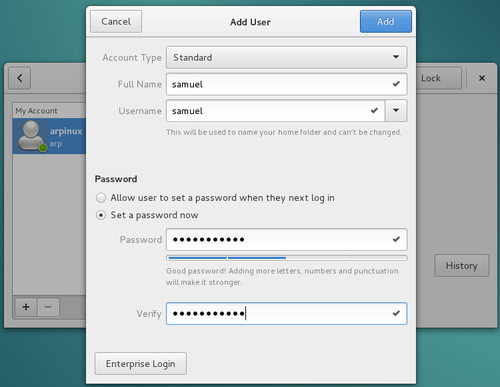
The user account is created … and here you go:
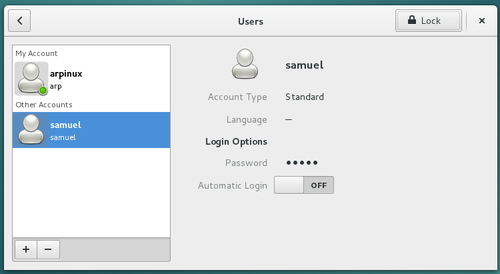
Advanced settings allow you to define the rights and permissions for each user.
Open a terminal in administrator mode (voir chap.3.8.3) enter the command which creates the new “username” account. Note that you should enter here the user ID (or pseudo), not the full name which will be asked later on:
adduser username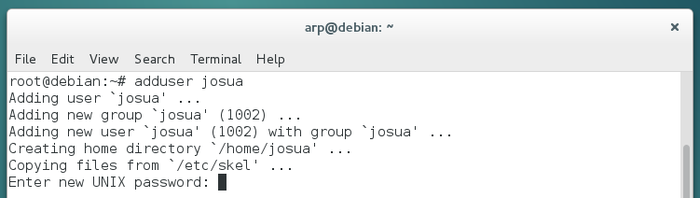
The user account creation process is started and you must enter the password twice (without any echo, its normal).
Once the account is created, we can enter additional information: full name, room number, work phone, home phone, and any comments in the “Other” field.
Once done, a confirmation is requested. If these information are correct you can type [Enter] or Y to finish the account creation process:
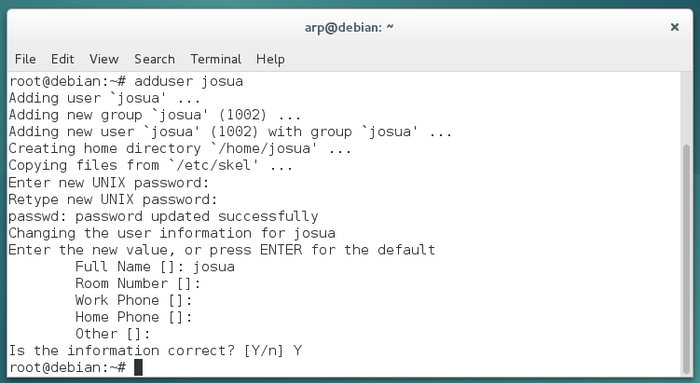
This new user will be able to login with its username and password at computer startup. It will be able to store and manage its data and configure its environment without any risks for your own data and preferences.
 System administration
System administration
Debian GNU/Linux uses the repository methodology to distribute applications. This methodology allows the software centralization and the usage of simple interfaces to administrate and upgrade your system: you have no need to visit the software sites themselves.
The Internet addresses of the Debian repositories are stored in the /etc/apt/sources.list and the files of the type /etc/apt/sources.list.d/xxx.list.
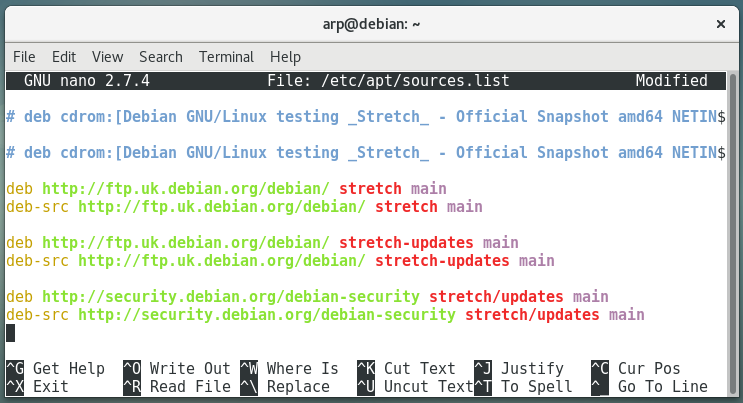
Details concerning the various information found in the ‘sources.list’ file (the lines beginning with a “#” are just comments):
![]()
… why “stretch” and not “stable” since the system is based on Debian Stable ??
“stretch” is the precise version name of the installed system. It sets a given version of each packages included in the “stretch” repository (the version of the generic kernel, for example).
“stable” is the generic name of the currently stable.
For the time being, “stretch” is the “stable” version, thus you could used either designation. But when the Debian “stable” version becomes “buster”, then “stretch” will change to “oldstable”.
Using the precise name of your version allows you to control if and when you want to upgrade your system to the next version, as opposed to some systems which want to impose their upgrades…
For more detailed information, I invite you to visit the dedicated Debian wiki https://www.debian.org/releases/index.html
Debian organizes its software within repositories. These repositories are divided into branches and sections/components. To learn more about the “testing” and “unstable” branch read the chapter 8.8. One word, however, about the sections/components in the repositories.
There are 3 sections in the official Debian repositories:
| section | component selection criteria for the packages |
|---|---|
| main | complies to the DFSG without any “non-free” dependency |
| contrib | complies to the DFSG with some “non-free” dependencies |
| non-free | does not comply to the DFSG |
DFSG (Debian Free Software Guidelines) : principes du logiciel libre selon Debian (https://www.debian.org/social_contract.html#guidelines)
Only the packages within the main section/component are officially supported by the Debian project and are 100% free software. Rather, those proposed in contrib and non-free are partially or totally non-free.
Having said that, and depending on your type of hardware, it is very possible that some services do not function correctly without using specific (proprietary) drivers. In that case, you need to modify the /etc/apt/sources.list file (details in the following chapter)
Before you start modifying the software sources of your system, you must be conscious of the risks your are taking by using the “contrib” or “non-free” components of the archived branch.
Now, that you are warned that the non-free people kill the pink rabbits, let’s move on:
To modify your software sources, it is enough to edit the ‘sources.list’ file. Open a terminal in terminal mode (chap.3.8.3), and enter:
apt edit-sourcesThis command opens the appropriated file with the default text editor (nano or vim). Once you are done with your modifications, save the file (“[Ctrl]+x” with nano, or “:wq” with vim http://www.vim.org/).
Example of line entry for the free packages:
deb http://deb.debian.org/debian/ stable mainExample of line entry for the free packages and the proprietary packages:
deb http://deb.debian.org/debian/ stable main contrib non-freeNow you can help yourself in the 3 package sections and install the non-free codecs and drivers.
Note also that you can modify your software sources by using the graphical Synaptic package manager (chap.8.3).

The following sections present the graphical interface of the APT (Advanced Package Tool) program. This application is also available directly from the command line, allowing a better fine tuning of your system.
This section presents the basic APT commands to manage the Debian packages from a terminal.
Debian supports also “aptitude”, another package manager, with a different syntax and behavior. This manual being intended for beginners, no need to explicit these commands here: to learn more about them, visit the dedicated Debian Aptitude Wiki: https://wiki.debian.org/Aptitude.
These commands can be executed as simple user, because they do not impact your system.
| command | description |
|---|---|
| apt show toto | display information about the package toto |
| apt search toto | look for packages corresponding to the toto |
| apt-cache policy toto | display the available version of toto |
These commands must be executed with the “root” administrator rights, because they impact the system. To move into the administrator mode from a terminal, type “su -”: the administrator password is requested.
| command | description |
|---|---|
| apt update | Update the repositories metadata |
| apt install toto | Install the toto package and its dependencies |
| apt upgrade | Secured update of the installed packages |
| apt dist-upgrade | Update of the installed packet, by adding/removing |
| other packages if necessary | |
| apt remove xyz | Remove the xyz package, but not the configuratrion files |
| apt-get autoremove | Auto remove the unecessary packages |
| apt purge xyz | Purge the xyz package and its configuration files |
| apt-get clean | Clean the local cache of the installed package |
| apt-get autoclean | Clean the local cache of the obsolete packages |
| apt-mark showmanual | Mark a package as being “manually-installed” |
For more detailed information and the apt/aptitude equivalence, visit the dedicated page of the Debian manual: https://www.debian.org/doc/manuals/debian-reference/ch02.html
All-in-One command line (in administrator mode) to update the repositories information + update your system + clean the packages in cache:
apt update && apt dist-upgrade && apt-get autocleanWhich goes to show that managing your system with a terminal is not that complex.
Apt vs Apt-get
The Apt program is currently going through some streamlining and offers now a simplified syntax for its commands and options. Thus, you will find both syntax (apt and/or apt-get) in this manual as well as in most of the GNU/Linux documentations.
Debian offers also some special repositories called backports, which contain more recent versions of some applications. These repositories are not activated by default, but do not present any particular risks for your system: the “regular” repositories have the highest priority during the update process, only the applications installed from the backports will look into these specific repositories.
![]()
… what do you mean exactly by “backports” ?
Nothing to do, in fact, with the “backdoors” used to spy on your machine running proprietary systems…
The backport is a mechanism allowing an application currently hold in the Debian development repositories, to be ported back to the “stable” version.
For example, the Debian developers take in the development repositories the most recent version of LibreOffice, and re-compile (re-build) the package holding the application, while taking care of all the dependencies existing in the “stable” version.
More details about Backports ine the dedicated page of the Debian wiki (https://wiki.debian.org/Backports). If you are looking for specific application, you have two solutions: use the search package tool (https://backports.debian.org/Packages/) [en] or the search by category (https://packages.debian.org/jessie-backports/).
![]()
Synaptic is the comprehensive graphical interface of the Debian package manager. It allows a total vision of the proposed packages, whether installed or not. It is a lot more detailed than the Software Center, or Apper (see the following chapters) since it displays the full set of available packages (including the libraries).
The Synaptic windows is divided in 4 areas: the tool bar at the top, the left pane allowing different ways of sorting and selecting the packages, the center pane displaying the package list itself, and below the pane hosting the description of the currently selected package (the selection is done with a click).
In front of each package, you notice a little box (white for non-installed packages, green when they are installed, red when they are broken). Next to this status box, a Debian logo indicates that this package is “free” (as in freedom).
The very first thing to do when you launch Synaptic, is to click on the “Reload” button in order to update all the information (metadata) concerning the repositories, the packages and the available applications.
Don’t hesitate to click on all the menus to explore Synaptic and become more familiar with it. It is a good way to discover its numerous functionalities.
Don’t be afraid to break your system since nothing will really happen until you click on the “Apply” button. On top of that, a message asking for confirmation will always be displayed first.
The repositories allow to update and install additional packages.
Open the Synaptic package manager (menu System > Synaptic package manager)
In the top menu bar, click on “Settings, then”Repositories“.
The GNOME desktop repository management uses an explicit “check” interface:
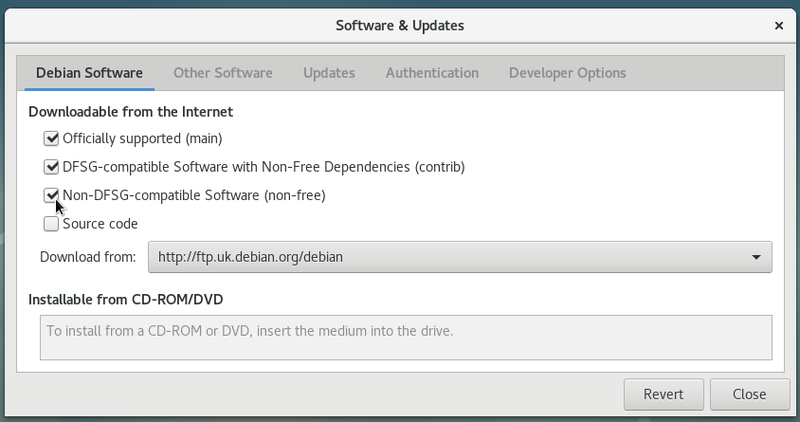
The management of the repositories on the other desktops like Xfce or LXDE is in “text” mode with the displayed addresses:
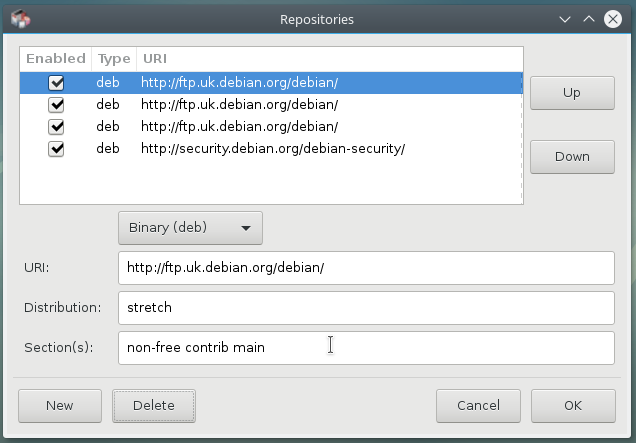
You’ll notice that the list corresponds to the contents of the /etc/apt/sources.list file mentioned in chapter 8.1.1.
Now, you can modify your repository sources at your entire convenience. Simply click on a source to modify it, or on the “New” button to add a new source.
Once your modifications are validated, the application will invite you to reload the repositories list in order to take your changes into account.
Note that if you want the “check” interface on Xfce Desktop, you have to install the “software-properties-gtk’ package.
Before updating the system, it is necessary to “Reload” the package list, by clicking on the corresponding button, or by going in the menu “Edit > Reload Packages Information” (or even [Ctrl]+r if you want to use a keyboard shortkey). This action checks if the version of the packages residing on your system is the most recent or not.

Then click on “Mark All Upgrades” or menu “Edit > Mark All Upgrades…”.
A new window appears with the list of the packages to be upgraded as well as the additional dependencies, if some are required:
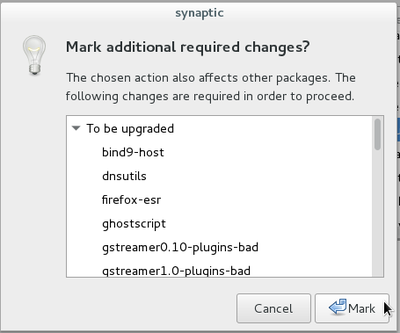
You only have to click on the “Apply” button, and accept the requested confirmation:
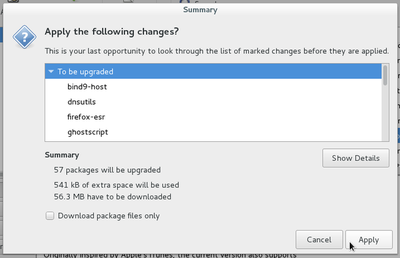
The system updating process begins with the package downloading, and continues with their installation. A message informs you that all the changes were applied.
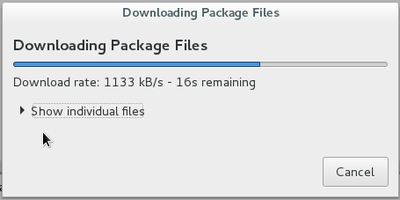
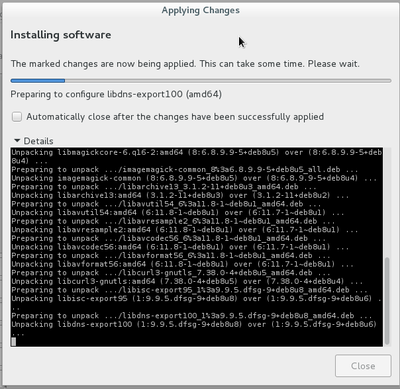
If you don’t know the name of the package you need, you can parse the list using the filtering by sections, status, origin, etc …
By example, if you are looking for a game, click on Sections in the bottom part of the left pane, scroll down to the “Games and Amusement” section, click on it, and the packages concerning games and amusement are listed in the center pane.
If you know the name of the package or if you are looking precisely for something, click on the search button (in the top bar) and enter the keywords of your search in the window which opens.
Other “Custom Filters” are available. Click on the button to explore them.
By clicking on a package, its description is displayed on the bottom center pane of Synaptic. To obtain even more information on a package, right-click on it, and select Properties, or go to menu “Packages > Properties”.
Then you will know everything - positively absolutely everything - on this package; dependencies, installed files, size and version.
To install one or several packages, right-click on the little box in front of the package name, and select the “Mark for Installation” option.
If, in order to be functional, this package requires the installation of other packages (the famous dependencies) they are automatically added to the selection.
Then, you simply need to click on the “Apply” button, and confirm the summary of the changes to be applied.
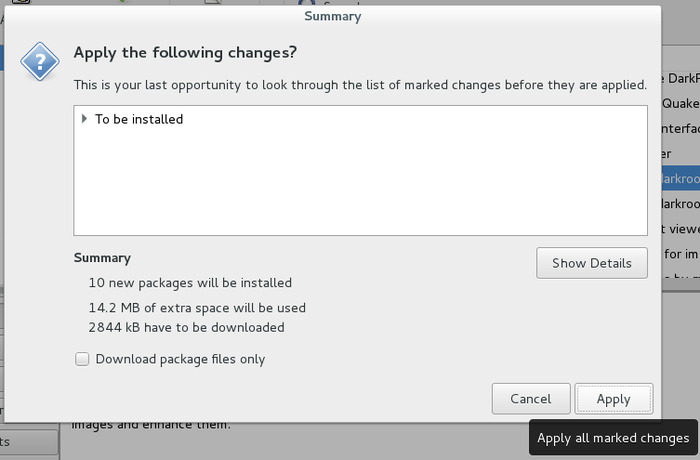
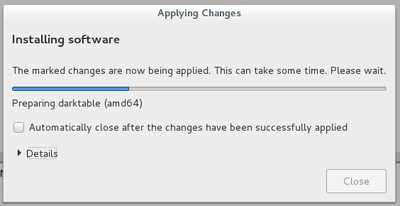
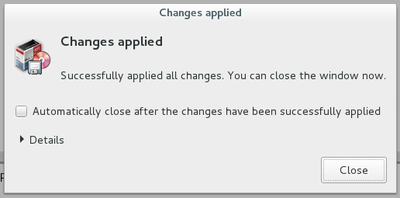
Like for the installation, right-click on the little box in front of the package name, and select the “Mark for Removal” option. Then click on “Apply”.
The simple removal keep the package configuration files on your system, in case you would like to re-install it, later on.
To remove also the configuration files select the “Mark for Complete Removal” option (equivalent to the “purge” in a terminal command line)
Sometimes we want to re-install a package which is already installed. In that case select the “Mark for Reinstallation” option. This allows, for example, to update the default configuration for the applicatoin if you modified it.
Often, when software is uninstalled, some packages (the dependencies) remain in the system while no longer useful, since all the packages needing them are gone. These useless packages can be easily removed with Synaptic.
When Synaptic is launched, click on the “Status” button at the bottom of the left pane. If the “Installed (Auto removable)” category shows up, click on it to display the corresponding package(s) (see image below):
All you have to do next is a right-click on each package in the center pane, and select the “Mark for Complete Removal” option. Once all the packages are marked, click on the “Apply” button.
Although one choose to completely remove a software, some configuration residues might still remain in the system, bur they can be removed with Synaptic.
Click on the “Status” button at the bottom of the left pane. If the category “Not installed (residual config)” shows up, select it (see image below):
All you have to do next is a right-click on each package in the center pane, and select the “Mark for Complete Removal” option. Once all the packages are marked, click on the “Apply” button.
“Preferences” is a well-named category, existing in most applications, and which is also present here…
But keep in mind that Synaptic is a very special case: it manages the full set of software installed on your system. When you remove a program, it does not go in the wastebasket (where you could have potentially retrieved it) !
After these scary warnings, let’s move to the settings available for Synaptic. the Preferences window (launched via menu Settings > Preferences) displays 6 different tabs:
Remember: by using a terminal (chap.8.2) you can achieve the same results more quickly and with less manipulations.
The Synaptic package manager is the default interface for the software management, but it is sometimes “too” complete. Gnome uses “Software” to manage applications in a simplified way, KDE integrates Discover, an intuitive and efficient software.
Discover simply launched from the KDE main menu > Applications> System > Software Center:
Search and install applications from the dedicated search field or by visiting the categories of Discover. A click on the “Install” button is enough:
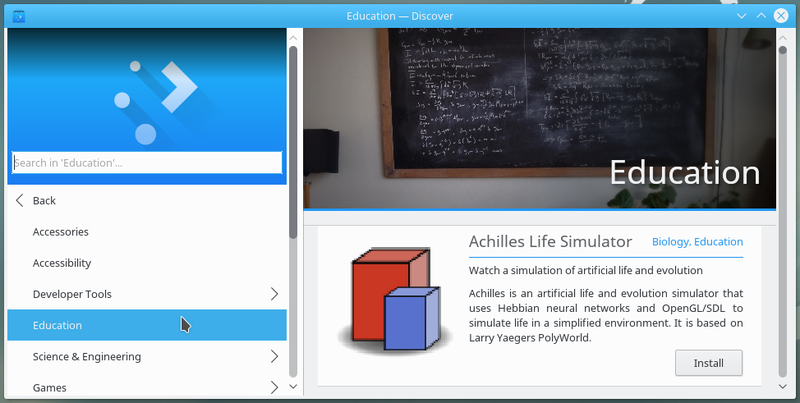
Install Plasma desktop wisgets directly from Discover by visiting the dedicated category (here with the “Weather” addon):
Uninstaliing an application with Discover, simply by visiting the “Installed” category then click on “Remove”:
A confirmation will be asked for any action on the software. The process will then be launched in the background. You can follow the progress of the changes from the KDE notification area.
When KDE notifies you of one or more updates, it is “Discover” that launches to perform them:
Simply click on “Update all” and confirm with the administrator password.
As with software management, you can follow the process from the KDE notification area.

Software is a simplified manager for Debian applications. It allows you to search, install, delete or update packages containing your applications. You can find it in the “System” category of your menus or directly from the Gnome search box by typing “Software”.
Directly from the search magnifying glass button, or by clicking on one of the displayed categories:
Install an application simply by clicking on its form and then “Install”. The administrator password will be requested. You can follow the progress in the main window and then launch directly the newly downloaded application.
Uninstall an application simply by visiting the “Installed” category (at the top of the interface) and clicking on the “Remove” button. You will be asked for confirmation:
Update your system from the dedicated section “Updates” which will indicate the available and/or already downloaded updates. If no update is available, you can check the repositories using the dedicated button at the top left.
In our example, an update series that includes the “operating system update” requires a reboot. You can list all the updated applications in this batch by clicking on the relevant entry:
You then have to restart by clicking on the dedicated button.
Note that for smaller updates, restart is not necessary.

Even if the capacity of hard disks increased dramatically during the last years, you might need some free space. Several scripts automate the disk cleaning process, however I must confess that I prefer to check before using the rm command (standing for remove. chap.11.2).
The first thing to do, of course, is to find out the used space on your disk. Several tools are available to you:
Disk space in terminal mode: a summary of the disk space usage for each system mount points (disks and partitions):
df -hList your folders sorted by decreasing size:
du -ks * | sort -nrNcdu: disk space analyzer in console mode. To launch it, simply type “ncdu” in your terminal. To install this software (in administrator mode):
apt update && apt install ncdu
Baobab: disk space analyser in graphic mode, integrated in Gnome.
Fslint: utility to find and clean various forms of unwanted extraneous files in your file system, like duplicates, broken links, empty folders, wrong encoding, etc … To be manipulated with extreme caution: double check carefully the pending changes before validating the whole process.
Apt/aptitude/dpkg are the usual Debian package managers. When you install a package its archive-source/deb file is stored in your system (in the /var/cache/apt/archives/ folder) to enable a potential re-installation without Internet connection. To clean the “apt cache” use a simple command in administrator mode (chap.3.8.3):
apt-get cleanOnce the cache of the installed packages is cleaned, you can also remove the useless packages from your system, as well as the configuration files. Warning! Remember to check carefully the list of the packages planed for removal, before accepting the operation:
apt-get autoremove --purgeThree different bins must be taken into account:
The user wastebasket : ~/.local/share/Trash/ . You can empty it with the system file manager, or with a terminal:
rm -Rf ~/.local/share/Trash/*The administrator wastebasket : /root/.local/share/Trash/ . To empty it with the proper manner, use a terminal in administrator mode:
rm -Rf /root/.local/share/Trash/*The external wastebaskets : locates on your external disks, they are usually named ‘/media/your_id/your_disk/.Trash_1000’, where your_id corresponds to your login name.
Some applications use a “cache” folder, where they store images, videos, and miscellaneous information in order to run faster. Usually these data do not occupy too much disk space, however if (using the tools described above) you detect that a folder becomes too fat, don’t hesitate to remove it.
Each application has its own way to manage its own cache: some purge it systematically when they close, others store their data in the /tmp folder, which will be cleared during the session logout, others keep all their information in a specific folder.
For Firefox, as an example, you can purge the cache from the preferences menu, and even automate this action every time the application is closed.
Every time you open a folder containing pictures or videos, thumbnails are created to represent these graphic files. These thumbnails are stored in a specific folder to reuse them, rather than being forced to recompute them, every time you access this kind of file.
The problem raised when you delete a graphic file, because its thumbnail is kept in the system, and this leads to a certain amount of disk space used to store obsolete thumbnails.
To purge them, it is enough to remove their corresponding folder:
rm -Rf ~/.thumbnailsThis folder will be created again, the next time the system needs to store a newly generated thumbnail.
Debian GNU/Linux uses the package repository system to better manage the software and increase the security of your system. But it may happen that you need an external package of the “.deb” format.
![]()
… but who is this “deb” ??
deb is the short for “debian”, the mother company. To distribute its software, Debian uses a specific archive file format: “.deb”. It is a compressed format, like the “.zip” that you use to save your data. These “.deb” archives are recognized by the different Debian package managers (APT and its graphical interface Synaptic) and thus can be handled more easily.
Gdebi is a graphical utility with allows the installation of external packages of the “.deb” format, while managing the dependencies.
To install it, look for “gdebi” in your favorite package manager (Synaptic, Apper, Packages) or more simply from a terminal in administrator mode using “su” (chap.3.8.3):
apt update && apt install gdebiWhen you download a Debian external package, right-click on it and select “Open with gdebi”.
Dpkg is a software utility handling the packages like apt, but it does not manage the dependencies. This means that if you use dpkg to install external packages, you need to install the “dependent” packages one by one from your terminal. Dpkg is integrated in Debian by default, and must be used in administrative mode.
To install an external package:
dpkg -i package.debAn error message will let you know if some dependencies are missing, an error message will let you know, and then simply install them the classic way with apt:
apt install dependent_1 dependent_2 ...Then relaunch the installation of your external package:
dpkg -i adresse_du_paquet.debTo remove an external package:
dpkg --purge package_nameFirst of all, one must know that several Debian distribution branches exist in parallel.
Namely the oldstable, stable, testing and unstable distributions, as well as an experimental branch.
The Stable distribution is the Debian official distribution, the one released at this moment, with is maintained and updated par the Debian teams. The only changes made concern the security updates and the bug fixes. It is recommended to favor this Version.
The Oldstable distribution is the previous stable version. It is usually supported by the Debian teams during one year after the release of the new stable version. Then it might live longer if enough individuals or companies continue to assure its maintenance. Then it is called a LTS (standing for Long Term Support) distribution: we extend its life span.
The Testing distribution is the future Stable version. It is used to prepared the next stable version. When everything is OK, when all the bit and pieces are functioning well together, when all the features targeted by the Debian teams are included, and after a period of software freeze and bug hunting, then the Testing version becomes the official new Stable distribution.
The Unstable distribution, nicknamed Sid is the version which receives all the new packages versions, and sits at the cutting edge of innovation, but is not very stable: it’s a research lab. Nevertheless some brave adventurers use it on a daily basis.
The Experimental distribution is not a Debian distribution per se, but rather a repository where alpha or beta software versions are tested.

All these distributions are given a name picked among the characters of the Toy Story® cartoon. Currently, the name of the stable version is Stretch, the name of the testing version is Buster, the name of the oldstable version is Jessie, the Experimental as no nickname.
The name of unstable is Sid, but who is this Sid guy?
Sid is the little boy, in the Toy story® cartoon, who breaks all his toys (http://pixar.wikia.com/wiki/Sid_Phillips).

More detailed information on the dedicated Debian Wiki https://wiki.debian.org/DebianUnstable.
 Back up your data
Back up your dataNo matter where your expertize level is, or the current state of your hardware, nobody is immune to a bad cockpit error, a technical failure, a heavy thunderstorm, a cup of tea/coffee spilt on the keyboard, or the cat messing around with the central unit …
The hard dish drive capacities are increasing every day and we are tempted to store on them more and more data (family pictures, videos, private copies of movies, etc). The risk of losing a large amount of data also increase at the same time, and that’s why we advise you to execute regular backups of your personal data, as well as your passwords and email messages.
This section will endeavor to provide you with simple keys to avoid the lost of your favorite files during a hardware or software failure.
![]()
The “cloud” is fashionable these days. Several on-line services are at your disposal to save your data on an external server…
First of all, you are not immune to a server failure, and secondly, you have no real control on what your data are going to be used for. The “cloud” is actually the computer of someone else, as user Bibi told us recently.
I strongly advise you, in case of doubts (all services are not subsidiaries of the NSA …) to backup your data locally, that is on your own physical medium which you fully control.

Backups used to be made on floppy disks, then on CDs and then on DVDs. Even if you can still use this kind of support, the technology now gives you access to larger capacities at little cost.
Depending on the amount of the data to backup, you can find external disk from 1GB (USB key type) to 2TB (2000GB), being powered directly over the USB cable, or by an external power supply. The prices range roughly from 5 to 200 US$, depending the capacity.
Of course, if the size of your data is below 700MB, you can use a CD-RW (re-writable CD-Rom) for your backups.

Debian hosts in its repositories several utilities (https://www.debian.org/doc/manuals/debian-reference/ch10.html#_copy_and_synchronization_tools) in the “copy and synchronization” section, each of them offers a graphical interface or “client”. Here we present one of the simplest backup tool: Deja-Dup.
Deja Dup is more than enough to backup your personal data, but if you want to execute a “full system backup” (including your application and the whole installation) you must use more complex software, as described in the Debian documentation (https://wiki.debian.org/BackupAndRecovery).

Deja Dup (https://wiki.gnome.org/Apps/DejaDup) is a “simplified backup tool”, which is a graphical interface to the Duplicity software (http://duplicity.nongnu.org/). It allows building secured backups of your data within a local folder, an external disk, a local network, a remote network or somewhere in the “cloud”.
It also allows the complete encryption and password protection of your backup files.
Deja-Dup offers a clear interface which does not require any computer knowledge.
Deja-Dup can be found in the Debian repositories.To install it using a terminal in administrator mode (chap.3.8.3) :
apt-get update && apt-get install deja-dupOr using the graphical interfaces (chap.8.3), look for “deja-dup”.
Deja-Dup will be accessible from the application menu > “Utilities” > “Backups”. During the first launch, the Deja-Dup settings let you define how to automatically execute the future backups, where to save, what to save and with which frequency.
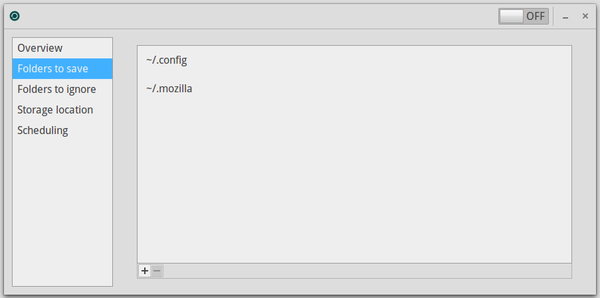
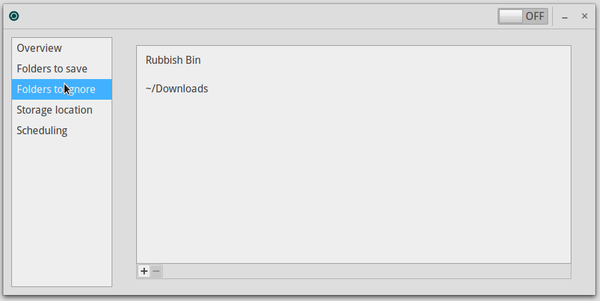
Once the settings are done, launch the first backup by clicking on the “Back Up Now” button residing under the “Overview” tab.
The very first backup execution will take some time, depending on the size of the data to be saved, but the following runs should be a lot faster since they will save only the modified files: this is the incremental backup.
An additional feature is the optional password setting during the configuration, which allows the encryption of the full set of backups:
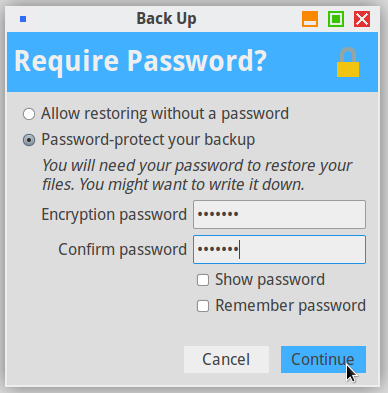
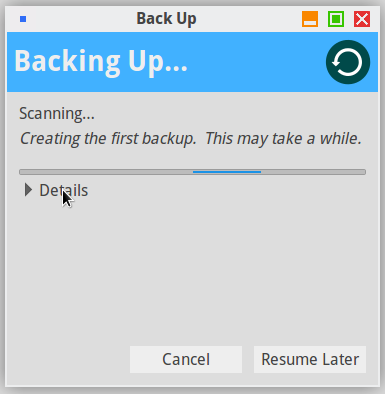
To restore a backup on a newly installed system, for example, simply install Deja-Dup on it, launch it and select “Restore” in the main window.
A series of simple windows will help you to find and restore your data:
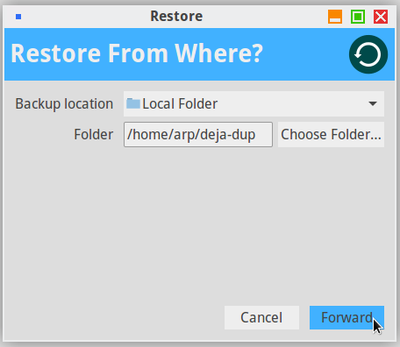
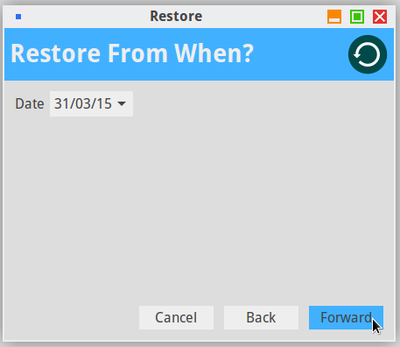
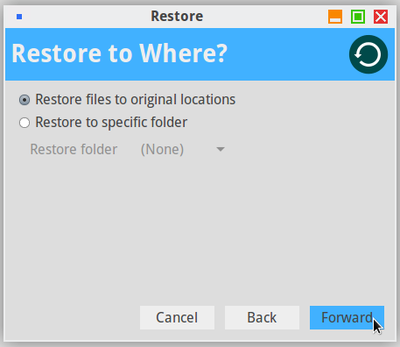
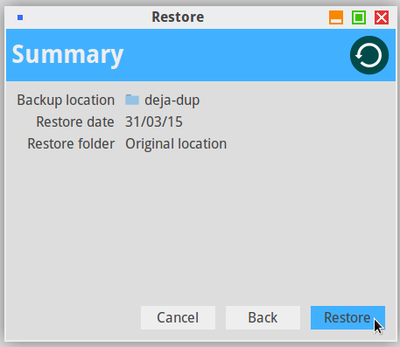

If you want to save just one folder or few of them, you can simply use the file system manager, or your archive manager (to reduce the storage space through compression).
The latter produces “real” archives: for subsequent consultation of these data, you need to uncompress the archive.
From the file manager, select the folders to be saved, then right-click and take the “Compress…” (or “Archive”) action.
Then you just have to move the archive on an external medium.

This is the complete solution ensuring a total safety for your data: cloning the entire hard disk.
Clonezilla Live (http://clonezilla.org/) is a Live CD based on the Debian GNU/Linux distribution, which includes the Clonezilla software. It allows the user to directly execute from its machine:
This Clonezilla version is able to connect to different servers: SSH server, Samba server, NFS server …
As its name suggests it, it works like a Live CD (CD-ROM, DVD-ROM) but can also be executed from a USB key, an external disk, etc. (source Wikipédia).
You can find an English tutorial on this page: https://www.howtoforge.com/back-up-restore-hard-drives-and-partitions-with-clonezilla-live.
 Protect your data and your privacy
Protect your data and your privacyThe news are crystal clear: is being wire-tapped. It is not to alarm or frighten you, but you have to realize that the “Internet” is not your private living room, and that each picture or text used on the web is potentially recoverable.
This is obvious, but let’s say it but once and for all: if you want to protect your data, don’t leave your laptop everywhere ! don’t leave your computer in self-service at your home !
Your computer hosts your passwords (bank, administration, work …) your documents (administrative forms, pictures, etc.), your browsing history (the sites you visited and when), etc. You may think that these information are seemingly harmless, but they allow - for the best - to define your consumer profile, or - for the worst - to use your computer as a gateway to crack in other persons systems.
If you want to present your distribution, or simply share tour resources, we strongly suggest you create another user account (chap.7.3) who will not be able to access your data, nor to mess with your system administration.
![]()
If your computer is always on the road, we suggest you use the direct encryption during the system installation like mentioned in the chapter 5.5.3. By this way, even if your computer is lost or stolen, it will be extremely difficult to extract the data from your hard disk.
The software updates bring new functionalities, fix bugs, and, above all, correct potential security flaws.
This is the big strength of the Libre-Software: the program sources are available, thus when a flaw is uncovered, it is publicized and fixed immediately.
This practice to be opposed to the proprietary systems, whose flaws are being kept secret, and continue to affect the daily life of all their users.
The security updates should not be considered as optional ones: you must install them as soon as possible.
Each year, tens of thousands of email accounts, Wi-fi access codes, phone PIN … are easily cracked, because users picked passwords too easy to guess. The top worst password for the year 2013 was “123456”, but there are other crazy sequences like “QWERTYUIOP”, “0000”, animal names, birthdays …
 All these passwords, too easy to guess, must be avoided !
All these passwords, too easy to guess, must be avoided ! 
And, by the way, putting together two weak passwords, does not create a strong one ! “Independance1783” might be difficult to guess for a human being, but a “computer robot” will decipher it in the blink of an eye.
To increase the robustness of your password, in other words to increase its resistance against deciphering attacks, use as many characters as possible and mix their types (lowercase and uppercase letters, numbers, special characters).
There are simple tolls which allow you to keep and organize your passwords like KeePassX (https://www.keepassx.org/).
![]()
The stronger my password is, the more difficult to memorize it. Isn’t it ?
You can use a **“pass-phrase**. Here we are talking about a long sentence, difficult to uncover, but easy to remember: few words put together produce a meaningless string, but which has a well defined sense for youself.
For example, the sentance “grandma loves French pickles in her soup”, can easily becomes a robust password: “GrandmaLovesFrenchPicklesInHerSoup” … especially if one replaces few vowels by numbers (“i” by “1”, “e” by “3” and o by “0”):
“GrandmaL0v3sFr3nchP1ckl3sInH3rS0up”.
If you use Debian in “multi-user” mode, the data of the other users are readable by you, and yours too, by necessity. You may want to restrict the access rights to some of your data for the other users. The graphical procedure is easy (no need to open a terminal): right-click on he folder > properties > “Permissions”. hereafter an example with the “Documents” folder.
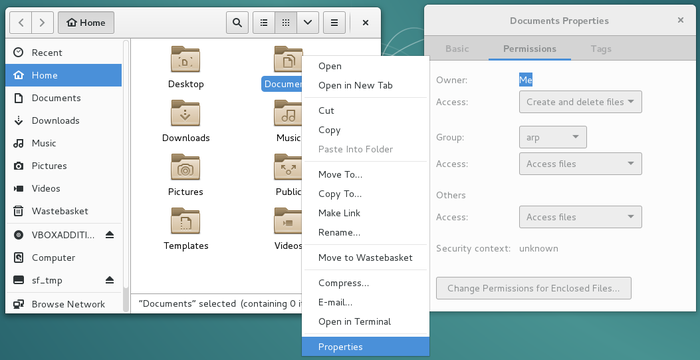
Select the “None” option for the “Others” access rights:
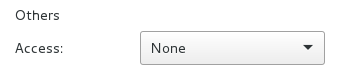
A window will ask you if you want to apply these modifications to all the files and folders embedded within the concerned folder, and we advise you to accept, in order to protect the full set of data included inside this folder.
You certainly ran into these warning messages talking about backing up your data …
and this is not for nothing! Please refer to the chapter 9 and get into the habit of saving your data on an external medium and on a regular basis.
Admittedly, the GNU/Linus systems are much less sensitive to virus attacks, but it is possible to find a virus on a GNU/Linux machine.
![]()
For the time being, updates are the only efficient protections against potential viruses, and adding an antivirus software on your system does not improve its security. Viruses embedded within documents originating from proprietary systems do not target the GNU/Linux environments, and as such, are totally harmless for your data.
However, if you want to monitor and control your data, ClamAv is the reference antivirus software. Note that it does not run continuously in the background, and the user should explicitely request a folder scan to verify its contents.
More information on the DebianHelp site http://www.debianhelp.co.uk/clamav.htm
Yes, one can find everything on Internet: the best and the worst, and often inappropriate images and contents for our children. In order to let them enjoy safely the digital world, you can use different parental control systems.
However, keep in mind that YOU are the best parental control ! 
The Internet Service Providers usually propose different parental control software. This method allows you to control all the devices on your home network, but does not exempt you to activate the parental control on your Web Browser.
More information on the site https://www.internetmatters.org/parental-controls/interactive-guide/
The settings of the parental control is reserved to the experienced users, because the procedure is rather complex … and is not 100% effective. In addition, the list of “prohibited” sites must be updated on a regular basis. The Fox Web Security addon module can be effectively installed in the Firefox navigator extensions (https://addons.mozilla.org/en-US/firefox/addon/fox-web-security) in order to filter inappropriate “adult content”.
An alternative solution is to use a search engine whis is going to filter the proposed results, like Qwant Junior: https://www.qwantjunior.com
It is difficult to remain completely anonymous on Internet. Unless you are a well equipped experienced user, you will always leave a trail behind you.
The most beautiful fingerprint you leave, on a daily basis, is your IP address. In fact, each device connected to Internet must have an IP address, which allows to know not only your ISP, but also your precise geographical location … A small test? visit this page to know your public IP address: http://whatismyipaddress.com/
In addition, even if you are not a great pastry chef, you are giving away a lot of “cookies” to all the sites you are visiting. Cookies are connection witnesses: they keep, for a given site, information like your preferences, your identifier, your password, your chosen language, the content of your digital shopping cart, etc. not only on your computer but also on the servers in the cloud. Thus, when you start a search request on a site, it is very capable to register this information.
Advertising companies come join the party, and automatically create your profile by looking at your browsing history.
Don’t be alarmed, Numerous advices and software tools are at your disposal to become easily discreet.
Remember that the social networks, in their vast majority, are not there to help you, quite the contrary: they are big advertising agencies which collect everything they find about you. Then, these personal information are resold to advertisers, in order for them to better target your “needs”.
Intelligence on the social networks does not stop there: they continue to trace you on plenty of sites by using - for example - the “like” or “G+” buttons.
Furthermore, the latest scandals unveil the fact that personal data can be collected by several governmental intelligence agencies, even if you are not doing anything suspicious.
![]()
If you cannot resist to the temptation of opening an account on a social network (and I fully understand you: virtual encounters are very cool), you can test the Diaspora or the Mastodon journey and discover a decentralized network, which is respectful of your private life and data; Diaspora and Mastodon are designed on the “node network principle”, which means that several connecting points are available. here is one to start with: https://www.joindiaspora.com/ and https://mastodon.social/about.
As far as the other “less social” networks are concerned, find hereafter few simple advices:
If you want to surf the Web without leaving traces on your computer, the latest versions of the Internet navigators include a “private browsing” feature. This mode functions very simply: once launched, the navigator does not keep the history of the visited sites, nor the cookies distributed by these sites, nor the passwords entered during this “private” session.
However, the visited sites keep track of your IP address: you don’t navigate in an “anonymous” way.
For Firefox, click on the menu (the 3 band top left button) then select the “New Private Window” option.
Note: it is very possible that some Internet sites do not function well if some cookies are disable. Thus, it is best not to use this mode all the time.
Warning: private does not mean anonymous!
First avoid using non-free navigators, whose source codes cannot be analyzed by the first expert that comes along. The non-free navigators (Internet Explorer, Safari, Chrome …) can potentially spy on your navigation without your knowledge.
The main free navigator you can trust is Firefox.
The private navigation allows the removal of all navigation traces on your computer and can add few more protections against the tracking. It cannot guarantee your anonymity when facing some advanced tracking technology like the fingerprinting (https://wikipedia.org/wiki/Canvas_fingerprinting).
Stop doing like everyone else, even if supposedly “you have nothing to hide”.
If you want to become anonymous and mask completely your IP address, the best idea is to use TOR (https://www.torproject.org/index.html). To achieve this, we are going to desciobe two methods: installation of the Tor-Browser or the usage of the Tails anonymous distribution.
![]()
… What’s this Tor stuff ??
TOR stands for The Onion Router, and is a software allowing us to become anonymous on the net by communicating with other TOR users. The principle is to define a random and indirect route on the network, between you and the exit node, which makes impossible the tracking of your IP address.
In addition, the data circulating on the TOR network are encrypted, which makes even more difficult to identify the flows, although they are spied on.
This functionality must not prevent the common sense … If you connect to an account, whatever it might be, with your usual pseudo and password, you will be quickly identified, even if you use TOR.
Tor offers its web browser under the form of an independent archive (no need for administrator rights):
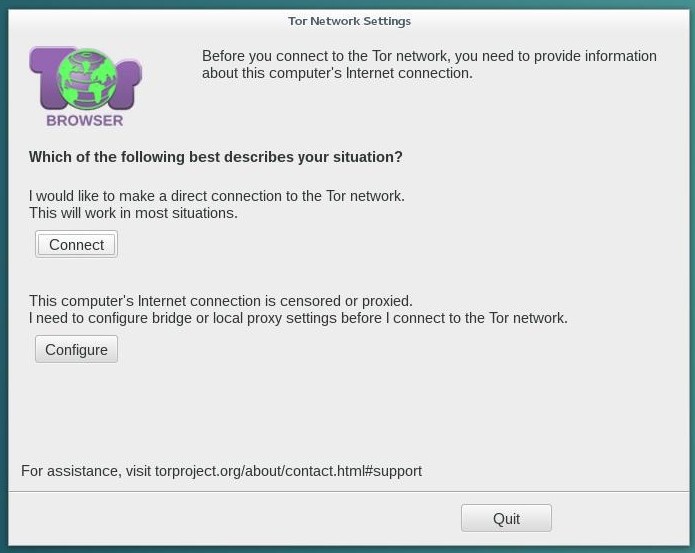
Please note that using Tor might slow down your Internet navigation.
Tails is a GNU/Linux distribution based on Debian. It allows you to be totally anonymous on the net. It is installed on a DVD or a USB key, and like with the other Debian Live (autonomous) images, nothing is saved on your DVD or USB key between two working sessions, and, in addition, you enjoy an anonymous navigation on Internet.
On the main site, you can read …
Tails is a live (autonomous) operating system that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to:
For more information, you can visit the Tails download page https://tails.boum.org/install/download/index.en.html.
![]()
Note that the TOR navigation is often slowed down, and that some site or functionalities will not be reachable, due to their embedded scripts or their “privacy” policies …
Is it the right time to sort out through all your bookmarks ?

No! You must be aware that internet browsing works thanks to a physical network of connected machines. A person with physical access to the different “connection points” will be able to observe the traffic and capture informations immediately, or to store this information for a further consultation.
In addition, computer monitoring is not the only way to identify you and your navigation: video surveillance of public or private places, labeling of machines “for your safety” are only examples of all the possibilities of the authorities and companies to access your valuable data.
It is up to everyone to define his “private life” and not spread it on the web … Or to move on to more political than technical considerations for the Privacy Protection  .
.

 Basic Command Memo
Basic Command Memo
Debian GNU/Linux systems have all the graphical applications needed to perform your daily tasks, so why use the command line?
This section gathers some basic commands. For a more complete list, visit the Debian documentation: https://wiki.debian.org/ShellCommands.
The ultimate command: man
command action
----------------------------------------------------------------------
pwd Print Working Directory
cd rep Change Directory to rep
cd Change Directory to /home/$USER or ~/
cd .. Browse the parent directory
ls rep List information about file(s) in rep
ls -a ls with hidden files displayed
ls -l ls with size and rightscommand action
----------------------------------------------------------------------
mv source target move the file from source to target
cp source target copy the file from source to target
cp -R source target copy the directory source to target
ln source link create a hard link from source to link
ln -s source link create a symbolik link from source to link
touch file create the file file or update its
modification date
mkdir rep create a repertory rep
mkdir -p rep/rep2 mkdir with creation of parent directory if needed
rm file remove file
rm -f file remove the write-protected file
rmdir rep remove an empty directory
rm -R rep remove a directory
du -h file or rep display size of the file or the repcommand action
----------------------------------------------------------------------
wc file Print byte, word and line counts of file
cat file display the contents of a file
more file displays file page by page. 'Space'=next page,
'Enter'=next line, 'u'=up
less file displays file with fine navigation
Left/Right/Up/Down/PageUp/PageDown
head -n x file displays 'x' first lines of file
tail -n x file displays 'x' last lines of file
tail -f file dynamicaly display last line of file
diff file1 file2 Displays differences between two text files
diff -u file1 file2 Displays differences between file1 and file2
with patch syntax
comp file1 file2 compares two binary files
comp file1 file2 n N compare two files, file1 from the octet n and
file2 from octet Ncommand action
----------------------------------------------------------------------
whoami Print the current user id and name
who Print all usernames currently logged in
id Print user and group id's (uid & gid)
id user Print user and group id's (root only)
finger user Print informations about user
write user Print a message on user's terminal
tty Print the current terminal's name
su - sudo Switch to administrator mode, superuser
passwd Change the password of the current user
adduser add a user
deluser delete a user
addgroup add a group
delgroup delete a groupcommand action
----------------------------------------------------------------------
ps Process Status. Lists running process
ps ax Print all running processes
ps aux Print all process identified by users
pstree Print all process in a tree
top List processes running on the system in a
semi-graphical table
kill signal pid kill a process using its pid
pkill signal name kill a process using its namesignaux utilisés par kill/pkill
signal mode action
----------------------------------------------------------------------
-1 (HUP) Reload the process configuration file
-2 (INT) Interrupt the process
-3 (QUIT) Quit the process
-9 (KILL) Kill the process (to avoid, try '-15' first)
-15 (TERM) Complete the process properly
-18 (STOP) Freeze the process
-20 (CONT) Resume execution of a frozen processcommand action
----------------------------------------------------------------------
lsusb Lists connected USB devices
lspci Lists connected PCI devices
cat /proc/cpuinfo Displays processor information
cat /proc/partitions Displays mounted partitionsexamples : (sources linuxtrack)
Display the model of the graphics card:
lspci | egrep "3D|Display|VGA"Show the model of the Wifi card:
lspci | grep -i "net" | cut -d: -f3Show the soundcard model:
lspci | grep -i audio | cut -d: -f3command action
----------------------------------------------------------------------
hostname Print or set system name
ping machine send a ping to a machine on the network
traceroute machine displays a traceroute through machine
netstat Displays the use of the network
by the processes
netstat -a netstat with the display of the
server processes
lsof Detailed list of file and network usage
ifconfig Displays the config of the interfaces
ifconfig interface IP mask configure the network interface
route Displays the routing tableex : displays its locap IP on eth0
ip address show eth0 | grep "inet " | tr -s " " ":" | cut -d: -f3
/sbin/ifconfig eth0 | grep "inet " | tr -s " " ":" | cut -d: -f4
ip address show eth0 | grep "inet " | tr -s " " ":" | tr -s "/" ":" | cut -d: -f3command/option action
----------------------------------------------------------------------
locate pattern search for file with a pattern name
updatedb update locate database
find path options search for file corresponding to options in path
find -name pattern search for file with a pattern
find -type f/d/l search by filetype: f=file, d=directory, l=link
find -exec cmd execute *cmd* to found filesExample: search for all png files in the ‘Images’ directory, then copy all files to tmp directory ( ‘{}’ stands for found files).
find $HOME/Images -name "*.png" -exec cp {} $HOME/tmp/ \;format compress extract
----------------------------------------------------------------------
.tar.bz2, .tbz2 tar -cvjf archive.tar.bz2 directory tar xvjf
.tar.gz, .tgz tar -cvzf archive.tar.gz directory tar xvzf
.bz2 bzip2 file bunzip2
.rar - unrar x
.gz gzip file gunzip
.tar tar -cvf archive.tar files tar xvf
.zip zip -r archive.zip files unzip
.Z compress files uncompress
.7z 7z a files 7z x
.xz xz -z directory unxzVersion of the Linux kernel used, its name, the version of the compiler used:
cat /proc/versionVersion of the Linux kernel used:
uname -rList all kernels installed on your machine:
dpkg -l | egrep "linux-(header|image)" Free Softwares
Free SoftwaresYou can find hereafter a list of the sites providing more detailed information concerning the Free Culture (in general) and the Free Software (in particular).
https://www.fsf.org/
The Free Software Foundation (FSF) is a nonprofit with a worldwide mission to promote computer user freedom. We defend the rights of all software users.
Free software developers guarantee everyone equal rights to their programs; any user can study the source code, modify it, and share the program. By contrast, most software carries fine print that denies users these basic rights, leaving them susceptible to the whims of its owners and vulnerable to surveillance.
https://www.gnu.org/
Philosophy of the GNU Project: Free software means that the software’s users have freedom. (The issue is not about price.) We developed the GNU operating system so that users can have freedom in their computing.
Specifically, free software means users have the four essential freedoms: (0) to run the program, (1) to study and change the program in source code form, (2) to redistribute exact copies, and (3) to distribute modified versions.
Software differs from material objects—such as chairs, sandwiches, and gasoline—in that it can be copied and changed much more easily. These facilities are why software is useful; we believe a program’s users should be free to take advantage of them, not solely its developer.
https://www.linuxfoundation.org/
The Linux Foundation partners with the world’s leading developers and companies to solve the hardest technology problems and accelerate open technology development and commercial adoption.
Founded in 2000, The Linux Foundation today provides tools, training, and events to scale any open source project, which together deliver an economic impact not achievable by any one company.

You all know Wikipedia the free on-line encyclopedia.
But actually Wikipedia is part of a large family, under the benevolent umbrella of the Wikimedia Foundation
The Wikimedia Foundation is a global movement whose mission is to bring free educational content to the world. Quoting the foundation home page :
“Imagine a world in which every single human being can freely share in the sum of all knowledge. That’s our commitment.”. https://wikimediafoundation.org/wiki/Home

wikipedia, the free encyclopedia https://wikipedia.org/
Wikipedia is an universal, multilingual encyclopedia, written and maintained by volunteers on the Internet, and functioning under the Wiki principle.

wikimedia commons, the multimedia library https://commons.wikimedia.org/wiki/Main_Page
Wikimedia Commons, which is often refereed to as Commons, is a media file repository making available public domain and freely-licensed educational media content (images, sound and video clips) to everyone, in their own language.

wikitionnary, the dictionary https://en.wiktionary.org/
Wikitionary was initially designed as the lexical companion to Wikipedia, the encyclopedia project, Wiktionary has grown beyond a standard dictionary and now includes a thesaurus, a rhyme guide, phrase books, language statistics and extensive appendices. We aim to include not only the definition of a word, but also enough information to really understand it. Thus etymologies, pronunciations, sample quotations, synonyms, antonyms and translations are included.

wikiquote, the free quote compendium https://en.wikiquote.org/wiki/Main_Page
The Wikiquote collaborative project, is a free online compendium of sourced quotations from notable people and creative works in every language, translations of non-English quotes, and links to Wikipedia for further information.

wikisource, the free library https://en.wikisource.org/wiki/Main_Page
Wikisource is a project to create a growing free content library of source texts, as well as translations of source texts in any language. This work is done by voluntary contributors.
Some things Wikisource includes are: Source texts previously published by any author, Translations of original texts, Historical documents of national or international interest, Bibliographies of authors whose works are in Wikisource.
Some basic criteria for texts excluded from Wikisource are: Copyright infringements, Original writings by a contributor to the project, Mathematical data, formulae, and tables, Source code (for computers), Statistical source data (such as election results).
Unless otherwise noted, all user contributions to Wikisource are released under the Creative Commons Attribution/Share-Alike License (CC-BY-SA) (replacing the previously used GNU Free Documentation License).

Wikibooks, the open-content textbooks collection https://fr.wikibooks.org/wiki/Accueil
Wikibooks is a collection of open-content textbooks. Wikibooks is for textbooks, annotated texts, instructional guides, and manuals. These materials can be used in a traditional classroom, an accredited or respected institution, a home-school environment, as part of a Wikiversity course, or for self-learning.

wikijuniors, the free textbooks for children https://en.wikibooks.org/wiki/Wikijunior|Wikijunior
Wikijunior produces non-fiction books for children from birth to age twelve. These books could take the form of macropedias, textbooks, or primers. These Wikijunior books are written with children in mind. The subjects of these books are chosen because they are appealing to kids. These books are richly illustrated with photographs, diagrams, sketches, and original drawings.

vikidia, the free encyclopedia for children https://en.vikidia.org/wiki/Main_Page
Vikidia is an English encyclopedic project, based on wiki technology, for 8-13 year-old readers and contributors, but not only.
The website is independent from Wikimedia Foundation which owns Wikipedia. It was launched in November 2006 in French and in 2013 in English. Vikidia is handled by the Association Vikidia, a non-profit-organization located in France.

Wikiversity, the open learning community https://www.wikiversity.org/
Wikiversity is a Wikimedia Foundation project devoted to learning resources, learning projects, and research for use in all levels, types, and styles of education from pre-school to university, including professional training and informal learning.
Teachers, students, and researchers are invited to join Wikiversity in creating open educational resources and collaborative learning communities.

wikispecies, the free species directory https://species.wikimedia.org/wiki/Main_Page
Wikispecies is a wiki-based on-line project supported by the Wikimedia Foundation. Its aim is to create a comprehensive free content catalog of all species; the project is directed at scientists, rather than at the general public. Wikispecies is available under the GNU Free Documentation License and CC BY-SA 3.0.

wikivoyage, the free travel guide https://www.wikivoyage.org/
Wikivoyage is a free web-based travel guide for travel destinations and travel topics written by volunteer authors (“Wiki-travelers” from all around the world). It is a sister project of Wikipedia and supported and hosted by the same non-profit Wikimedia Foundation. Wikivoyage has been called the “Wikipedia of travel guides”.

wikinews, the free news source https://en.wikinews.org/wiki/Main_Page
Wikinews is a free-content news source Wiki and a project of the Wikimedia Foundation. The site works through collaborative journalism. Wikipedia co-founder Jimmy Wales has distinguished Wikinews from Wikipedia by saying “on Wikinews, each story is to be written as a news story as opposed to an encyclopedia article.” The neutral point of view policy espoused in Wikinews distinguishes it from other citizen journalism efforts. In contrast to most projects of the Wikimedia Foundation, Wikinews allows original work under the form of original reporting and interviews.

wikidata, the free and open knowledge base https://www.wikidata.org/wiki/Wikidata:Main_Page
Wikidata is a collaboratively edited knowledge base operated by the Wikimedia Foundation. It is intended to provide a common source of data which can be used by Wikimedia projects such as Wikipedia, and by anyone else, under a public domain license. This is similar to the way Wikimedia Commons provides storage for media files and access to those files for all Wikimedia projects, and which are also freely available for reuse. Wikidata is powered by the software Wikibase.
This project was launched by Wikimedia Deutschland. It was presented during the Semantic Tech & Business Conference in February 2012, and the site was open to the first contributions on 30 October 2012.

wikimedia Meta-wiki, the global community site for the Wikimedia projects https://meta.wikimedia.org/wiki/Main_Page
Meta (or Wikimedia’s Meta-Wiki) is a wiki-based web site that is auxiliary for coordination of all the Wikimedia Foundation projects.
Meta currently serves as one of the major avenues of discussion for Wikimedians including Wikipedians, the others being the mailing lists, the IRC channels, and the talk pages of individual articles and users. Meta is an independent and autonomous project from the English language Wikipedia and thus has its own policies and customs, which often differ from those here.
Originally focused on the English language version of Wikipedia, Meta has, since its upgrade to Wikipedia’s custom MediaWiki software, become a multilingual discussion forum used by all Wikimedia language communities.

wikimedia incubator, where possible new languages for existing projects are tested https://incubator.wikimedia.org/wiki/Incubator:Main_Page
The Wikimedia Incubator founded on 2 June 2006, is a wiki-based website hosted by the Wikimedia Foundation. It serves as a platform where anyone can build up a community in a certain language edition of a Wikimedia project (Wikipedia, Wiktionary, Wikibooks, Wikinews, Wikiquote and Wikivoyage) that does not yet have its own sub-domain, provided that it is a recognized language.
This is where potential Wikimedia project Wikis in new language versions can be arranged, written, tested and proven worthy of being hosted by the Wikimedia Foundation.

mediawiki, a free software open source Wiki package, supporting all the Wikimedia projects https://www.mediawiki.org/wiki/MediaWiki
MediaWiki is free server-based software, licensed under the GNU General Public License (GPL). It’s designed to run on a large server farm for a website that gets millions of hits per day.

Debian, the universal operating system, aka the “Mother” of numerous children distributions https://www.debian.org/index.en.html
By the way, Debian provides more than a pure OS: it comes with over 43000 packages, precompiled software bundled up in a nice format for easy installation on your machine.
Debian is also a democratic community organization, which aims at the development of operating systems exclusively based on free software.

Emmabuntüs (http://www.emmabuntus.org) a distro for all seasons.
Emmabuntüs is a distribution designed to facilitate the refurbishing of computers given to humanitarian associations, in particular the Emmaüs community (http://www.emmaus-international.org/en/) (hence, the name of the distribution), to help the discovery of the GNU/Linux world by beginners, and limit the the electronic wastes generated by the hardware overconsumption, by extending the lifespan of aging computers.

Mageia (https://www.mageia.org) is a free operating system, based on GNU/Linux. It is a community project (https://www.mageia.org/en/community/), supported by an association law 1901 consisting of elected contributors.
The goal of Mageia: to make superb tools for people. Beyond a secure, stable and sustainable operating system for your computers, the goal is to establish stable and credible governance to coordinate collaborative projects.
Contributions are based on their own license (https://www.mageia.org/en/about/license/) and the community complies with a Code of Conduct (https://www.mageia.org/en/about/code-of-conduct).
Mageia has an active community and detailed documentation. https://www.mageia.org/en/support/

Fedora (https://getfedora.org/) is a polished, easy to use operating system for laptop and desktop computers, with a complete set of tools for developers and makers of all kinds.
Fedora comes with a “Server” release, a powerful, flexible operating system that includes the best and latest datacenter technologies. It puts you in control of all your infrastructure and services.

https://www.gnu.org/distros/free-distros.fr.html
This page lists the GNU/Linux distributions that are entirely free as in freedom.
The Free Software Foundation seems quite tough in what concerns the real freedom … But can we put the blame on an organization which is seeking a situation that should be commonplace.
Equivalence between proprietary software: A list of free alternatives proposing functionalities close to those of proprietary software, well established in their application domain. This list is far to be comprehensive, and does not have the goal to spotlight particular software, but rather to present different (proprietary or free) software within the same application domain. http://wiki.linuxquestions.org/wiki/Linux_software_equivalent_to_Windows_software
The Free Software Directory: FSD, or simply Directory is a project of the Free Software Foundation (FSF). We catalog useful free software that runs under free operating systems — particularly the GNU operating system and its GNU/Linux variants. https://directory.fsf.org/wiki/Main_Page
h.node: This project aims at the construction of a hardware database in order to identify what devices work with a fully free operating system. The h-node.org website is structured like a Wiki in which all the users can modify or insert new contents. The h-node project is developed in collaboration and as an activity of the Free Software Foundation (FSF).
https://h-node.org/home/index/en
 Glossary
Glossary=> With great power comes great responsibility…
The administrator is a person in the IT department who is responsible for managing the company server. He takes care of the system updates, verifies its proper functioning, creates new accounts, sets permissions and configures file sharing, emails, backups, security scheme …
On a computer for private use, the administrator is the one who has the system management rights: in this case, yourself.
ADSL means broadband Internet. ADSL (Asymmetric Digital Subscriber Line) is practically deployed throughout most of the industrial countries the French and allows you to take advantage of speeds up to 30 Megabits/s, which permits you to watch videos, download files and navigate the Web very easily.
ALSA (Advanced Linux Sound Architecture) is a Linux kernel module which gather the function of several different sound drivers into one. It is used to detect sound cards whatever they are; it is very popular and very efficient. It greatly simplifies the management of sound on Linux and is often updated.
Apt (Advanced Packaging Tool) is the Debian package manager using the .deb package formats. There are graphical interfaces like Synaptic or Adept for those who are not comfortable with the command lines in the the terminal window.
Aptitude is an alternative to Apt. It offers other options such as the construction of dependency tree, update of package status and many others. If Aptitude does not care about broken packages on your system, Aptitude will try to repair it during the next update or upgrade, by presenting alternative solutions as well as their consequences and let you decide what to do.
Finally, it is also interesting to see the behavior of Aptitude when removing software: it computes useless dependencies and deletes them. On the other end, Apt only does only what you clearly ask for.
The “at” symbol ‘@’ is the little “a” with a circle curling around it. It is used to form email addresses (eg user@isp.com). This symbol is not used in the web addresses, only for electronic mail.
An Audio format is a data format used to represent sounds, music and voices in digital form, with the purpose of either store or transport them.
Autonomy is the time that a battery enables a mobile unit to operate without having to be recharged by an electric outlet. The autonomy of a laptop is a few hours and that a mobile phone a few days in theory.
Computer name when it’s big and powerfull.
BIOS stands for Basic Input Output System. The BIOS is the software (firmware) embedded on the motherboard which allows you to perform basic tasks when you turn the computer on (eg read a sector of a hard disk).
This is the program that launches at startup, allowing the choice of booting the computer with one among several operating. The most popular, Lilo and Grub are usually installed in the MBR (Master Boot Record) or the GPT (GUID Partition Table) of the hard drive. Although Windows has a similar piece of software, it is more difficult to use, when implementing a dual-boot Linux/Windows (for example), than using Grub.
Software used to navigate the Web.
A bug is unwanted operation in a computer or a computer program. We are talking about bug when the software does not do what you asked, it stops or do something weird or shutdown…
The computer language (following the A and B languages) which has become one of the most widely used programming languages of all time.
An evolution of the C programing language. Warning: C+ does not exist!
Live chat rooms on the Internet are spaces where you share information via text with a group of other users. The ability to converse with multiple people in the same conversation differentiates chat rooms from instant messaging programs, which are more typically designed for one-to-one communication.
A click is the action of pressing and releasing (almost) immediately one of the mouse buttons. An unspecified “click” actually means a “left-click”.
Common type of architecture on the Internet and more generally in computer science: A server contains information, clients connect to it and submit a request. Corresponding treatments are performed by the server and the results are sent back and displayed on the client computer. The Web is a good example of client/server application.
Cloud computing is concept gaining wide acceptance: rather than installing a program on our computer, which is going to take some space, the current trend is to do the work online, without the need to download the software. This is a way to do office work with Google Docs without installing anything on the computer, a browser is enough.
to write a program, or to speak the “machine language” (no, it does not mean “make beep beep beep” …).
The source code is the text file written by the software developer, which can be understood by the compiler and transformed into a directly executable program. Some source codes are freely available to developers in particular in the context of free software.
Start a command that converts source code into an executable program.
Also named terminal, it is (or not) a graphical window giving access to the shell interpretor allowing you to type command lines to be executed.
Files sent by some websites and stored on your hard drive. On subsequent connections, your computer let the Web site retrieve data that you previously entered. Cookies can only be read by the website that issued them and may contain only data that the user voluntarily provided to the site, or that can be retrieved from the connection itself (source IP address, etc). They can not read the disc’s contents or contain an executable program. You can set your browser to reject cookies, but you lose an interesting usability (like storing your preferences or passwords).
Copy and paste represents the action to duplicate a file from one location to another. The file is cloned into a new destination. The copy-paste operation is done, for example, by right-clicking on a selection and choosing the “Copy” action, and then right-clicking in the destination folder and choosing the “Paste” action. The keyboard shortcuts for these two actions are the popular [Ctrl]+‘c’ and [Ctrl]+‘v’.
A program crashing under Unix has the effect of copying its entire memory contents into a file named “core”. Not a good news … but becoming seldom these days.
Cut and paste, moves a file without duplicating it: the file will no longer exists in its original location, but only in its destination. The keyboard shortcuts for these actions are [Ctrl]+X and [Ctrl]+V.
=> arrow, the movements of which you have a hard time to follow on the screen…
The cursor is following on the screen the movements of your mouse. Often symbolized by a slanted arrow cursor, it lets you point an element: an icon, a menu, a button to click on in order to activate a function.
=> The mommy of many distributions
Debian is a community and a democratic organization whose purpose is the development of operating systems based exclusively on free software.
Debian differs from most of the distributions based on it by its non-commercial nature and the cooperative governance of the association managing the distribution.
It is said that there is a dependency, when a package depends on another one to be installed and/or running.
In the Unix world, a DE is a set of programs that provide a user friendly graphical interface to the operating system. It usually consists of a window manager and a lot of software that fit well with the environment, first and foremost file managers, control panels, web browsers, text and image editors, games, and even office and messaging suites.
A device is a piece of hardware that is connected to a computer. USB key, keyboard, mouse, printer … are all devices.
A dialog box is a small window that appears when the system or an application wants you to make a choice. You must therefore read the message and click the button that corresponds to your choice (Yes or No, Save or Cancel, …).
Distribution is a GNU/Linux system with a collection of software, which forms a complete operating system, ranging from the command line up to the graphical environment. The goal is to put together a stable and coherent set of software aiming at a particular audience. Distribution provides different tools to easily obtain and install the software.
Some distributions are commercial, that is to say, manufactured and distributed by companies, which adhere, more or less, to the free software spirit. Others, only developed by volunteers, are completely free.
Drag and drop is the action of moving the cursor on an icon, pressing and holding a mouse button, moving the mouse cursor to another location, and then releasing the button: the selected files follows the mouse and moves directly into this new location.
An email can be written in plain text or in HTML format. In the HTML case, some text enrichments are possible (bold, color, image, tables) but some mail client software (increasingly rare) do not read messages in HTML format.
Ergonomics refers to the ease of handling, understanding and using an equipment (eg a phone, a software or a website). More ergonomic it is, and faster the end user will master it. An ergonomic system is intuitive.
A file manager or file browser is a computer program that provides an user interface to work with file systems. The most common operations performed on files or groups of files include creating, opening (e.g. viewing, playing, editing or printing), renaming, moving or copying, deleting and searching for files, as well as modifying file attributes, properties and file permissions. Folders and files may be displayed in a hierarchical tree based on their directory structures. Some file managers contain features inspired by web browsers, including forward and backward navigational buttons. Some file managers provide network connectivity.
A file system (FS) , represents the way data are organized in a disk partition. GNU/Linux has its own FS, called ext2, ext3, ext4, ReiserFS, btrfs … and handles a multitude of file systems from other architectures, including FAT , VFAT (ie FAT32), NTFS (DOS/Windows file systems), ISO 9660, etc.
A file system is called “journalized” when it keeps a record (log) of the operations being performed, and then saves them on the disk.
These types of file systems (for example ext3/4 or Reiserfs and also NTFS) are more tolerant to system crashes because they keep the system consistent (no need anymore to use fsck or scandisk at start-up).
The firewall is a software protection located at the entry point of a computer, or a local network, to prevent intrusions from the outside. It controls the inputs and outputs and transmits only the authorized signals.
A firmware is a program used to connect smart devices (hard drive, DVD burner, scanner, ADSL modem) to your computer. It is written in the language understood by the electronic device. We can compare the firmware of a device to the BIOS of a computer. It is responsible for initializing the device and then executes the commands received from more advanced programs.
A font represents a range of characters with a particular size, weight and style of a typeface.
It is often used in a figurative sense to designate a “branch” or a “differentiation” from a common root. It is often through this differentiation process that new Linux distributions emerge. More precisely the whole idea is to take a basic known kernel or program, to modify it according to some purpose and to redistribute it.
File Transfert Protocol. Protocol used to transfer files over the Internet. Also the name of the program implementing this protocol. It is necessary to have a specialized program for access the FTP servers (Example: Filezilla)
Although the word may have a broader connotation, a geek is a computer enthusiast, usually passionate about other subjects (Eg. science fiction) and generally curious. Geek does not mean technology obsessed: geek do not like to only use the technology, they love to understand how that works and they do have a critical mind.
The graphics card is a component of the central unit responsible for the on-screen display. Powerful graphics cards also handle the rendering of 3D displays (for video games). The main manufacturers of graphics cards are Nvidia and ATI.
The graphical user interface refers to how the software is presented on the screen to the user. It is the positioning of the elements: menus, buttons, features in the window. A well defined graphical interface is ergonomic and intuitive: designed in such a smart way that the user understands it immediately.
GNOME stands for GNU Network Object Model Environment. It is a user friendly free graphical environment which goal is to make the GNU operating system usage available to the greatest number of people. This interface is currently very popular on the GNU/Linux systems and runs also on most of the UNIX-like systems.
The GNU project (“GNU’s not Unix”) is a community initiated in 1983 by Richard Stallman to create a free alternative to the Unix operating system.
GNU is particularly known in the software world because it made major contributions such as the development of the GNU compiler collection (GCC), the improvements of existing Unix commands or the definition of the free GNU General Public License (GPL).
GNU has also worked on a kernel called HURD, but ultimately it is Linux which emerged and became the kernel enabling the usage of all the other bricks of the project.
An inelegant but effective solution to a computing problem. Sometime also called a workaround.
The hard (disk) drive is an important component of a computer. It is the computer shed, since its role is to store data. The hard drive contains partitions that contain your installed system and your personal data
=> note : Soft Drive does not exist …
The collection of physical elements that comprise a computer system (the beast, cards, chips, drives, processor, etc.), as opposed to the Software part.
High Definition is the successor of the television set as we knew it before. HDTV is a television system providing an audio quality and an image resolution which are substantially higher than that of standard-definition television. The difference is really obvious. Video games (PS3 and Xbox360) and Blu-Ray (successor to the DVD) also benefit from this technology. However you will need some money and compatible hardware to enjoy it (compatible HDTV set, HDMI cable, Blu-Ray player …).
HDMI stands for High-Definition Multimedia Interface. HDMI is a standard for connecting together High Definition devices. It is replacing the Scart socket. You can connect a Blu-Ray player for example to an HDTV with an HDMI cable, and even a PS3 or a Xbox 360.
An icon is a pictogram, accompanied by a name, representing an element: folder, file, software, shortcut … clicking on an icon will launch a predefined action: open the file, launch the software, display the content…
IM stands for Instant Messaging, and refers to a software where you can communicate directly (or chat) with friends and family, possibly share files, using the microphone to talk and the webcam to see each others. Unlike a chat, instant messaging lets you talk with some people of your contact list, and not just anyone on the web.
Internet includes all interconnected (wired and wireless) networks in the world and their associated websites. With an Internet access, you can access visit all the websites of the world in one click, listen to music, communicate, watch videos, learn … let it be from your computer, your tablet or your smart phone.
Inputs/Outputs (or I/O) characterize the exchange of information between the processor and its associated devices. In practice, within an operating system, the inputs are the keyboard, the mouse, the disks, the incoming data from the network. When the outputs are the screen, the disks, the printer, the outgoing data to the network etc …
Single address across the Internet network, to uniquely identify a machine. It is usually represented by a group of four numbers. If your computer is connected to the Internet, it has an IP address that is usually provided at the beginning of the connection by your Internet Service Provider (ISP).
Internet Service Providers which let you enjoy Internet. Each of them provides an interface allowing you to connect to the Internet, to have an unlimited land-line phone and even access to digital TV programs.
Internet Relay Chat. Discussion System in real time on the Internet. There are several IRC networks themselves divided into “channels” themes.
Multi-platform programming language by Sun. The principle is that a program written once in Java can run on any computer as long as it has the specific runtime environment called “Java Virtual Machine”. This converts Java virtual machine instructions into specific instructions to your computer while requiring it to meet certain safety rules.
Java programs can be embedded within web pages, and in that case they are executed while the container page is being displayed. They are named Applet.
You should be extremely careful, because Java applet can be used as malware on your computer.
graphics file format producing an impressive compression ratios compared to previously defined formats, but at the expense of image quality. Actually, he compression method is usually lossy, meaning that some original image information is lost and cannot be restored, possibly affecting image quality. The corresponding file extension is JPG.
The core of an operating system, or simply the kernel, is one (if not the most) important part of the system. It manages the computer resources and allows different components - hardware and software - to communicate with each other.
A keyboard shortcut is a combination of keys pressed simultaneously on the keyboard to perform a specific action on the computer. The most commonly used keyboard shortcuts are for saving ([Ctrl] + s), to copying ([Ctrl] + c), pasting ([Ctrl] + v), or closing a window ([Alt] + F4) …
The KISS principle, “Keep it Simple Stupid”, is a method which advocates seeking simplicity in design and avoiding unnecessary complexity. Example: Give me a KISS.
Run … very … slowly. Lagging like a snail.
A live CD (or a live USB key) is a bootable medium. The system starts booting the computer and then runs the OS without installation. It actually uses the volatile memory (RAM) to run, and does not affect the permanent memory (hard disk).
“Free Software” is a concept of free applications and operating systems, whose source codes are left open by the developers, in order for everybody to inspect and improve them. One example is the GNU/Linux initiative which regroups free and gratis operating systems like Debian, but also the LibreOffice suite, the free alternative to Microsoft™ Office, or Firefox and Chromium the free alternatives to Microsoft™ Internet Explorer.
Sentence used by the computer people to say that they still have 2 hours to finish (the time to compile, test, fix, compile, test, fix, compile …)
mail refers to a letter sent by Internet via email software (Eg. Icedove). The mails are free, usually limited to 10MB, which can be accompanied by attachments (images, documents …) and sent to recipient(s) (At :) and potentially people in copy (CC :). Unwanted mails are called junk or spam.
A memory card is a small device able to permanently store digital data, likewise a USB key. The memory card is intended to be plugged into digital cameras or camcorders. It can store photos and movies, and can be read back by computer featuring a memory card slot. Among the most popular formats, we find the MemoryStick card for Sony devices, and SD for most others. A recent memory card can store thousands of photos.
The motherboard is the main component of the CPU. Its role is to centralize and process all the data exchanged between the processor and the peripheral. The motherboard therefore manages the hard disk, the CD/DVD drive, the keyboard, the mouse, the network, the various USB ports …
Nolife is an insane geek or nerd so passionate by his computer activity that he:she spends all his time with his/her passion neglecting everything else and in consequence has no (or very few) social life. No comment …
The “Noob” term (derived from “newbie” or novice) refers to a computer novice. It is not necessarily a pejorative term.
The notification area is usually located at the right of the taskbar. You can usually find in there, the time, the network indicator, the sound volume. This is where the messages appear when the system has something to tell you (eg the battery is running empty, updates are available …)
This is the set of software that manages the computer hardware and provides common services for the application programs. By extension, it is also viewed as the main interface with the end users.
Some examples of operating systems : GNU/Linux, Windows, Mac OS X, FreeBSD.
Operating System.
A package manager is the software which installs, updates and uninstalls the system packages. On Debian, Synaptic is the graphical front-end of the APT Debian package manager.
To use certain media such as hard disks, we need to structure them, to break them down into rather large subsets: partitions. In turn, each partition is then structured as a separate file system. Spliting a hard drive into multiple partitions allows, for example, the coexistence, on the same disk, of two different operating systems like GNU/Linux and Windows, which use different file systems.
Phishing is a scam practice which tricks an user by sending him an email with a forged sender address and including a link to a fake website mimicking its bank site, or an e-commerce site, and asking him to update its information … If the user get trapped (or phished) then his sensitive information (private data, bank account details, …) can be used to evil ends.
a Pixel is the smallest controllable element of a picture represented on the screen. A pixel can display one color at a time. Thus the screen is composed with million of these pixels, spread in both directions (height and width), and they come together to form the screen image. A pixel is so small that you can barely see it with the naked eye. The more pixels compose an image and the sharper it is.
A plugin is a software component that adds a specific feature to an existing computer program. Allowing for example a web browser to read more image, video, animation or sounds formats. Sometimes also called “addon”.
PS/2 port represents a couple of plugs located in the rear of the system unit. The purple plug connects the keyboard, while the green one connects the mouse.
Having said that, we should mention that the PS/2 port not used very often and replaced by the universal USB ports. One of the big disadvantage of this port is that it is not a hotplug : a device connected after the computer startup won’t be recognized.
The processor, also named Central Processing Unit (CPU), is the electronic circuitry within a computer that carries out the instructions of a computer program by performing the basic arithmetic, logical, control and input/output (I/O) operations specified by the instructions.
In particular, it handles the data exchanges between the various components of the system (hard drive, memory, mouse, graphics card …) and performs all the computation needed to interact with the you through the data displayed on the screen.
There is also the Graphics Processor Unit (GPU) which is a special component of the graphics card which accelerates the creation of images in a frame buffer intended for output to a display.
Used in the sense of “waiting line”. For example different files to be printed are put first in the printer spooler queue.
Terminate the execution of a program. Example : give me a pay raise or a quit my job.
RAM stands for Random-Access Memory. It is the computer volatile data storage. Its major advantage is the speed at which one can read from or write to it, as opposed to other direct access data storage media where the time required to read and write data items varies, depending on their locations and/or some mechanical limitations such as the media rotation speeds and arm movement delays.
A right-click is the action of pressing and releasing (almost) immediately the mouse right button. A right-click will display a contextual menu corresponding to the pointed element. In particular, it allows to copy, move, delete and rename the pointed element when it is a file or a folder.
Means “Read The Fucking Manual”. This is an abbreviation that is thrown wildly at the head of someone who asks a question to encourage him to do first his home work in the documentation.
This is because people sometimes ask trivial questions, whose answers are readily available in the man pages or on the Internet, and often these people are not used to the power of the documentation in the Unix world.
A search engine is a large software system, hosted by a website and which is designed to search for information on the World Wide Web. It lets you ask questions or type key words to be searched for. The engine will then return the most relevant results.
A shortcut is an icon placed anywhere and providing a quick access to a software or a location on your computer. Most of the time a shortcut is used to launch a program. Deleting a shortcut does not uninstall the program it is associated with, and does not delete either the linked file.
Everything that makes a computer running, except the hardware part. Applications are software, for example.
Generally present in modern Internet browsers, tabs allow to browse multiple sites simultaneously. To switch from one site to another, you just have to click on its corresponding tab. Tabs are represented like tabs in a workbook.
We call a terminal, the command line console which is available and essential in all GNU/Linux distributions.
Even though many GUIs are available for virtually any application, nothing is more efficient, for example, than updating your entire system by typing single command line.
Note : a terminal is a very useful tool to debug a program.
In the world of Usenet, forums of all kinds, mailing lists, IRC, and all these places open to online discussions, a troll is a person who sows discord by starting arguments or upsetting people, by posting inflammatory, extraneous, or off-topic messages with the intent of provoking readers into an emotional response. By extension the subject of the argument itself.
Known examples : “GNU/Linux or Windows”, “Women in Free Software”.
For a desktop, the central unit is the box containing all the electronic equipment that allows the computer to operate. The Keyboard, mouse, monitor, speakers etc. are all connected to it. The hard disk drive is located in this central unit, for example.
For a laptop, there is no Central Unit. All the electronic components are grouped under the Keyboard.
Unix is a multitasking, multi-user computer OS. The original Unix system was developed in 1969. Several versions were created later on, and today, GNU/Linux is taking its inspiration from this family and continues with the same philosophy.
Unix systems are characterized by a modular design that is sometimes called the “Unix philosophy,” meaning that the OS provides a set of tools, each of which performing a well-defined function, and an unified file system to perform complex work-flows.
The main Unices are : the BSD family (NetBSD, FreeBSD, OpenBSD), AIX, Solaris, HP-UX, Mac Os X.
An update is a new version of a program that fix a problem existing in its the previous version. The update may fix a security hole, add a new functionality, solve an algorithm error …
The URL (Uniform Ressource Locator) points to the address of a website like “http://www.debian.org”. By typing an URL in the browser address bar, you go directly to the desired site, without having to go through a search engine. You never need to type the %%“http://www.”%% address header, simply enter “debian.org”.
USB stands for Universal Serial Bus. It is the cable with a rectangular connector that wants to be universal: almost all current hardware devices are connected to your computer via USB. Computers now have USB ports on the back, on the front of the Central Unit, and even sometimes on your monitor.
It usually requires 3 steps to plug an USB connector: try to plug in a first try, it does not work. Turn over the connector and retry, it does not work too. Retry with the initial position and the connector will be in. This is as mysterious as the sock which disappears in the washer…
It is the full set of the workspaces available on a GNU/Linux desktop. It is like having on hand several desktops (with task bar and included windows). Very handy to get organized !
Video Graphics Array (VGA) refers to the display hardware first introduced with the IBM PS/2 in 1987. The term can also mean either an analog computer display standard, the 15-pin D-subminiature VGA connector or the 640x480 resolution itself. While this resolution was superseded in the personal computer market in the 1990s, mobile devices have only caught up in the last few years.
Stands for Virtual Private Network, and refers to an encrypted network on the Internet, which allows a company whose premises are geographically dispersed to communicate and share documents in a completely secure manner, as if they were all connected in a local area network.
Web is the most common Internet network and refers to all the interconnected networks that run across the whole world and connect computers together in the manner of a spider web.
Surfing the Web means : browse the Internet.
An Internet browser is a software application that allows you to visit websites, download files and make some research.
A wiki (Hawaiian word meaning “quick”) is a web site whose pages are editable by visitors, enabling the creation of collaborative contents. (And aren’t you afraid to give the keys to strangers ?).
A window is a rectangular area that appears on the screen to display, for example, the contents of a folder, or a text file, or some software output. The window can take all the space (full-screen) or only a part of the screen real estate. It is possible to view multiple windows simultaneously and drag items from one to another using the drag and drop technique.
The window manager is the X (graphical) client software that controls the placement and appearance of windows (title bar, framing, moving, resizing, etc..) within a windowing system in a graphical user interface. Most window managers are designed to help provide a desktop environment.
Applications, handle the inside of the window they created and manage their content and the interaction with the user.
It is possible to change the window manager and see all the look and feel of the screen change completely.
When the window manager can do many other things in addition to what has been described here, it is a desktop environment like XFCE.
Initials of the World Wide Web.
X Window System, commonly called X Windows, X11 or just X is the graphics subsystem of GNU/Linux. X Window is not only a driver for the video card, it is mainly an interface (API) for applications, so that they appear on the screen and receive input from the keyboard and mouse.
Free X server used by GNU/Linux distributions.
Yes We can make you understand your computer, use it to do what you want and share knowledge…
“Stay zen”, means keep calm. Zen Buddhism has always been appreciated by hackers. This is a fundamental virtue of good programmer, especially in the debugging phase …
A very popular file compression format. Requires a specific program for decoding (expanding) the compressed file.
Program that ended but whose father, informed of its death, does nothing (in keeping with the quilt analogy, he is not concerned with the funeral and the administrative procedures). It does not exist anymore but is not deleted from the processus listr, so it is still a bit alive … A program whose father was destroyed in turn is an orphan.
 Sources & licenses
Sources & licensesSources of this manual are freely available on this server thebeginnershandbook-deb9-src.tar.gz
The various sources that helped me in the development of this manual:
The beginner’s handbook scribbled by 3hg team  https://3hg.fr under free license WTFPLv2
https://3hg.fr under free license WTFPLv2  (http://www.wtfpl.net) unless otherwise stated.
(http://www.wtfpl.net) unless otherwise stated.
This manual integrates logos (Debian, Firefox, etc.) under copyright (each one its own, otherwise it’s not funny) as well as some images and texts under license CC-BY-SA  (https://creativecommons.org/licenses/by-sa/3.0/) (specified and credited under images and texts Concerned)
(https://creativecommons.org/licenses/by-sa/3.0/) (specified and credited under images and texts Concerned)
The icons used come from themes Gnome:
https://commons.wikimedia.org/wiki/GNOME_Desktop_icons
& Tango: https://commons.wikimedia.org/wiki/Tango_icons
Debian : Copyright © 1997-2017 SPI (http://www.spi-inc.org/) and others; See license terms (https://www.debian.org/license)

Debian is a registered trademark (https://www.debian.org/trademark) of Software in the Public Interest, Inc.
First of all, a great Thanks to the Framasoft team  (https://framasoft.org) that hosts the sources of this project on framaGIT and the online public version.
(https://framasoft.org) that hosts the sources of this project on framaGIT and the online public version.
Thanks a lot to people who participated to the first “Jessie” release of the beginners handbook: bendia, nIQnutn, Atapaz, Severian, deuchdeb, martinux_qc, mercredi, nazmi, chalu, bruno-legrand, Thuban, Starsheep, arpinux, smolski, Trefix, desmoric, nono47, yanatoum, PengouinPdt, èfpé, fiche, BibiSky51, titiasam, Firepowi, dcpc007, rhyzome, Péhä, Caribou22.
For this Stretch release, thanks to BibiSky51 for its rereading and advices, to kyodev for gitpages initiation, to 3hg for work and support, to saby43 for the english translation and to my wife <3
Special thx 2 Péhä for his drawings (under CC-BY-SA) and his free spirit https://lesptitsdessinsdepeha.wordpress.com.